Patterns and Trends in Insider Threats Across Industry Sectors (Part 9 of 9: Insider Threats Across Industry Sectors)
In previous posts of our series analyzing and summarizing insider incidents across multiple sectors, we presented up-to-date statistics from the CERT National Insider Threat Center (NITC) Incident Corpus and looked closely at which types of insider incidents are prevalent within certain types of organizations. From there, we presented statistics on what types of assets those insider attacks target, the time frames associated with those attacks, and the tactics, techniques, and procedures the insiders used to carry them out. In this final post of the series, we summarize what we have learned or reinforced in these recent explorations of insider incidents across multiple industry sectors.
Same Incident Type, Different Sector, Different Attack Path?
Our analysis of the different insider threats across sectors clearly showed distinct patterns for the three types of insider crime we have examined in this series: fraud, intellectual property theft, and IT systems sabotage. However, each type of crime also tends to differ across sectors. For example, the data indicates that the most common target of insider fraud attacks in the healthcare industry is customer data, whereas money is the most common target of insider fraud in the finance and insurance sector.
What drives these differences between the patterns of the same types of attacks across different industry sectors? The answer is simple: what is important to the organization!
Organizations in different industry sectors have different missions, which are supported by different critical services, which are supported by different critical assets. This structure is the foundation of the CERT Resilience Management Model, a valuable resource for organizations looking for a maturity model for managing operational resilience that includes insider risk mitigation. Misuse of authorized access to critical assets occurs in every insider incident.
Insiders understand their organization's critical assets and how they are protected. Different targets of the same attack type will cause attackers to use different techniques, tactics, and procedures, which will in turn require the organization to adopt different controls. This finding remains the same today as it has since we began studying insider threats in 2001, and it is the reason the first recommended best practice in our Common Sense Guide to Mitigating Insider Threats, Sixth Edition is "Know and protect your critical assets."
Trusted Business Partners Are a Consistent Risk
All industry sectors have consistently experienced insider incidents committed by trusted business partners--any individuals an organization has contracted to perform a service. As indicated in the figure below, the percentage of insider incidents perpetrated by trusted business partners has typically ranged between 15% and 25% across all insider incident types and industry sectors in our insider incident corpus.
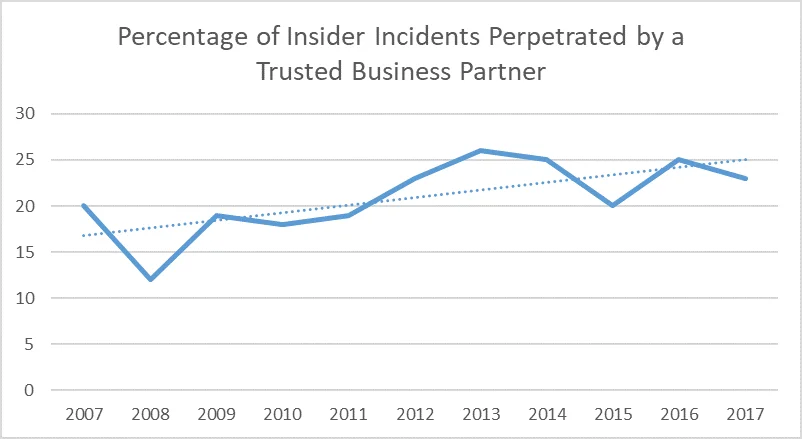
There is some variance in the prevalence of insider incidents perpetrated by trusted business partners across industry sectors:
- Finance and Insurance: 38%
- Health Care: 18%
- Information Technology: 22%
- Federal Government: 31%
- State and Local Government: 16%
- Entertainment: 30%
We hypothesize that this variance can primarily be attributed to differences among the prevalence of using trusted business partners in different industry sectors. Organizations should take special care to ensure the same protections are in place for trusted business partners as for employees. Trusted business partners have the same access to your critical assets as employees and, in turn, have misused that access to harm victim organizations in the past. Ensuring consistent coverage of technical and administrative controls for trusted business partners and employees can be a challenge for organizations, particularly for small businesses. However, it is vital, as research suggests that small businesses are increasing their use of trusted business partners.
Contractual agreements with trusted business partners should include requirements for insider threat safeguards and protections that meet the standards of your organization. Special care should be taken to require the timely sharing of information that the contracting organization can use to proactively identify concerning behaviors or issues. For more on how to address this concern, see Best Practice 6, "Consider threats from insiders and business partners in enterprise-wide risk assessments," of the Common Sense Guide to Mitigating Insider Threats, Sixth Edition.
Start with Your Data
The data presented in this blog series is a great way for organizations to begin using empirical data to drive their insider risk mitigation strategies. As you have seen, your organization's critical assets will drive its insider risk and how insiders misuse their access.
We recommend that organizations collect and analyze their own insider incident data using collection and analysis techniques similar to those we have used in this blog series. Studying your own incident data can help your organization understand the concerning behaviors and activity that precede insider attacks. This knowledge can enable your organization to consider tailored administrative controls to proactively deploy to help prevent future incidents.
When deploying preventive insider threat controls, organizations should consider a balanced approach that uses positive incentives, which can reduce the organization's insider risk by managing employees' unmet expectations, defusing conflicts between coworkers before tensions escalate, and managing stressed employees' workloads.
Looking Ahead
The insider threat landscape is constantly evolving. When organizations create new types of assets, new risks involving the misuse of authorized access to those assets may be identified, and new attacker methods are sure to follow.
As sociotechnical and organizational factors continue to influence insider risk, we continue to refine our insider incident data collection and analysis methods. We will continue to update you with our new statistics, collect and analyze incident data, and encourage you to do the same within your own organization.
As always, if you found this blog series useful, or if you have a suggestion for another blog post or series, please contact us at insider-threat-feedback@cert.org.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
- Part 9: Patterns and Trends in Insider Threats Across Industry Sectors
More By The Author
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
