Mapping the Health Insurance Portability and Accountability Act Security Rule to the Cyber Resilience Review
The 2003 Health Insurance Portability and Accountability Act (HIPAA) Security Rule requires health care organizations to safeguard electronic protected health information (ePHI). We have recently mapped the practice questions in the Cyber Resilience Review (CRR) to the Security Rule requirements. This post describes the mapping and how organizations can use the CRR alongside the HIPAA Security Rule.
What Is the HIPAA Security Rule?
The HIPAA Security Rule requires that health care organizations safeguard ePHI. Specifically, they must
- ensure the confidentiality, integrity, and availability of all ePHI they create, receive, maintain or transmit
- identify and protect against reasonably anticipated threats to the security or integrity of the information
- protect against reasonably anticipated, impermissible uses or disclosures
- ensure compliance by their workforce
Various tools and services exist to help organizations assess their compliance with the HIPAA Security Rule. The Security Rule lacks detailed implementation guidance, leaving it to organizations to decide if the security programs they implement provide coverage for the legislation and are effective at addressing their cyber risk. Organizations that are inexperienced at implementing a security program are likely to treat HIPAA compliance as the end game, rather than using them as the starting point for building a complete cyber program.
The U.S. Department of Homeland Security offers its own assessment of operational resilience and cybersecurity capabilities: the Cyber Resilience Review (CRR). The CERT Division of the SEI developed the CRR as a no-cost, voluntary, non-technical evaluation to help critical infrastructure organizations and key resource sectors, as well as organizations that are part of state, local, tribal, and territorial governments.
The CRR encompasses 10 domains of practices that organizations should implement to establish an effective, enterprise-wide cybersecurity management program.
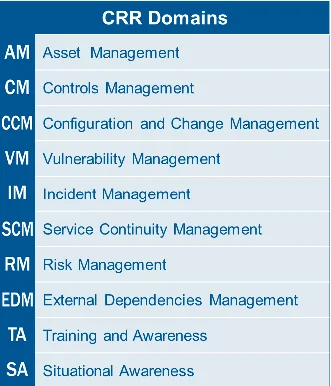
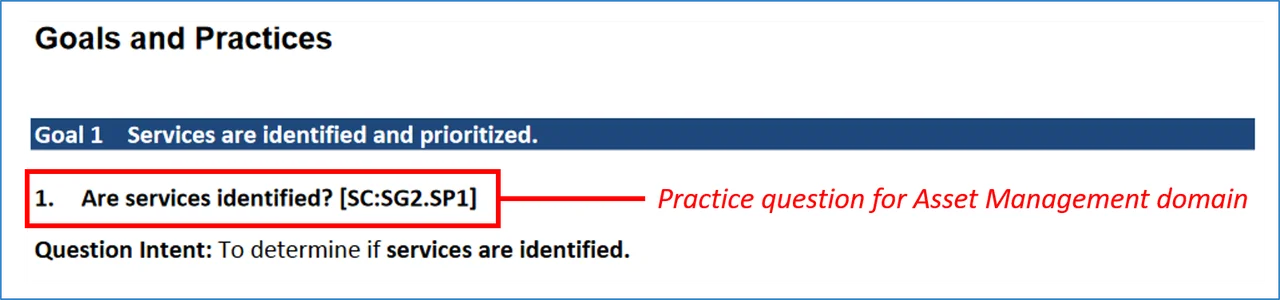
CRR domains and sample practice question
My colleagues and I set out to map the CRR practices to the requirements of the HIPAA Security Rule.
Mapping Approach
We used the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) as a touchstone. Born of Executive Order 13636, the CSF is a voluntary, risk-based, cybersecurity framework--a set of industry standards and best practices to help organizations manage cybersecurity risks. The HIPAA Security Rule and the CRR had already been mapped to the CSF, so we used the CSF as a Rosetta Stone to develop an initial mapping. The CERT Division had used a similar approach to map the CRR to the financial sector's cybersecurity assessment tool. We then checked and customized each mapping and added new ones not captured in the initial crosswalk.
Mapping Results
The mapping exercise showed that the CRR provides complete coverage of the HIPAA Security Rule. That is, the CRR provided guidance on each and every section of the HIPAA Security Rule's administrative, technical, and physical safeguards. Using the one-day, lightweight CRR gives an organization an indication of its cybersecurity program's compliance with the HIPAA Security Rule.
Of course, the mappings between the CRR practices and the HIPAA Security Rule are intended to be informative and do not imply or guarantee compliance with any laws or regulations. However, this correlation may provide organizations with justified confidence that if they can answer the CRR questions in the affirmative, they are effectively addressing the Security Rule. Organizations can use the full, section-by-section mapping, alongside the results of a CRR assessment, to examine the completeness of their existing policies, plan, processes, and procedures as they relate to the HIPAA Security Rule.
Beyond Compliance
While covered entities and business associates are required by law to comply with both the HIPAA Privacy Rule and the HIPAA Security Rule, this may not be enough to establish a comprehensive cybersecurity program. In fact, the mapping showed that 8% of the CRR practices went beyond the Security Rule requirements. A CRR assessment can highlight an organization's gaps in implementing a more comprehensive cybersecurity management program. It can also help organizations gauge their cybersecurity baseline against the NIST CSF.
Using the CRR as a measuring stick, the mapping shows that HIPAA Security Rule's administrative, physical, and technical safeguards contain gaps in coverage and can be augmented to more thoroughly identify the policies, plans, processes, and procedures necessary to adequately protect the confidentiality, integrity, and availability of electronic protected health information.
Send your thoughts on our mapping to info@sei.cmu.edu.
More By The Authors
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


