CERT Releases 2 Tools to Assess Insider Risk
According to a 2023 Ponemon study, the number of reported insider risk incidents and the costs associated with them continues to rise. With more than 7,000 reported cases in 2023, the average insider risk incident cost organizations over $600,000. To help organizations assess their insider risk programs and identify potential vulnerabilities that could result in insider threats, the SEI CERT Division has released two tools available for download on its website. Previously available only to licensed partners, the Insider Threat Vulnerability Assessment (ITVA) and Insider Threat Program Evaluation (ITPE) toolkits provide practical methods to assess your organization’s ability to manage insider risk. This post describes the purpose and use of the toolkits, with a focus on the workbook components of the toolkits that are the primary methods of program assessment.
The ITVA and ITPE Toolkits
The lITVA and ITPE toolkits are intended to assess distinct areas of an insider risk program. The ITVA toolkit helps programs assess their capacity to prevent, detect, and respond to threats to an organization's critical assets and processes, and is derived from vulnerabilities coded in the CERT insider threat case corpus. The ITPE toolkit evaluates the components of an insider risk program at an enterprise level. It benchmarks them against National Insider Threat Task Force (NITTF) standards along with CERT best practices. Each toolkit includes several workbooks and a variety of useful content to help facilitate insider risk program assessments, including interview and logistics guidance, pre-assessment information collection worksheets, and participant briefing templates.
The Workbooks
The workbooks included with each toolkit are the primary methods of assessment. The workbooks are organized by the functional area that they assess, and utilize the Goals, Questions, Indicators, and Measures (GQIM) framework to measure effectiveness. The tables below show the names of the workbooks for the ITVA and ITPE (in bold), as well as their respective capability areas:
Insider Threat Program Evaluation (ITPE) Workbooks
As shown in Figure 1 below, ITPE is organized by three functional area workbooks: Program Management, Personnel and Training, and Data Collection and Analysis. Each workbook is broken down into individual capability areas.
|
Program Management |
Personnel and Training |
Data Collection and Analysis |
|
Formalized Program |
Organization-Wide Participation |
Executing Response |
|
InTP Policy |
InTP Team Composition |
Information Access Management |
|
Insider Threat Response Plan |
Insider Threat Awareness Training for the Organization |
InTP Access to Technical Information |
|
InTP Communication Plan |
InTP Team Training |
InTP Access to HR Information |
|
ERM Integration |
Role-Based Training for the Organization |
InTP Access to Counterintelligence and Security Information |
|
Critical Asset Identification |
Manager and Supervisor Training |
User Activity Monitoring |
|
InTP Governance |
Employee Onboarding Process |
Integrated Data Analytical Capability |
|
Quality, Effectiveness, and Performance of the InTP |
InTP Access to HR Information |
|
|
Employee Investigations |
Employee Behavior |
|
|
Employee Support Programs |
Employee Separation |
Figure 1: The Insider Threat Program Evaluation (ITPE) is organized by three functional area workbooks: Program Management, Personnel and Training, and Data Collection and Analysis.
Insider Threat Vulnerability Assessment (ITVA) Workbooks
Similar to the ITPE workbooks, the ITVA workbooks are named after seven functional areas: Data Owners, Human Resources, Information Technology, Legal, Physical Security, Software Engineering, and Trusted Business Partners (Figure 2). Each workbook is broken down into individual capability areas.
|
Data Owners |
Human Resources |
Information Technology |
Legal |
Physical Security |
Software Engineering |
Trusted Business Partners |
|
Access Control |
Recruitment |
Access Control |
Agreements to Protect Sensitive Information |
Facility Security |
Technical Policies and Agreements |
Screening/Hiring of Applicants |
|
Modification of Data, Systems, or Logs |
Policies and Practices |
Modification of Data or Disruption of Services or Systems |
Restrictions on Outside Employment |
Physical Asset Security |
Modification of Data or Systems |
Management of Business Partners |
|
Unauthorized Access, Download, or Transfer of Assets |
Training and Education, Evaluation |
Unauthorized Access, Download, or Transfer of Assets |
Employee Behaviors in the Workplace |
Asset Management |
Asset Management |
|
|
Incident Response |
Policy and Practice Monitoring and Enforcement Programs |
Detection and Identification |
Conditions of Hire |
Incident Response |
||
|
Termination |
Enforcement and Termination |
Incident Response |
Property Lending Agreements |
Contractor/ Business Partner Agreements |
||
|
Termination |
Contractor/ Business Partner Agreements |
Figure 2: The Insider Threat Vulnerability Assessment (ITVA) is organized by seven functional area workbooks: Data Owners, Human Resources, Information Technology, Legal, Physical Security, Software Engineering, and Trusted Business Partners.
Workbook Scoring Methodology
As mentioned above, each workbook in the ITVA and ITPE toolkits is descomposed into functional areas and their individual capabilities. These capabilities are defined as a designated activity, process, policy, or responsibility considered good practice or a requirement for an insider threat program. For instance, the Information Technology workbook has seven capabilities that will be assessed: Access Control, Modification of Data or Disruption of Services or Systems, Unauthorized Access, Download, or Transfer of Assets, Detection and Identification, Incident Response, and Termination
Each capability uses several indicators to determine whether the relevant activities are performed. Indicators are individual questions related to controls, practices, processes, or other activities that must be answered and substantiated (via interviews, observations, or document review) to determine capability scoring levels. A capability is scored based on the indicator level achieved. Figure 3 shows the relationship between workbooks, capabilities, and indicators/indicator scoring levels.
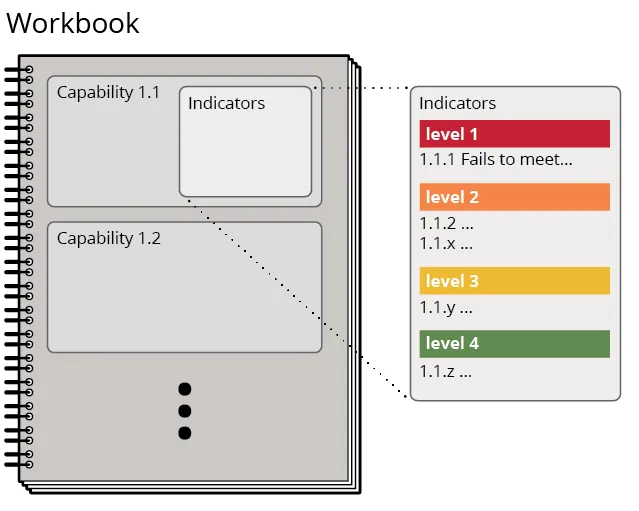
Figure 4 below describes the scoring level definitions used by the ITVA and ITPE.
| ITVA | ITPE | ||
| Level | Definition | Level | Definition |
| 1: Not Performed | There is a failure in an organization’s ability to meet the capability. The organization is not prepared to perform this capability. | 1: Not Performed | There is a failure of the organization to fully perform this capability. One or more of the Level 2: Core indicators are not being performed. |
| 2: Core | The organization has minimal controls and processes in place. The organization is prepared to Detect but has issues Preventing or Responding to the issue of concern. | 2: Core | The organization performs all the minimal set of practices as required by the NITTF. All the Level 2 Core indicators are performed. One or more indicators (but not all) at levels 3 and 4 may also be performed. |
| 3: Enhanced | The organization has adequate controls and processes in place. The organization is prepared to Detect and Respond but has issues Preventing the issue of concern. | 3: Enhanced | The organization has additional practices beyond what is required by NITTF to manage insider threats to improve efficiency and functionality. All the indicators at levels 2 and 3 are performed. Some (but not all) of the indicators at level 4: Robust may also be performed. |
| 4: Robust | The organization has exceptional controls and policies in place. The organization is prepared to Prevent/Detect/Respond to the issue of concern. | 4: Robust | The organization has extensive practices for the effective, efficient, and sustained management of insider threats. All the indicators at levels 2, 3, and 4 are performed. |
Figure 4: Scoring level definitions used by the ITVA and ITPE.
Scoring Example
Capability scores are attained by evaluating the indicators at each level. Level scores can then be compiled to provide overall scoring for the workbook. The following are example indicators from the Access Control/Expired Accounts capability in the Information Technology workbook. Note the different indicators and substantiation requirements for each of the four levels.


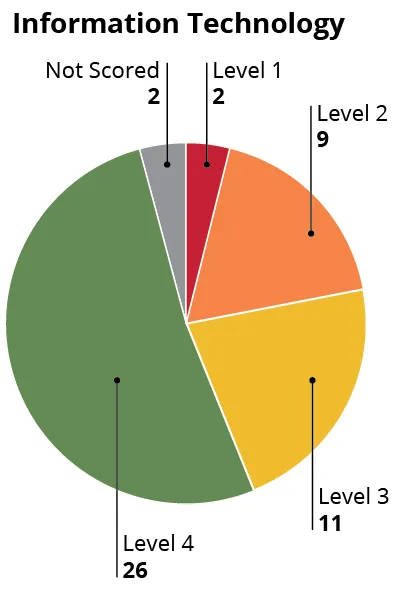
After all capabilities are scored, cumulative workbook scoring can be produced. The circle graph in Figure 6 below is an example visualization of capability scoring from the Information Technology workbook in the ITVA. The Information Technology workbook contains 50 capabilities and more than 300 indicators. The scoring levels are represented by color, along with the number of capabilities at each scoring level. While twenty-six of the capabilities are scored as Level 4 “robust,” three function at an “enhanced” Level 3, nine are at a “core” Level 2, and two capabilities are Level 1 “not performed.” Detailed workbook capability scoring allows organizations to drill down to specific indicators and distinctly identify strengths and weaknesses of their program, reveal potential gaps in processes and procedures, and provides a baseline for future assessments.
Additional Workbook Content
The ITVA and ITPE workbooks also include additional sections to help assessment teams understand capabilities and assist with assessment activities:
- Clarification/Intent provides easy-to-understand explanations of the workbook capabilities and their intended purpose.
- Assessment Team Guidance offers detailed direction from CERT to help assessment teams evaluate the workbook capabilities.
- Organization Response, Evidence Sought, Additional Information outlines additional workbook fields used by the assessment team to document the various assessment data collected.
Insider Risk-Measures of Effectiveness (IRM-MOE)
For organizations looking for detailed guidance on the use of the ITVA and ITPE toolkits, CERT’s new IRM-MOE course offers instruction and assistance with different ways to assess your insider risk program. This three-day course covers using the ITVA and ITPE toolkits, and also reviews CISA’s Insider Risk Mitigation Program Evaluation (IRMPE) instrument. The IRMPE is a lightweight tool with built-in reporting used to help evaluate your insider risk program. The tool is easy to use, and can typically be completed in under 4 hours. In addition, the IRM-MOE course provides instruction for metric development using the Goal-Question-Indicator-Measure (GQIM) framework. This framework enables insider risk programs to create custom metrics based on their organization’s criteria.
Toolkits Add Value to Your Insider Risk Program
The ITVA and ITPE toolkits can be valuable assets to your insider risk program. The accompanying ITVA and ITPE workbooks help organizations assess their insider risk programs and identify potential vulnerabilities associated with insider risk behavior. Using the toolkits as part of your program’s routine assessment procedures can help align your program with best practices and NITTF standards, identify potential vulnerabilities, and produce scoring to benchmark your program’s progress.
Additional Resources
The ITVA and ITPE insider risk tools can be downloaded for free from the SEI website
Insider Threat Vulnerability Assessment (ITVA)
Insider Threat Program Evaluation
For organizations looking for further guidance with assessing and improving their insider risk program, CERT offers the Insider Risk Management: Measures of Effectiveness (IRM-MoE) course. This three-day class details how to use the ITVA, ITPE, and IRMPE toolkits and offers in-depth instruction on assessment planning, custom metric development, and report writing.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
