Insider Threats in the Federal Government (Part 3 of 9: Insider Threats Across Industry Sectors)
The CERT National Insider Threat Center (NITC) Insider Threat Incident Corpus contains over 2,000 incidents, which, as Director Randy Trzeciak writes, acts as the "foundation for our empirical research and analysis." This vast data set shows us that insider incidents impact both the public and private sector, with federal government organizations being no exception. As Carrie Gardner introduced in the previous blog post in this series, federal government organizations fall under the NAICS Codes for the public administration category. Public administration, in this context, refers to a collection of organizations working primarily for the public benefit, including within national security. This blog post will cover insider incidents within federal government, specifically malicious, non-espionage incidents.
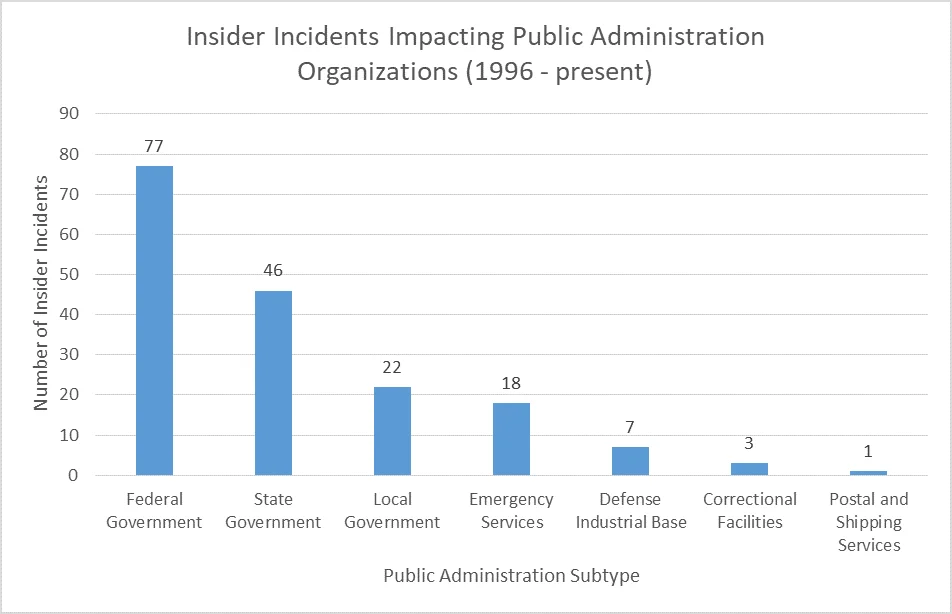
In part, the focus of this blog post is due to the high representation of federal government incidents within public administration, as can be seen in the chart above. The potential impact of insider incidents in federal government is greater with regard to national security. As such, federal government organizations are mandated by Executive Order 13587 to implement insider threat programs. While this requirement also applies to organizations within the defense industrial base per NISPOM Change 2, the mandate and NISPOM do not extend to state/local government and nonprofits. Since federal government organizations are under mandate to detect insider threats, it follows that more would be detected and eventually prosecuted than in other Public Administration organizations. Additional information on state and local government insider threat incidents will be featured in a future post.
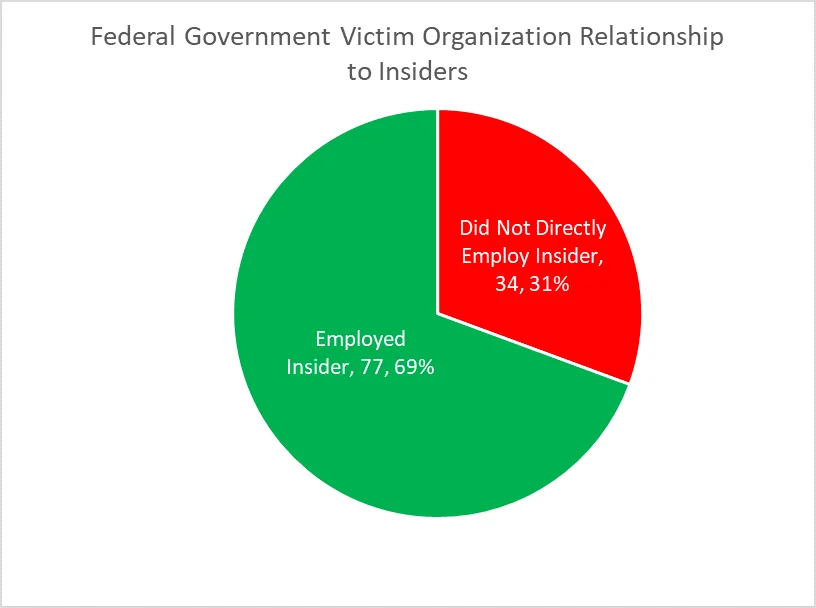
In total, we identified 77 non-espionage insider incidents where a federal government organization was both the victim organization and the direct employer. However, there were 34 additional incidents where a federal organization was impacted by an insider incident at another organization. By and large, these were incidents where a federal government organization had employed a consultant or contractor. These incidents also included an instance where a federal agency was indirectly victimized in the course of a Stolen Identity Refund Fraud (SIRF) scheme and another incident where a federal employee of another agency had authorized access to the victim organization's IT systems. Though organizations may understandably not consider a SIRF incident by external actors as an insider threat, they may consider any individuals that have hands-on, authorized access to their systems as insiders and pose a threat - even if they are employed elsewhere in government. In general, we advocate for identifying threats by trusted business partners in enterprise-wide risk assessments. While we wanted to give some context regarding these kinds of incidents, a deep dive into these incidents is beyond the scope of this blog post.
Insider incidents in the federal government rarely include IT Sabotage or Theft of Intellectual Property (IP). In part due to the nature of the federal and national security operating environment, so few cases are categorized as IT Sabotage or Theft of IP because incidents involving classified information are typically considered (or prosecuted as) national security espionage.
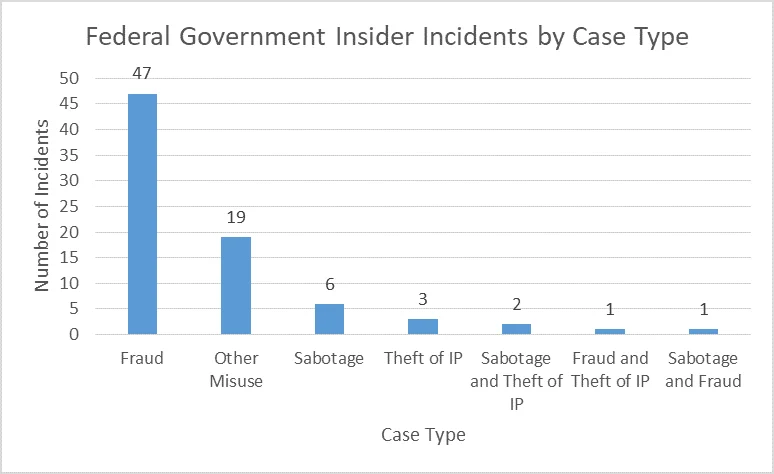
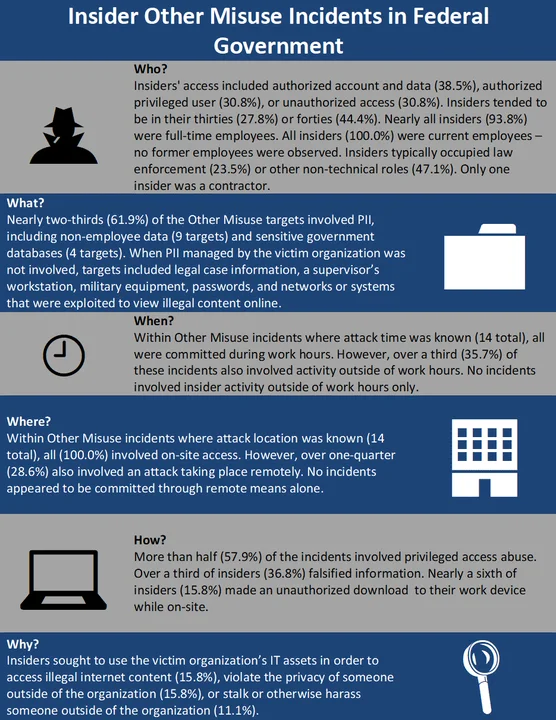
Given how few reported incidents involved IT Sabotage or Theft of IP, the following analyses focuses on incidents of Fraud and "Other Misuse". Incidents of Other Misuse by insiders can be described as those incidents that involve the unauthorized use of organizational devices, networks, and resources that are not better classified as Theft of IP, IT Sabotage, or Fraud. Representative examples of Other Misuse include the use of organizational resources for personal benefit, to violate the privacy of other individuals (e.g., obtaining access to colleagues' emails without consent or a proper business purpose) or to commit another kind of cyber-related crime (e.g., stalking or purchasing drugs), which in turn violate organizational policies.
Sector Characteristics
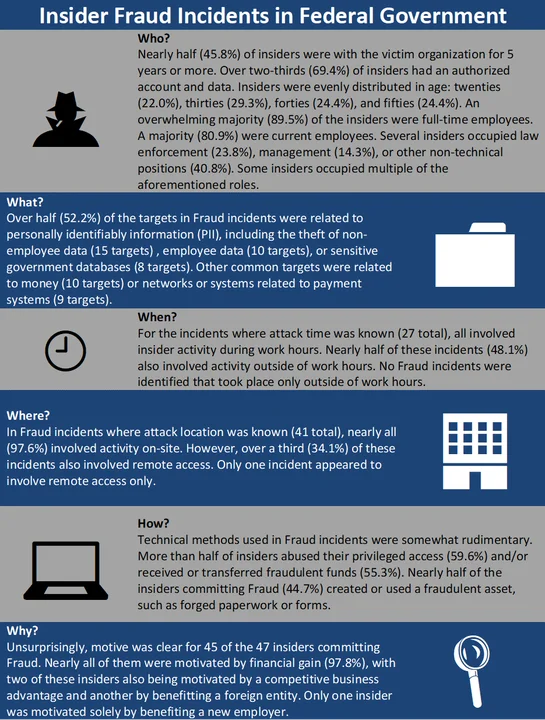
Over half (60.8%) of incidents impacting federal organizations involved Fraud. In theory, this is not necessarily surprising given the well-documented efforts to combat issues of fraud, waste, abuse, and mismanagement of federal funds. To that end, the Insider Threat Incident Corpus reflects those efforts. The Fraud statistics include only incidents where no other incident type was known and, for each attribute (i.e., Who, What, When, Where, How, Why), take into account only cases where that attribute was known.
Other Misuse was the second-most common form of insider threat in federal government. These incidents generally involved insiders abusing access to devices or systems for reasons not including financial gain (often the case in Fraud or Theft of IP) or revenge (typical in IT Sabotage). While these incidents are not typically related to an immediate loss of revenue or system availability, they have potential to cause reputational damage to or generate liability concerns for an organization.
Analysis
Insiders committing Fraud in federal government tended to be in trusted positions and committed the incident during working hours. In federal government Fraud incidents where the financial impact was known (44total), the median financial impact was between $75,712and $317,551. Overall, in federal government insider incidents where impact was known (64 total), the median impact was between $0,000 and $144,195. For comparison, the median financial impact of a domestic insider threat incident - across all industries within the CERT Insider Threat Incident Corpus where financial impact is known - is between $95,200 and $257,500. Three Fraud incidents (9.4%) had a financial impact of $1 million or more.
Perhaps the most notable feature of insider incidents within federal government was how prevalent incidents of Other Misuse were compared to other sectors. Although one-third (33.3%) of the Other Misuse incidents in the CERT NITC Insider Threat Incident Corpus took place in federal government organizations, federal government incidents as a whole represent only about 8.0% of the malicious, non-espionage corpus. Insiders committing Other Misuse generally did so in the furtherance of an additional crime (e.g., stalking an individual using employer-owned information systems), which made motive clear in all but one incident. Given the small sample size of insiders committing Other Misuse (19), claims cannot yet be made about the significance of any of the patterns or statistics described above. Indeed, Other Misuse incidents may be composites of other distinct incident patterns and the technical methods used simply reflect that. Financial impact was unknown in most (84.2%) incidents of Other Misuse. Of course, insider incidents can have more than just a financial impact. For instances where an insider was stalking an individual, that could have resulted in a real compromise of a victim's personal safety. In at least one of these incidents, in an instance where the insider had access to medical records, the insider's actions delayed the delivery of vital healthcare.
Final Thoughts
Although not every insider incident impacting the federal government will be at the level of national security espionage, incidents are still worthy of attention and study. Looking at these insider incidents - where for instance the cleared employees are the most vetted, are the most trusted, and have among the most sensitive access to information - we can glean insights into cybersecurity best practices to mitigate insider threat, including the importance of being attuned to employee behavior. Organizations in all industries can (re)consider to whom they give access to information that can be used to harm the organization directly, vis-Ã -vis fraud, or indirectly by violating the privacy and safety of third parties. Overall, these incidents underscore the need for robust auditing functionality to identify when previously "good" employees start to go "bad."
Stay tuned for the next post, in which we spotlight the Financial Services sector, or subscribe to a feed of the Insider Threat blog to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, or to provide feedback, please contact insider-threat-feedback@cert.org.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
More By The Authors
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed



