Insider Threats in Information Technology (Part 6 of 9: Insider Threats Across Industry Sectors)
PUBLISHED IN
Insider ThreatAs Carrie Gardner wrote in the second blog post in this series, which introduced the Industry Sector Taxonomy, information technology (IT) organizations fall in the NAICS Code category professional, scientific, and technology. IT organizations develop products and perform services advancing the state of the art in technology applications. In many cases, these services directly impact the supply chain since many organizations rely on products and services from other organizations to perform and carry out their own business goals. This post covers insider incidents in the IT sector and focuses mainly on malicious, non-espionage incidents.
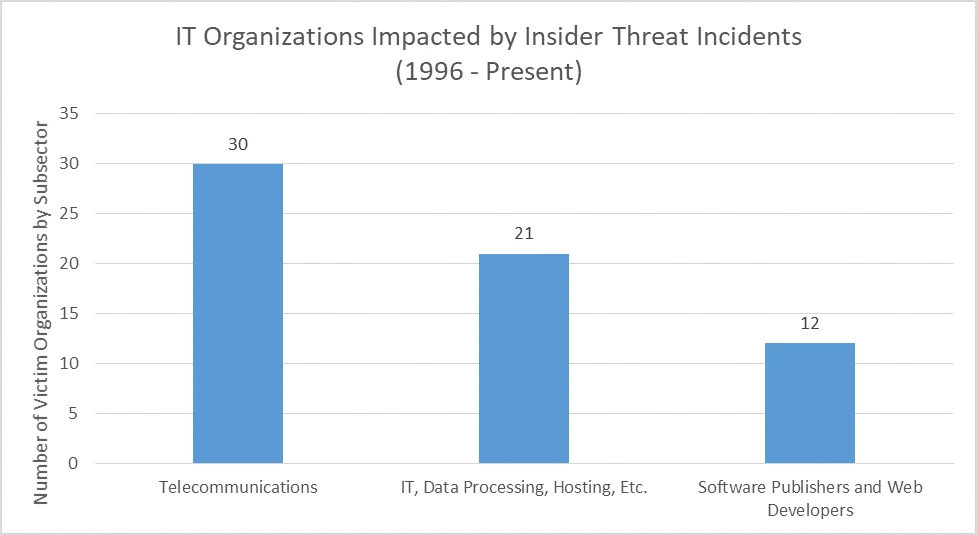
The CERT Insider Threat Incident Corpus has 60 incidents in Information Technology, with 631 victim organizations spread across three main subsector spaces: Telecommunications, IT Data Processing, and Application Developers. Telecommunications organizations account for the majority of insider incidents in the CERT Insider Incident Corpus. One specific example of a telecommunications incident involves a contractor working for an Internet service provider (ISP) where the insider committed Sabotage by gaining administrator access and disabling the Internet connection to all customers for almost three weeks, costing the victim organization more than $65,000 to fix.
Federal mandates put forth by EO 13587 and NISPOM Change 2 require DoD, USG, LE, and Defense Contractors with access to or who handle classified information to have insider threat programs that involve monitoring of IT systems for threats such as data exfiltration and sabotage. The absence of similar federal mandates for the non cleared private sector leaves many organizations, including those in IT, without insider threat programs or insider threat security controls. These organizations may be more susceptible to insider attacks. This situation could lead to incidents not being detected simply because of a lack of security awareness training about insider threats and their impacts.
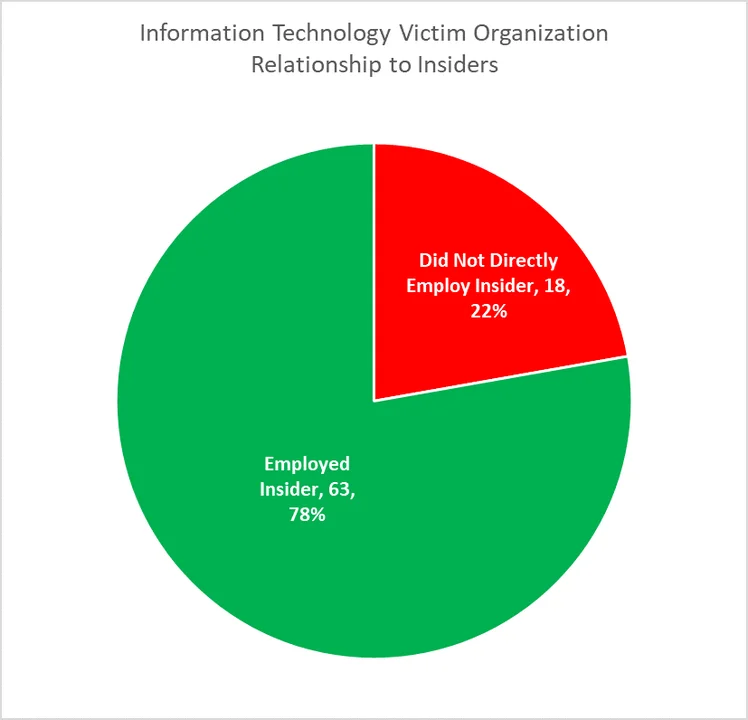
Of the 60 IT insider incidents, we identified 81 organizations impacted by those incidents, of which 63 (78%) organizations were both the direct victim and the direct employer of the insider. The remaining 18 (22%) organizations involved trusted business partner relationships in which an insider was a contractor or had non-regular full-time employement with the victim organization.
Insider incidents in the IT sector included IT Sabotage (36.67%), Fraud (21.67%), and Theft of IP (16.67%).
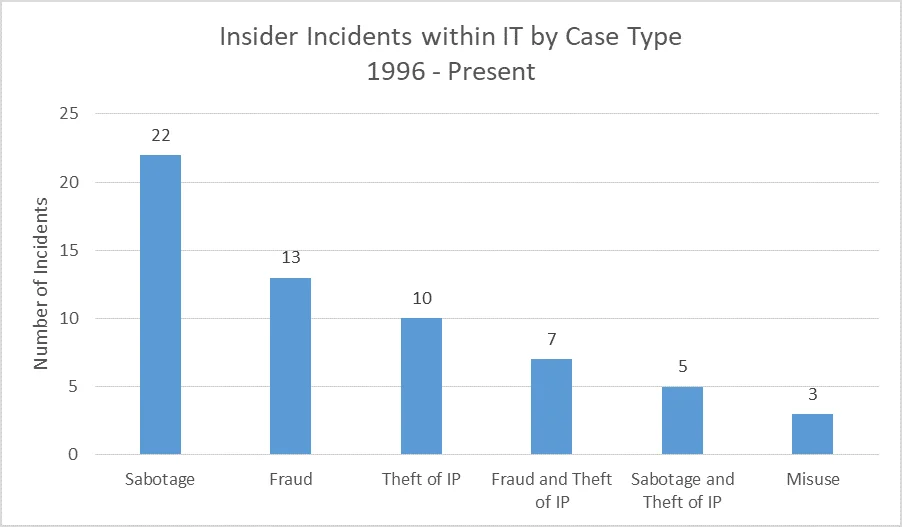
The remaining analysis will focus on Sabotage, the incident type of greatest number.
Sector Characteristics
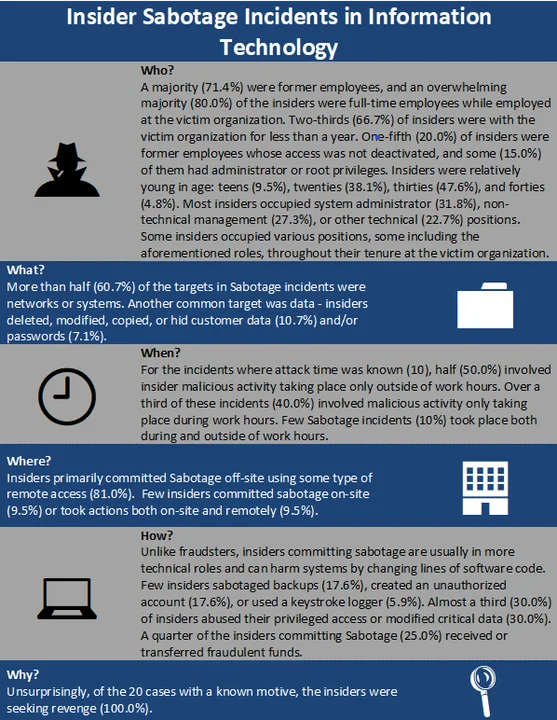
Over one third (36.67%) of incidents impacting IT organizations involved Sabotage. The statistics below include only incidents where the case type was solely Sabotage (22 incidents). Each attribute (i.e., Who, What, When, Where, How, Why) considers only cases where that attribute was known.
Analysis
Insiders committing Sabotage in the IT sector tended to be in high-trust IT positions, such as those with administrator-level access and permissions. These insiders typically committed the incident outside of typical working hours. In insider Sabotage incidents where the financial impact was known and the victim organization directly employed the insider (17), the median financial impact was between $10,000 and $20,000. Overall, in IT insider incidents and all evaluated incident types, where impact was known (63 total), the median impact was between $5,000 and $26,000. For comparison, the median financial impact of a domestic, malicious insider threat incident--across all industries within the CERT Insider Threat Incident Corpus where financial impact is known--is between $95,200 and $257,500. Six Sabotage incidents (9.5%) occurring within the IT sector had a financial impact of $1 million or more.
Final Thoughts
Reliance on the supply chain within the IT sector is growing rapidly, particularly in today's popular business models. When looking at IT Sabotoge incidents, most incidents were conducted by employees who had the greatest privilege and trust, which is why the CERT Division's Common Sense Guide to Mitigating Insider Threats (CSG), Fifth Edition recommends creating separation of duties and granting least privileges.
By thoroughly understanding motives and implementing effective behavioral and techncial monitoring strategies, organizations can better prevent, detect, and respond to insider incidents, including Sabotage. The cases of Sabotage in the IT sector tell us that former employees possess potentially damaging knowledge to do devastating harm. Some may retain access to an organization's systems, and some may be motivated to seek revenge, a known factor in these incidents. Best practice 20 of the Common Sense Guide referenced above recommends that organizations implement better practices and procedures for employee separation and disabling access to organizational systems.
Stay tuned for the next post, which will spotlight the Healthcare Services sector, or subscribe to a feed of the Insider Threat blog to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, or to provide feedback, please contact insider-threat-feedback@cert.org.
1 For some events, there is a one-to-many mapping for incidents to many victimized organizations that directly employed the insider.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
More By The Authors
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


