Mapping Cyber Hygiene to the NIST Cybersecurity Framework
In honor of Cybersecurity Awareness Month, I decided to put fingers to keys and share some basic practices that every organization should consider for their cyber hygiene initiatives. This blog post will describe a process to determine if 41 foundational practices from the CERT Resilience Management Model (CERT-RMM) are part of your NIST Cybersecurity Framework v1.1 target profile.
NIST Cybersecurity Framework
In 2013, President Obama signed Executive Order 13636 Improving Critical Infrastructure Cybersecurity to help identify the need for the cybersecurity of our critical infrastructure. In response, the National Institute of Standards and Technology (NIST) released the Cybersecurity Framework (CSF) 1.0.
This foundational body of work, now in version 1.1, breaks down into five functional areas: Identify, Protect, Detect, Respond, and Recover. These further break down into 23 categories and 108 subcategories, or desired outcomes. Here's an example: Protect (Function) -> Identify Management, Authentication and Access Control (Category) -> Remote access is managed (subcategory). The CSF maps these subcategories to existing standards, such as ISO 27001:2013 and NIST Special Publication 800-53 Revision 4, in the form of informative references. Readers can also use the references to align their understanding of the practices with the stated desired outcome (subcategory).
The CSF also incorporates profiles, both current and target. An organization would create a current profile to identify all subcategories it is executing at an acceptable level. Organizational leadership would create the equally important target profile to identify the desired end state of the organization's cybersecurity program. For the vast majority of organizations, the target profile should not include the entirety of the CSF. Instead, the target profile should express an organization's understanding of the most important, impactful cybersecurity practices that enable the business to achieve its mission objectives. To state it more plainly, cybersecurity practices should be business enablers, not obstacles.
Cyber Hygiene
Back in 2017, I worked with my colleagues Charles Wallen and Alexander Petrilli to identify the baseline set of CERT-RMM practices that every organization should consider. One of our methods was to map the more than 200 CERT-RMM practices to similar standards, identify the correlations, and select the practices that were the basic building blocks for more advanced cyber capabilities.
That year, we published a blog post on the 11 functional cyber hygiene areas that encompass 41 essential CERT-RMM practices, which we outlined in a presentation.
Since then, our team has spoken about cyber hygiene regularly as we conduct assessments of critical infrastructure organizations and present at cyber-related conferences. We want organizations to understand that performing these practices are as foundational to using cyber-related assets as brushing your teeth or bathing are to personal health.
These 11 functional cyber hygiene areas are
- Identify and prioritize key organizational services, products, and their supporting assets.
- Identify, prioritize, and respond to risks to the organization's key services and products.
- Establish an incident response plan.
- Conduct cybersecurity education and awareness activities.
- Establish network security and monitoring.
- Control access based on least privilege and maintain the user access accounts.
- Manage technology changes and use standardized secure configurations.
- Implement controls to protect and recover data.
- Prevent and monitor malware exposures.
- Manage cyber risks associated with suppliers and external dependencies.
- Perform cyber threat and vulnerability monitoring and remediation.
On the surface, these functional areas are very broad and are carried out using organizational assets from all four CERT-RMM asset categories: technology, information, people, and facilities. Each functional area consists of one or more basic practices that are imperative to the proper execution of tasks related to the specific area.
For example, functional area #2, Identify, prioritize, and respond to risks to the organization's key services and products, consists of hygiene practices about identifying risks to your critical services, establishing criteria for measuring those risks, and dispositioning those risks. These identified practices are essential to building an effective risk management function within any organization.
Several of our customers are currently using assessment tools based on CERT-RMM practices. Some of these tools identify assessment questions related to the cyber hygiene practices. Identifying these cyber hygiene practices in the assessment output indicates whether an organization's policies, plans, processes, and procedures are addressing basic cybersecurity practices.
A response of No or Incomplete to one of the assessment's cyber hygiene questions should alert the organization to take a second look at practices in that area. Perhaps the organization has dispositioned a risk related to that area and is aware of the gap. However, more often than not, it's an oversight in the practices that represents a foundational gap within the organization's overall cybersecurity program.
If your organization has not participated in one of these free, lightweight, one-day assessments, I encourage out to reach out to your local Department of Homeland Security Cybersecurity Advisor (CSA) and schedule a Cyber Resilience Review (CRR) at https://www.us-cert.gov/resources/assessments.
Mapping Cyber Hygiene Practices to the NIST CSF
If you've created a current and target CSF profile, you can use the overlay shown below to help you identify any gaps within your current cybersecurity program.
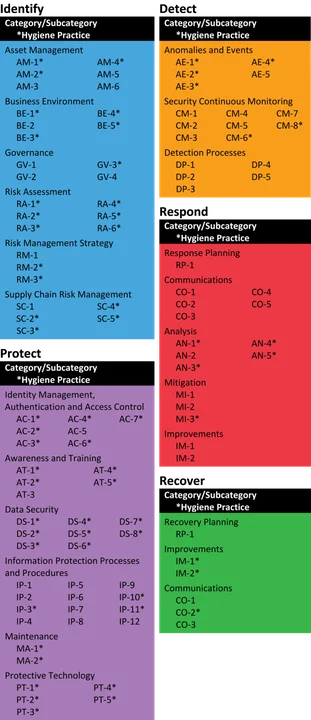
Conclusion
Though we recommend these basic cyber hygiene practices, they are not the only way to ensure your organization has a solid basis for a comprehensive cybersecurity program. That said, if your organization chooses not to implement even one of them, we urge you to consider why. If you do choose to implement them, or make any other substantial change to your cybersecurity program, seek support from your organization's leadership.
More By The Author
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
