Insider Threats in Finance and Insurance (Part 4 of 9: Insider Threats Across Industry Sectors)
PUBLISHED IN
Insider ThreatThis post was co-authored by Jonathan Trotman.
In the previous post of our series analyzing and summarizing insider incidents across multiple sectors, we discussed some of the mandates and requirements associated with federal government insider threat programs as well as documented insider threat incidents. In this post, we will discuss information security regulations and insider threat metrics based on Finance and Insurance incidents from our CERT National Insider Threat Center (NITC) Incident Corpus.
For context, Finance and Insurance refers to a collection of organizations working across various facets of financial services. The graph below shows incident counts in this sector.
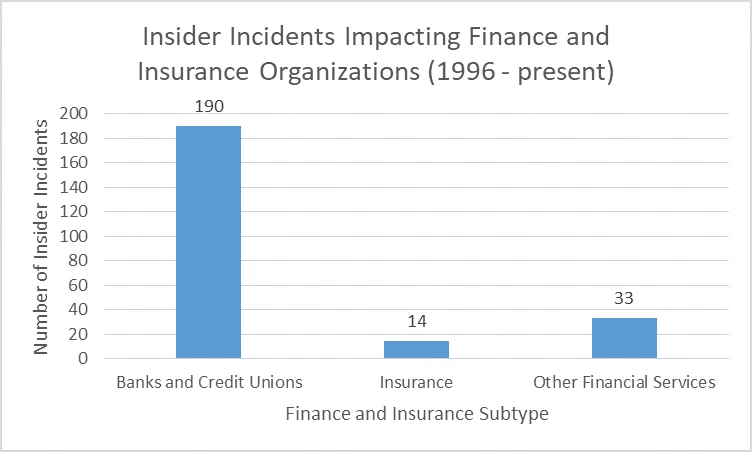
With the statistics that follow, keep in mind that Banks and Credit Unions are far more represented than Insurance or Other Financial Services in the CERT NITC Incident Corpus.
In total, we identified 237 malicious, non-espionage insider incidents where a Finance and Insurance organization was both the victim organization and the direct employer. There were 148 additional incidents where a Finance and Insurance industry organization was impacted by a Trusted Business Partner (e.g., temporary employees, outsourced computer support, or cleaning services) or an insider incident at another organization. In one incident, more than 20 individuals (approximately half of them insiders and half of them outsiders) targeted more than a dozen Finance and Insurance organizations across multiple states as part of a Stolen Identity Refund Fraud (SIRF) scheme coordinated by an outsider-ringleader. This incident underscores the ubiquity of SIRF schemes within Finance and Insurance organizations and the threat of collusion with outsiders. Finance and Insurance organizations are well-served by getting involved with information sharing groups, such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) to collaborate with others in the sector.
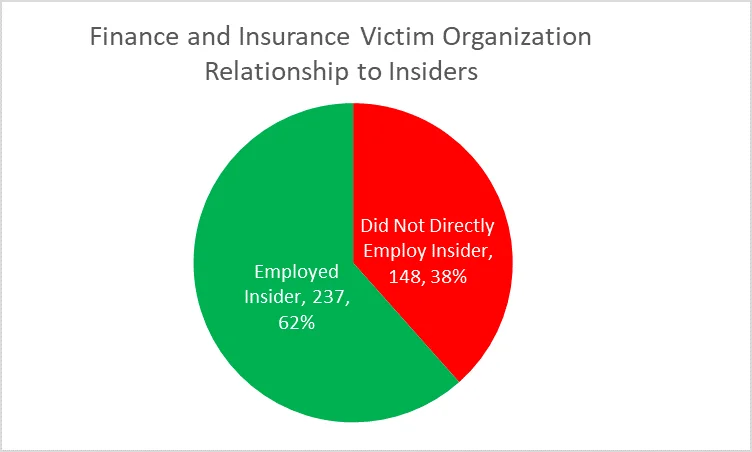
Sector Overview
To understand the Finance and Insurance insider threat landscape, we first need to understand its regulations and their background check guidance:
- 1999: The Gramm-Leach-Bliley Act (GLBA), also known as the Financial Modernization Act, requires that financial institutions take steps to ensure the security and confidentiality of customers' personal and financial information. The Federal Trade Commission (FTC), as part of its implementation of GLBA, issued the Safeguards Rule. The Safeguards Rule in turn recommends, among other best practices, checking references and performing background checks as part of the hiring process for employees that would have access to customer information.
- 2002: Section 404 of the Sarbanes-Oxley Act (SOX) requires an assessment of the internal control structure used to ensure financial statement account and disclosure accuracy, which involves detecting security breaches. It also implicitly necessitates employee background checks.
- 2004: Guidance for reference and background checks is also provided by the Payment Card Industry Data Security Standards (PCI DSS) Council.
Taken together, these regulations would suggest that Finance and Insurance employees are vetted before they ever have system access. However, as we have demonstrated, insider threats still persist.
As the chart below shows, Fraud is the most frequent insider threat incident type for Finance and Insurance organizations (in the CERT Insider Incident Corpus), followed by Theft of Intellectual Property (IP) and IT Sabotage. In the four incidents where two case types were present, Fraud was one of them. Fraud is all too commonplace in the Finance and Insurance sector because employees have a high degree of access to money and sensitive financial data.
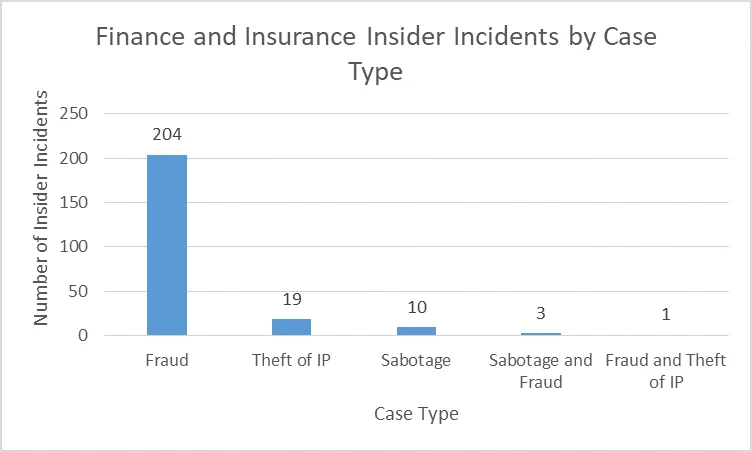
Given how few reported incidents involved Theft of IP or IT Sabotage, the following analyses focuses on incidents of Fraud where the insider was employed by the Finance and Insurance victim organization.
Sector Characteristics
Nearly all (87.8%) of the insider incidents impacting Finance and Insurance organizations involved Fraud. The Fraud statistics below include only the 204 incidents where no other incident type was known. Each attribute (i.e., Who, What, When, Where, How, Why) represents only the cases where that attribute was known.
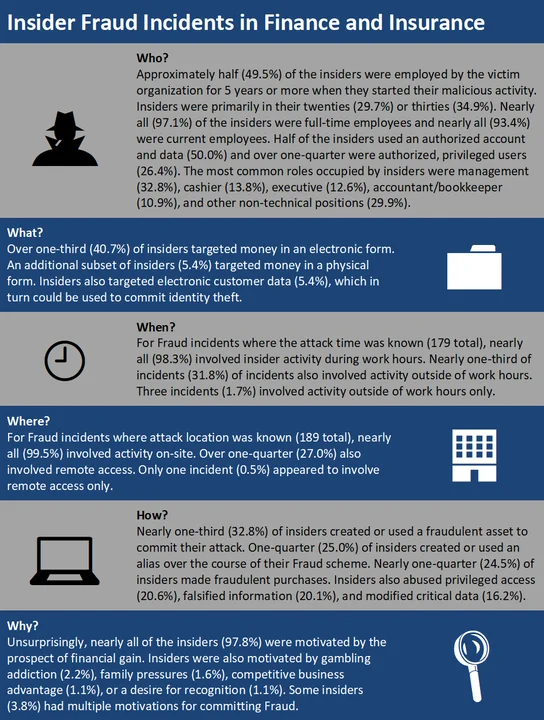
Analysis
Insiders committing Fraud in Finance and Insurance organizations tended to be more tenured employees, and many were in leadership positions. These insiders also had privileged access to information systems and customer personally identifiable information (PII) commensurate with that level of experience or role. In turn, these insiders exploited vulnerabilities in processes they were familiar with to access money or customer data. Nearly all of the insiders were motivated purely by financial gain, with a portion of those insiders also under financial stress from a gambling problem or family distress. In Finance and Insurance insider incidents where the financial impact was known (221 total), the median financial impact was between $98,137 and $268,403. Again, the median impact across the CERT Insider Threat Incident Corpus is between $95,200 and $257,500. The Finance and Insurance incidents, since they comprise the majority of the incidents collected, essentially define the median financial impact range of the corpus.
Final Thoughts
As we addressed earlier in this post, organizations subject to the Safeguards Rule are encouraged to perform background checks before hire. At the NITC, we also advocate for employee background checks. However, given the evidence around the tenure of insiders, recurring background checks are also advisable, particularly when an employee receives increased or new access to customer information. After all, we saw that managers and executives are also capable of committing Fraud.
However, SOX compliance can pose significant financial and implementation challenges for organizations, even 16 years after its passage. With those costs, organizations may not be performing background checks as frequently or extensively as is needed to address emerging threats from within.
If you work for a small organization that must comply with SOX, review the Securities and Exchange Commission's Section 404 Guide for Small Business. Organizations small and large can also reference the Common Sense Guide to Mitigating Insider Threats, Fifth Edition, for additional best practices on how to improve their security posture.
For recommendations for your insider threat program, stay tuned for future blog posts related to your industry. Check back in a few weeks to read our next industry post on state and local government, or subscribe to a feed of the Insider Threat blog to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, please contact insider-threat-feedback@cert.org.
Entries in the "Insider Threats Across Industry Sectors" series:
- Part 1: Insider Threat Incident Analysis by Sector
- Part 2: Classifying Industry Sectors: Our New Approach to an Industry Sector Taxonomy
- Part 3: Insider Threats in the Federal Government
- Part 4: Insider Threats in Finance and Insurance
- Part 5: Insider Threats in State and Local Government
- Part 6: Insider Threats in Information Technology
- Part 7: Insider Threats in Healthcare
- Part 8: Insider Threats in Entertainment
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
