Insider Threats in State and Local Government (Part 5 of 9: Insider Threats Across Industry Sectors)
PUBLISHED IN
Insider ThreatContinuing our industry sector series, this blog post highlights insider threat trends in the State and Local Government subsector and explores distinct characteristics of fraud, the most common insider case type in the CERT Insider Threat Corpus for this subsector.
State and local governments, including emergency services, make up nearly half of the collected public administration insider incidents. Unlike the Federal Government subsector, there is no national requirement for state and local government organizations to have an insider threat mitigation capability.
Only 19 states require by statute that their state-run institutions maintain some level of cybersecurity readiness to protect their sensitive data. These statutes generally prescribe that state institutions implement and maintain security practices and procedures for data protection. Some of these state measures additionally mandate periodic security audits or employee awareness training. While these measures seem to be a good-faith effort to support information assurance, none of the statutes specifically acknowledge or address threats from authorized users--insider threats.
Some of the state and local government organizations that are victims of insider incidents include state departments of motor vehicles, courts, police departments, and health care programs. The graph below lists the breakdown of the 87 cases in the State and Local Government subsector in which organizations were direct victims of an insider threat attack.
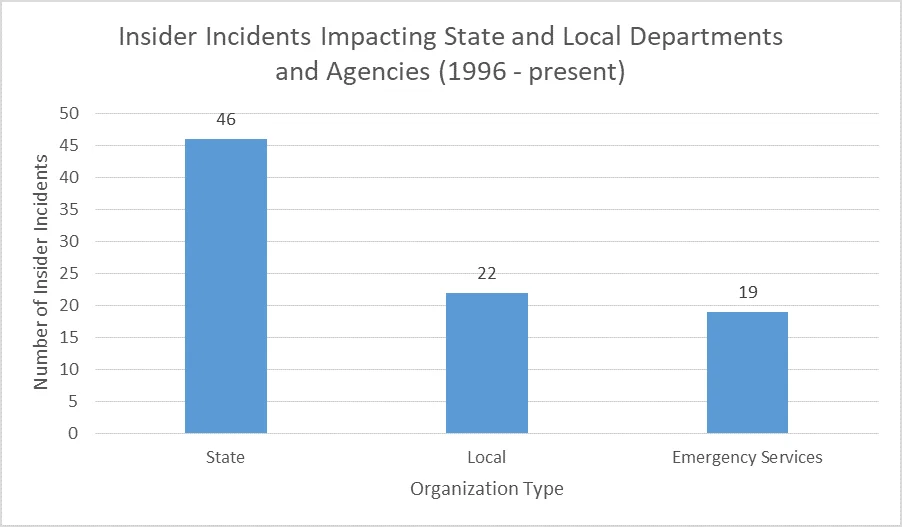
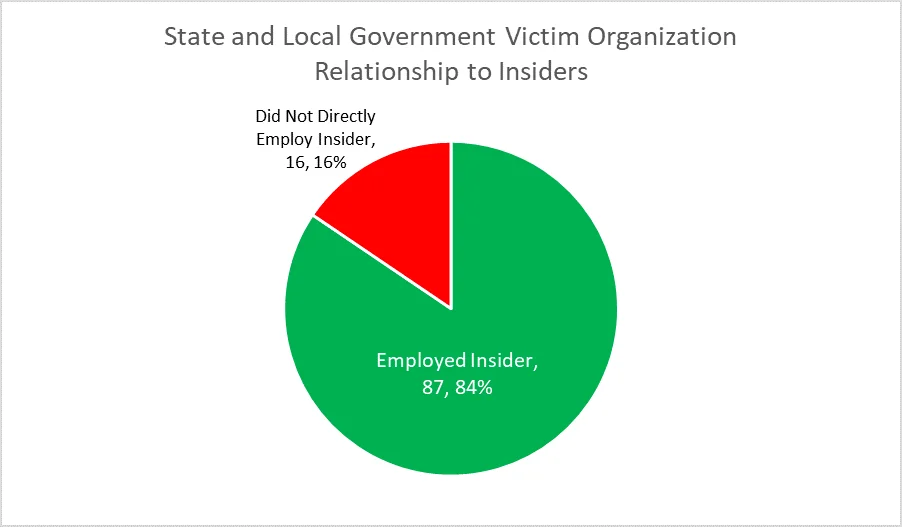
In addition to the 87 incidents where the organizations involved directly employed the insider, we identified 16 cases where there was an incident in the State and Local Government subsector involving a Trusted Business Parter (e.g., contractors or temporary employees).
Sector Overview
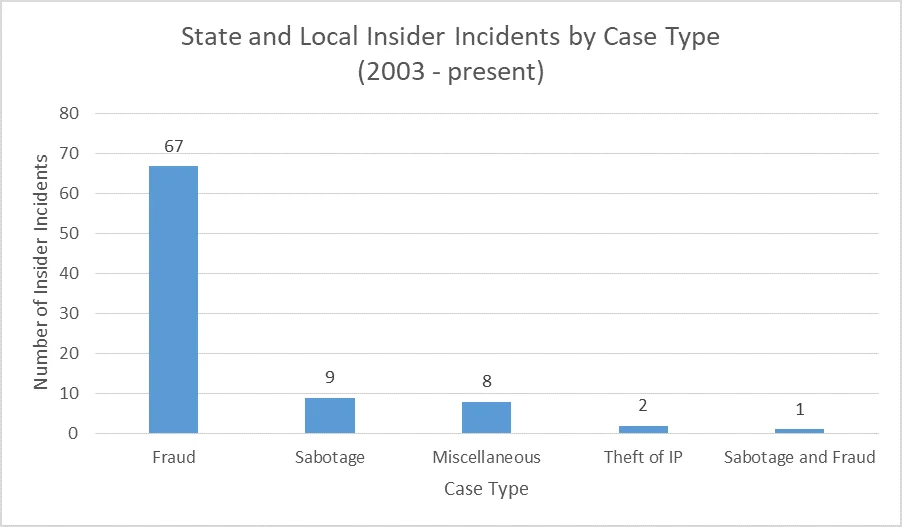
The most frequent insider incident case type in the State and Local Government subsector is fraud, occurring in 77% of incidents. These findings are consistent with findings in the Federal Government subsector of public administration. In these fraud incidents, we see insiders with access to sensitive data, such as personally identifiable information (PII), attempting to illegally profit by selling the data or their authorization to handle sensitive data or systems.
For example, a Department of Motor Vehicles (DMV) clerk misused their access to create a fraudulent ID card and sell their access to sensitive systems. Similiarly, we have instances in the corpus where DMV clerks have misused their access to scrape PII data about individuals without the need to know, and then turn around and sell that information for profit.
In both scenarios, the insider abused their authorization to impact the confidentiality or integrity of sensitive data or systems.
Sector Characteristics
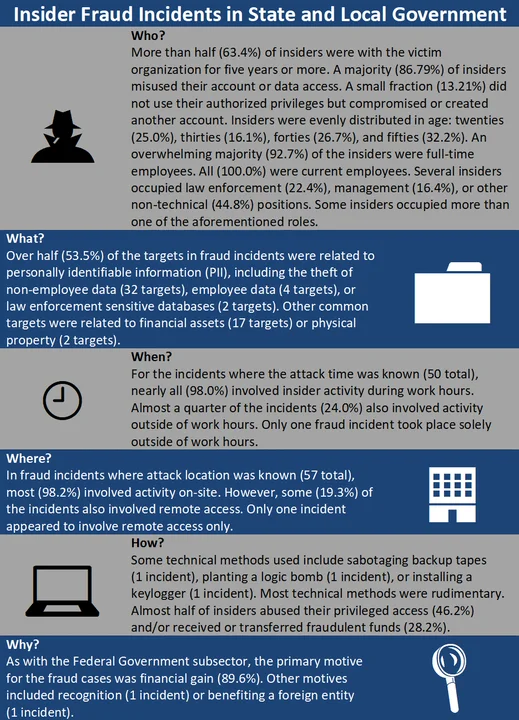
We summarize the findings from these fraud incidents below. These statistics consider only incidents where the case type is exclusively fraud and the industry subsector is either State Government, Local Government, or Emergency Services.
Analysis
Incidents in the State and Local Government subsector appear to share many similarities with Federal Government incidents, such as attack patterns and insider objectives (i.e., fraud). When we look at the overall impact and the targeted assets, we notice some differences. Federal Government insiders target non-employee data (31.6%), passports and immigration databases (21.3%), or financial assets (9.6%). State and local government insiders target non-employee data (49.6%) and financial assets (15.0%) at much higher rates, with an additional focus on employee data (7.1%).
Final Thoughts
The majority of insider incidents in the State and Local Government subsector of public administration occur due to the insider's authorized access to sensitive data. The unauthorized use of access can make it difficult for employers to differentiate activity that is potentially malicious from activity that is characteristic of typical job functions. Some specific best practices that organizations can use to mitigate insider threats include auditing employee activity such as database searches, monitoring the movement of monetary funds, and auditing the creation and modification of user accounts.
Stay tuned for the next post, in which we spotlight the Information Technology sector. Or subscribe to a feed of the Insider Threat blog to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, or to provide feedback, please contact insider-threat-feedback@cert.org.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
More By The Author
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
