Announcing Insider Threat Program Evaluator Training from the CERT National Insider Threat Center
The National Insider Threat Center (NITC) at the CERT Division of the SEI is developing an Insider Threat Program Evaluator (ITPE) Training course based on the methods and techniques the NITC currently uses to conduct Insider Threat Program Evaluations. This three-day, instructor-led, classroom-based, certificate training program presents strategies for measuring and evaluating an operational insider threat program within an organization. The first course will be offered in March 2018.
Organizations, including the federal government, are increasingly recognizing the need to counter insider threats and are doing it through specially focused teams. Several mandates for the federal government have been set forth in recent years including:
- M-11-08, Initial Assessments of Safeguarding and Counterintelligence Postures for Classified National Security Information in Automated Systems - Office of Management and Budget (OMB) memorandum dated January 2011 that evaluates the insider threat safeguards of government agencies.
- Executive Order (E.O.) 13587, Structural Reforms to Improve the Security of Classified Networks and the Responsible Sharing and Safeguarding of Classified Information [Obama 2011] - requires all federal agencies that have access to classified information and systems to have a formal insider threat program.
- National Industrial Security Program Operating Manual (NISPOM) - requires defense contractors to establish and maintain an insider threat program to meet many of the requirements of E.O. 13587.
- National Insider Threat Task Force (NITTF) minimum standards - requires a method to assess program strengths and weaknesses, and to identify areas for improvement. Complying organizations are required to conduct annual assessments.
The NITC has developed and used an Insider Threat Program Evaluation instrument over the past five years. This instrument assesses the robustness of an organization's program to prevent, detect, and respond to insider threats and provides recommendations for enhancing the program's effectiveness. In the long term, the evaluation results help organizations reduce exposure to damage from potential insider threats and strengthen their insider threat programs.
The NITC is in the process of developing the Insider Threat Program Evaluator (ITPE) Training course based on the methods and techniques it currently uses to conduct insider threat program evaluations. The course will use scenario-based exercises to show participants how to evaluate an insider threat program. Topics of exercises and discussions include techniques and templates for evaluation preparation and execution; processes for engagement, planning, data collection, scoring, and report development; and group discussions and summarized lessons learned for each exercise.
The NITC Insider Threat Program Evaluation criteria are based on both the NITTF minimum standards and NITC best practices1 developed over its almost 20 years of research and experience in the insider threat domain, along with its continuous work helping organizations build or improve their insider threat programs.
Participants will learn about all the components of a robust insider threat program, shown below, and how to compare them to the ITPE benchmark criteria. The instrument scores along a continuum that starts with meeting the NITTF and NISPOM minimum requirements and specific NITC practices. It ends with having an exceptional set of measures or practices in place.
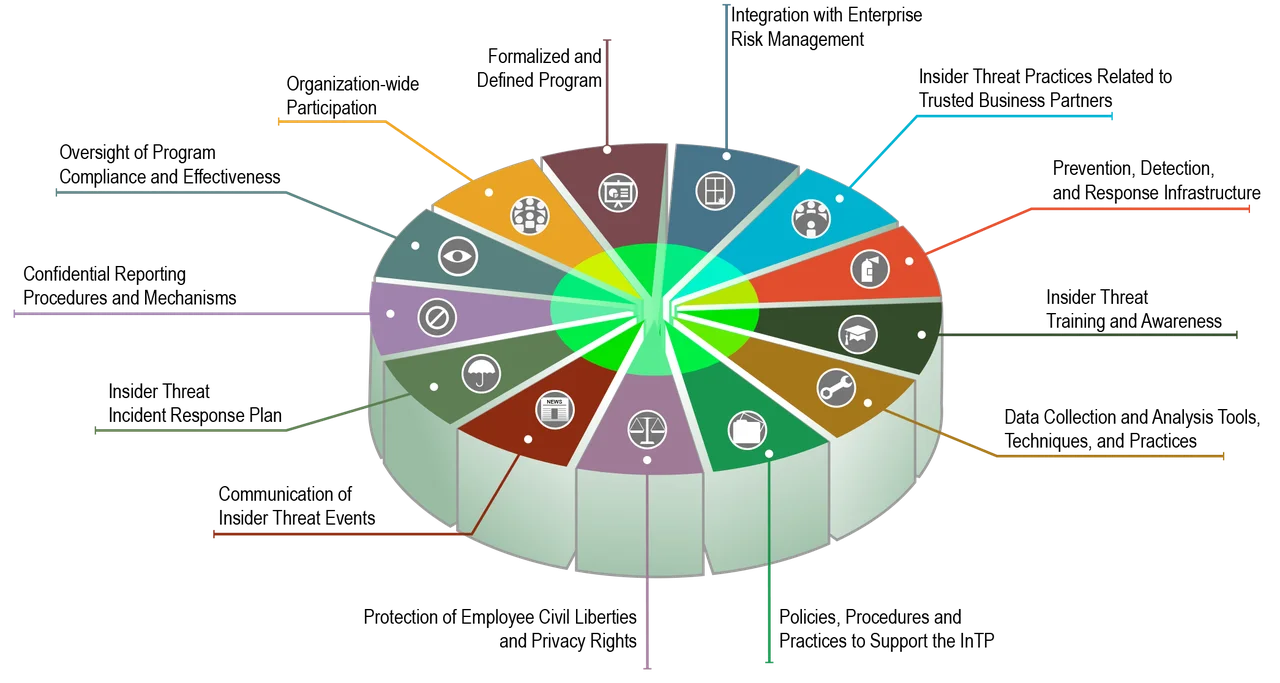
Figure 1: Components of an Insider Threat Program
This training is for insider threat program managers, evaluators, and team members and for those interested in licensing the CERT methodology and tools to perform an Insider Threat Program Evaluation. This course may also benefit those working in auditing or risk management.
The ITPE certificate program will enable evaluators to help organizations better understand the effectiveness of their established insider threat programs. Organizations will have the ability to license the CERT Insider Threat Program Evaluation methodology for internal use or to evaluate the effectiveness of other programs.
Participants who complete the course will be able to
- design an evaluation plan for working with an organization
- build a team of experts to perform the evaluation
- use the workbooks and templates to assess capabilities, components, and processes of an insider threat program
- score capabilities based on evidence-driven assessment of a set of specific indicators
- highlight key gaps within a program and recommend improvements or mitigations
Insider Threat Certificates and Training
The Insider Threat Program Evaluator Training joins other NITC insider threat training and certificate programs:
- Insider Threat Awareness Training (ITAT): one-hour course for all employees on the basics of insider threats and role responsibilities
- Insider Threat Program Manager (ITPM) Certificate: training for team members and program managers developing formal insider threat programs
- Insider Threat Vulnerability Assessor (ITVA) Certificate: training for insider threat program managers and for those interested in licensing the CERT methodology and tools to perform insider threat vulnerability assessments
- Insider Threat Analyst Training: Training for insider threat program analysts regarding strategies for collecting and analyzing data to prevent, detect, and respond to insider activity.
For more information on upcoming course dates and to register for an upcoming course, please visit https://www.sei.cmu.edu/education-outreach/credentials/index.cfm.
1 Various NITC best practices are discussed in the following resources: The CERT® Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud); Common Sense Guide to Mitigating Insider Threats (5th Ed.); and other publications located on the CERT Division web site: https://www.sei.cmu.edu/publications/index.cfm
More By The Authors
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
