Insider Threats in Healthcare (Part 7 of 9: Insider Threats Across Industry Sectors)
PUBLISHED IN
Insider ThreatNext in the Insider Threats Across Industry Sectors series is Healthcare. As Healthcare-related information security conversations are predominantly driven by security and privacy concerns related to patient care and data, it's important to recognize the magnitude of security lapses in this sector. Patients can face severe, permanent consequences from medical record misuse, alteration, or destruction. And medical record fraud vis-a-vis identify theft, otherwise known simply as Fraud in our incident corpus, is one of the primary types of security instances observed in this sector.
Defining and enforcing security and privacy protections in this sector is the 1996 Health Insurance Portability and Accountability Act of 1996 (HIPAA), which has since been expanded. The HIPAA Privacy Rule specifies data-access standards for personal health information (PHI) (i.e., who may access PHI). The HIPAA Security Rule defines requirements for ensuring that proper authentication and authorization policies and practices are in place for accessing electronic PHI in medical records.
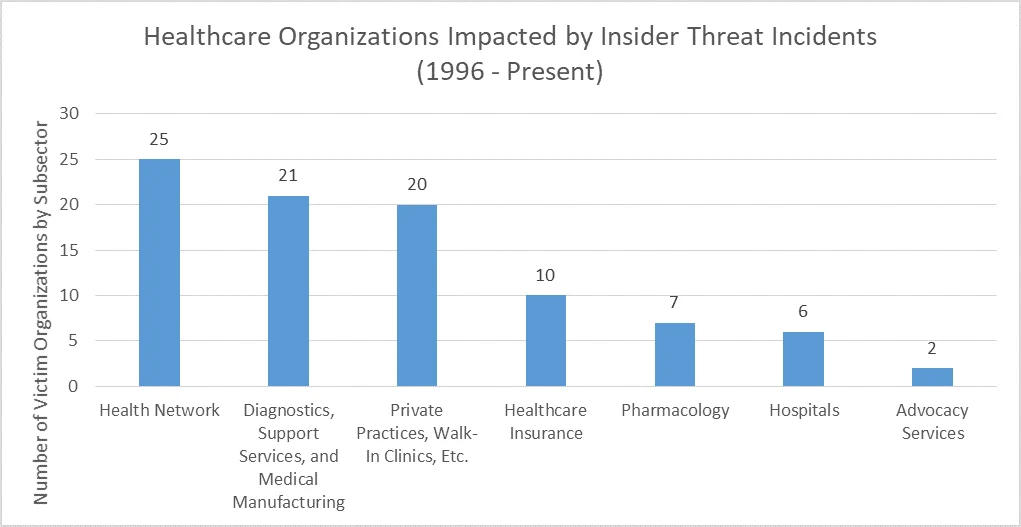
In our National Insider Threat Center (NITC) Incident Corpus, we identified 88 malicious insider incidents impacting Healthcare organizations. These incidents do not include unintentional insider threats who may have accidentally left a laptop at a bus stop or sent an email containing PHI to a party that it wasn't intended for. The 88 malicious insider incidents map to 91 healthcare organizations that were directly victimized in the attack (i.e., in some incidents, there is more than one direct victim organization). Of these victim organizations, Health Networks make up the largest subsector. Health Networks, also known as Integrated Health Systems, are networks of hospitals and private practices that are dedicated to bringing healthcare to a specific region.
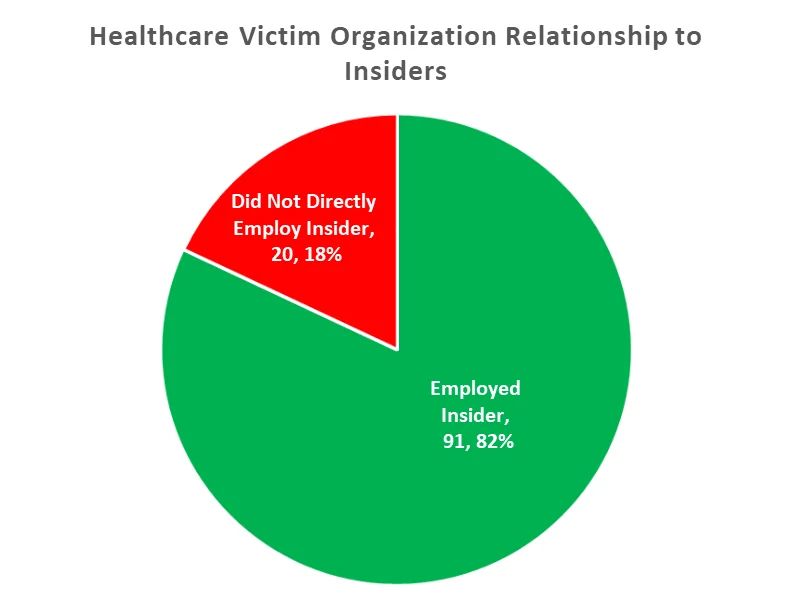
In addition to the 91 direct victim organizations, 20 victim organizations indirectly employed the insider in some sort of trusted business partner relationship or non-regular full-time employment (e.g., contractors).
Sector Overview
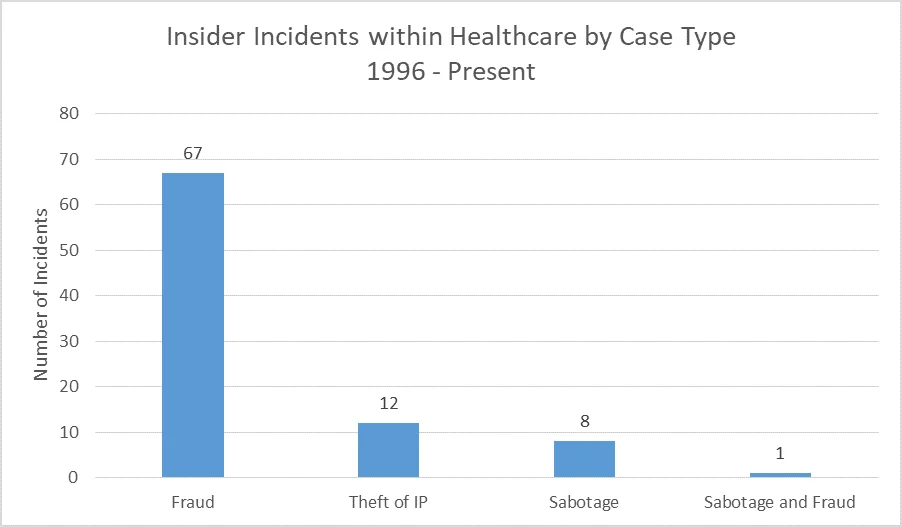
Fraud is the most prevalent case type across all of the insider threat incidents within the Healthcare Sector. It occurred in some form in about 76% of all incidents. This rate of fraud is at a higher observed frequency than across the entire NITC corpus (68%). Within these fraud cases, we generally see individuals with access to patient payment records taking advantage of their access to customer/patient data to create fraudulent assets such as credit cards in order to make a profit.
Sector Characteristics
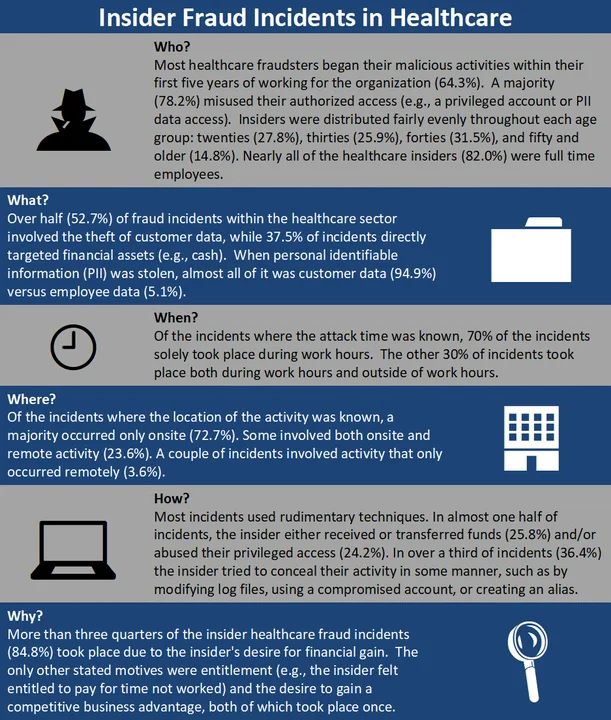
Below is a summary of the Healthcare Fraud incidents that are contained within the NITC corpus.
Analysis
Although Healthcare may be an industry defined by unique regulations (e.g., HIPAA), the statistics gathered for it are similar to the statistics gathered from the broader NITC corpus. For almost all of the insider fraud cases within healthcare, the insider followed a similar path of improperly using patient PII or PHI to acquire some asset in order to gain a profit.
Financial impact differs slightly from the Healthcare sector to the broader NITC corpus. From the incidents with a reported financial impact, eight healthcare organizations (11.6%) recorded a financial impact of greater than $1 million. A higher percentage of fraud incidents (16.9%) outside of the Healthcare sector in the NITC corpus recorded the same financial loss. Notably, we did not find a significant difference in high financial impact. This is noteworthy because, given the gravity of healthcare data and the legal and reputational penalties associated with a breach, we might expect a potentially higher frequency of significant financial loss for the Healthcare sector.
Final Thoughts
Healthcare information security should be of the utmost importance for administrators and IT staff alike. Although identity theft is the most common misuse of patient data, patients could face severe medical debt from identity theft.
To better protect healthcare organizations from insider threat incidents, it is suggested that organizations participate in an Information Sharing and Analysis Center (ISAC) to receive pertinent information and help propagate a collaborative security environment. In addition to participating in an ISAC, it is also suggested that organizations enforce least privilege concerning organizational roles and data access along with tracking and blocking data exfiltration.
Stay tuned for the next post, in which we spotlight the Entertainment sector. Or subscribe to a feed of the Insider Threat blog to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, or to provide feedback, please contact insider-threat-feedback@cert.org.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
More By The Authors
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


