Insider Threats Related to Cloud Computing--Installment 7: Seven Proposed Directions for Research and Two in Detail
Hi, this is Bill Claycomb and Alex Nicoll with installment 7 of a 10-part series on cloud-related insider threats. In this post, we introduce seven proposed directions for cloud-related insider threat research and discuss two of them in detail: socio-technical approaches and predictive models.
Cloud computing security is ripe with new opportunities for future research, including cloud-related insider threats. As mentioned previously, we do not believe the nature of the insider will change due to cloud computing's impact, but the opportunities for attacks will broaden. Researchers should take note of these new opportunities and respond accordingly to prevent, detect, and respond to new cloud- related insider attacks.
Some important future research topics are
- socio-technical approaches to insider threats
- predictive models
- identification of cloud-based indicators
- virtualization and hypervisors
- awareness and reporting
- normal user behavior analysis
- policy integration
Socio-Technical Approaches and Predictive Models
CERT has long advocated that insider threat prevention requires a combination of non-technical (i.e., socio) and technical input, as shown in the figure below.
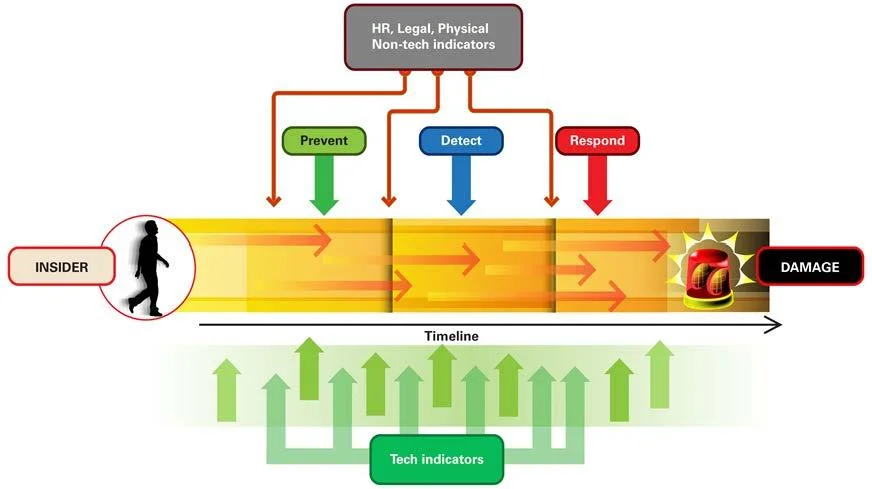
Examples of non-technical input include information on workplace behavior (e.g., tardiness, conflicts with others), personal behavior (e.g., drug or alcohol abuse, overwhelming debt), or human resources data (e.g., demographics, salary, position). Technical input is a more common data source used by researchers, and includes system logs, intrusion detection or data loss prevention systems, etc.
One of the first authors to identify the need to combine these sources is Schultz, who notes in his 2002 article A Framework for Understanding and Predicting Insider Attacks, "many different potential indicators of internal attacks exist," and suggests several indicators including technical and non- technical components. Others championed the same cause in the article Modeling Human Behavior to Anticipate Insider Attacks and the report Insider Threat Security Reference Architecture. However, few have implemented successful real-world socio-technical monitoring systems; and this remains an open research challenge.
Corresponding to that challenge is the ability to rank or weight the importance of specific indicators. The National Protective Security Authority advocates an ongoing insider threat risk management program that includes screening, access controls, promoting effective security culture, social engineering, protective monitoring and intrusion detection, and investigations. The centre has also published Risk Assessment for Personnel Security: A Guide.
Greitzer et al. advocate a predictive model that identifies several weighted indicators of insider risk. Furthermore, Greitzer et al. discuss development of a reasoning system to integrate multiple data sources and help analysts identify high-risk events in the paper Identifying At-Risk Employees: Modeling Psychosocial Precursors of Potential Insider Threats. Successfully ranking a combination of technical and non-technical indicators is a very challenging topic for future research.
A socio-technical approach to insider threats related to cloud computing is not directly applicable from the perspective of an organization concerned with the rogue administrator at the cloud provider, but it is useful when looking for employees who exploit cloud weaknesses or use the cloud against the employer. On the other hand, organizations may have some insight into certain important non-technical aspects of the cloud provider, such as hiring processes that include pre-employment screening.
Understanding how pre-employment screening, as described in Pre-Employment Screening: A Good Practice Guide, can identify potential threats is critical to reducing overall insider threats, both for cloud service consumers and providers. New directions in this area could include careful analysis of which pre-employment screening practices are most effective at identifying potential insider threat issues.
Coming up next: We'll discuss three more areas of future research on cloud-related insider threats.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed