Insider Threat Incidents: Communication Channels
PUBLISHED IN
Insider ThreatThe CERT National Insider Threat Center collects, categorizes, and analyzes technical insider incidents--those in which the insider used technology--to monitor the evolving insider threat landscape. In a previous blog post, we reviewed the devices that are affected in insider threat incidents. In this post, we categorize incidents by the channels insiders use to communicate with their co-conspirators as they plan, attack, or conceal their attack on an organization.
Insider Collusion
The communications we address in this post are between insiders and those they collude with over the course of insider incidents. Since we first wrote about insider collusion in a 2016 blog post, additional data in the CERT Insider Threat Incident Corpus has shown a decrease in the proportion of collusion incidents. Still, as shown in the chart below, more than a quarter of the cases in our corpus involve collusion. Of those cases, three-quarters involve outsiders, an increase from our 2016 data.
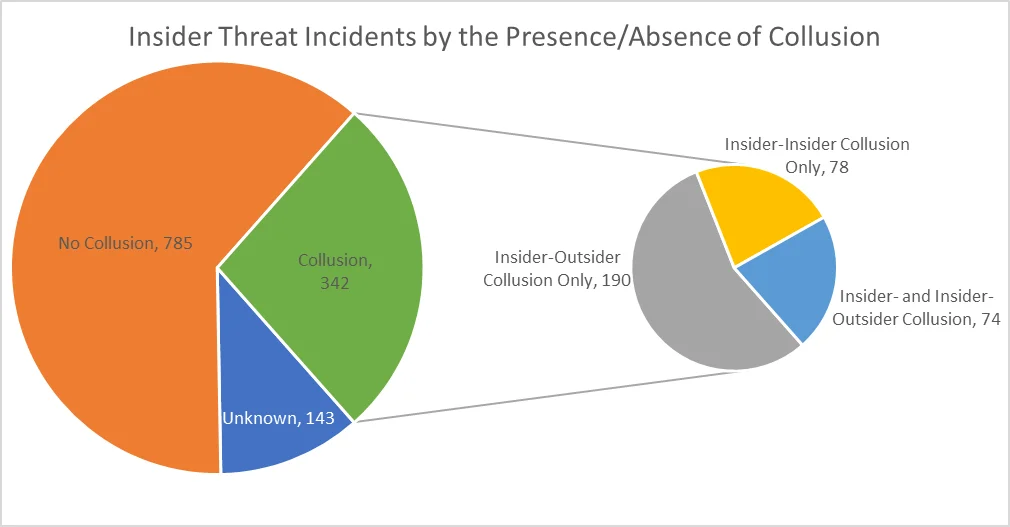
Insiders might collude with others to bypass organizational controls, increase profits, or conceal activity. The kinds of accomplices or conspirators that insiders collude with affect the means, including communication channels, by which insiders plan their actions.
Communication Channels
We use the term "communication channel" to describe any mode the insider uses, while planning or executing the incident, to communicate with one or more involved people. This communication is between those knowingly engaging or participating in the insider incident: insiders, an insider and an outsider, or the insider and various third parties.
Communication between parties need not involve the transmission of sensitive data. The insider and the co-conspirators may simply be planning their hostile act. For our purposes, an exfiltration channel is not a communication channel unless stolen data is sent between two people. For example, an insider stealing data by emailing it to themselves is not a communication--it is purely exfiltration. In contrast, an insider stealing data by sending it to someone else is a communication as well as an exfiltration
The chart below shows how frequently different communication channels are used during insider incidents.
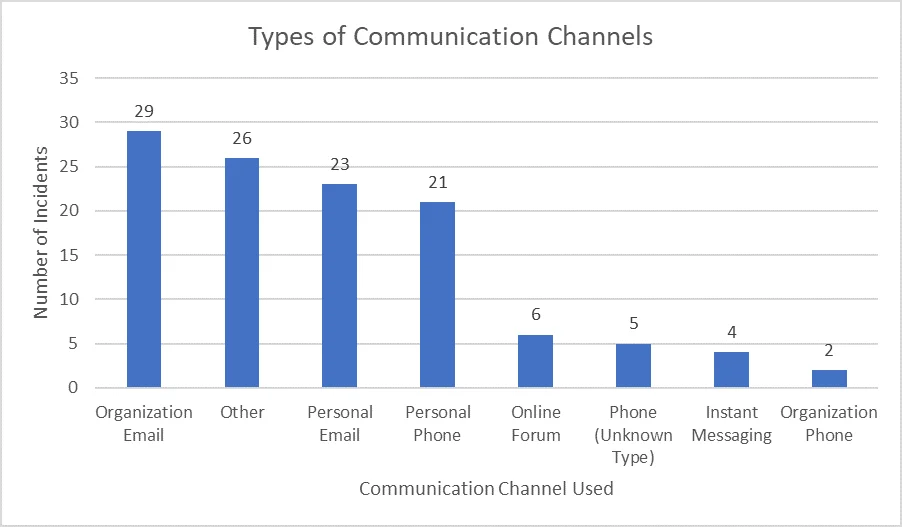
To communicate with co-conspirators, most insiders use email controlled or owned by the victim organization, apparently the email accounts they use every day. This finding underscores that insiders misuse their authorized access to critical assets.
We can also look at the number of communication channels that insiders use. As the graph below shows, most insiders used a single communication channel, but we identified insiders using as many as three channels. Colluding insiders committing fraud tend to use more communication channels on average than any other case type.
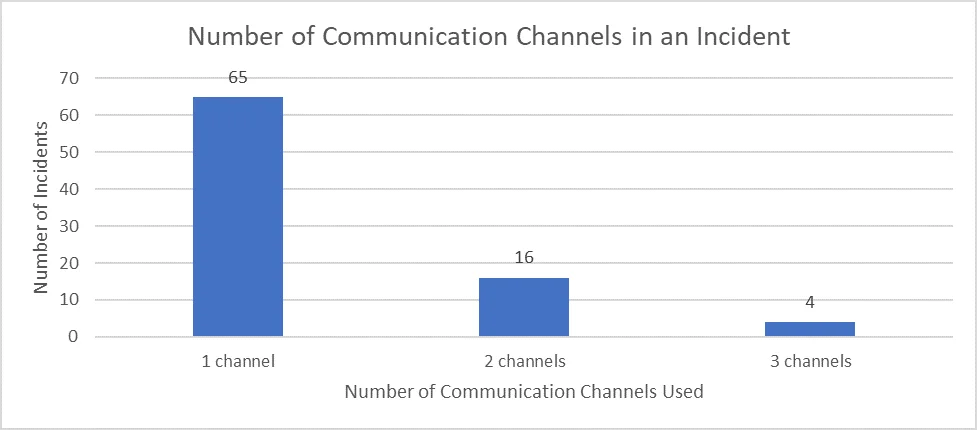
The primary consequence of insiders' use of a single communication channel is that there may be few data sources that can be used to identify that collusion is taking place.
Differences in Case Type
Of the four types of insider cases--fraud, theft of intellectual property (IP), misuse, and IT sabotage--IT sabotage and misuse cases generally are not associated with collusion. Looking at fraud and theft of IP, we can begin to identify some differences in the types of communications channels used.
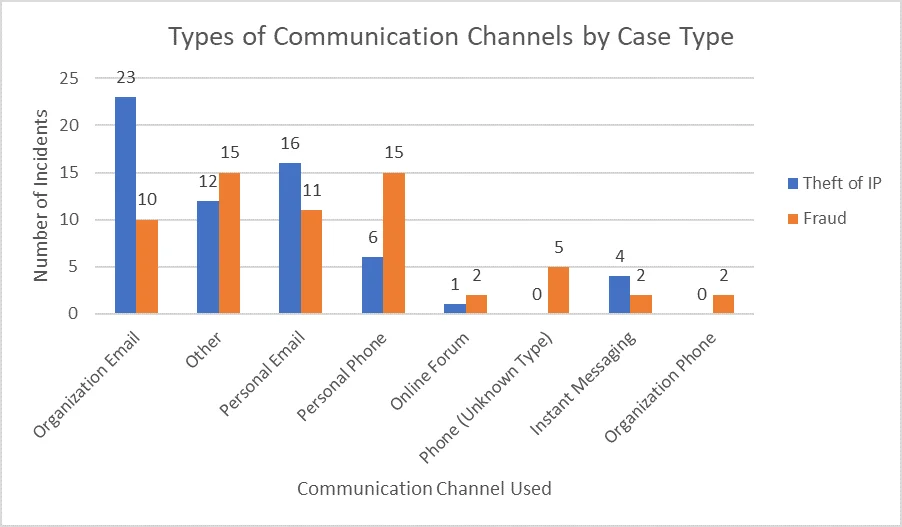
In IP theft cases, insiders use both organization-controlled email and their personal email to communicate. Given the volume of data typically exfiltrated in IP theft incidents, and their expected depth of coordination, it is not surprising to see email used so frequently.
Perhaps more surprising is the greater use of phones and mobile devices in fraud incidents. While numerous encrypted and anonymized messaging applications exist, many insiders communicate over texts or phone calls. However, the most common communication channel among fraud cases falls outside of the taxonomy. The "Other" category contains a number of different media, with email accounts of an unspecified type accounting for nearly one-third (30.8%). Other common examples include paper-based communications (e.g., hand-written notes and faxes) or in-person communications.
Implications for Insider Threat Monitoring
To prevent theft of IP, organizations may want to invest in anomaly detection for email communications to identify potential collusion, whether with other insiders or outsiders. Additionally, data loss prevention (DLP) solutions may identify attempts to circumvent IP policies.
While phones and mobile devices are used more often by insiders committing fraud, employee-owned devices are not always available or eligible for monitoring. Because many insiders collude with conspirators with whom they have personal relationships, it may be difficult to determine malicious from benign communication patterns even if the data source is available.
Further Resources
For more information about what controls your organization can use to monitor its infrastructure, check out Improving Insider Threat Detection Methods Through Software Engineering Principles. For other information concerning monitoring and mitigating insider threat, see The Common Sense Guide to Mitigating Insider Threats, Sixth Edition.
More By The Authors
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


