Devops Q&A: Frequently Asked Questions
PUBLISHED IN
DevSecOpsSince beginning our DevOps blog in November, and participating in webinars and conferences, we have received many questions that span the various facets of DevOps, including change management, security, and methodologies. This post will address some of the most frequently asked questions.
How does Change and Release Management integrate with DevOps?
First off, the DevOps culture involves embracing change. One of the core principles of DevOps, the second of the Three Ways according to Gene Kim, is to amplify feedback loops. The Second Way is the continual, iterative feedback loop allowing us to respond quickly to customer needs. This feedback loop is where change management comes into play. Often, change management occurs when things don't work the way you expected, or the customer (who can be internal or external) decides that a change should be made to increase business value. This type of change is OK. In fact you should embrace it.
Without DevOps and the encouragement of continuous integration (CI) and continuous delivery (CD), a requested change usually didn't occur until after an official release. But with CI and CD in place teams can achieve faster and more frequent releases. Our customers therefore potentially see those changes in their products earlier. These rapid updates allow them to more quickly evaluate the product and their own requirements, which in turn leads to change requests. Let's face it, nothing brings about a change to requirements quite like actually seeing and using the product.
In such an iterative environment/process how do you ensure that security requirements are always considered? Should we have a security person also in the DevOp process?
Security must be a first-class citizen throughout the DevOps processes. Here is the typical Venn diagram you see describing DevOps.
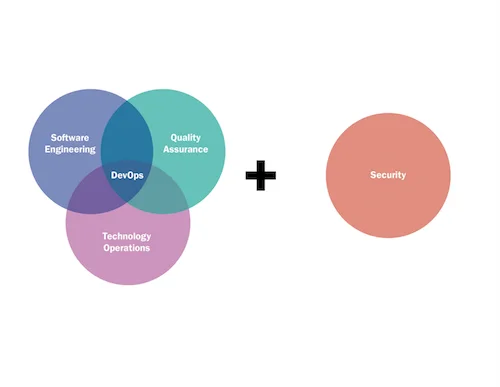
Actually, security is often overlooked, and its circle is not even pictured. When describing secure DevOps, which we preach here at the SEI's CERT Division, the diagram should look like this
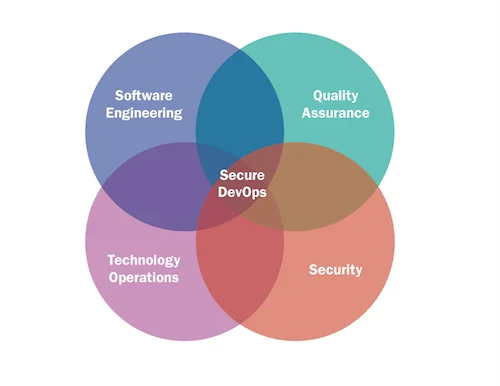
Security must always be considered and a security expert should be involved in the DevOps process from the beginning. You cannot expect a developer or an operations team member to make the necessary security decisions for a given project. If security is a concern (and these days it should always be a concern) to your business, then there is obviously room for a full-role dedicated to a primary subject matter expert in security/privacy. Your developer or operations professional should be an expert on topics such as
- data privacy
- intrusion detection
- threat vectors
- Common Vulnerabilities and Exposures (CVEs)
- package security
- authentication
- authorization
- security standards compliance
Microsoft has worked on a Security Development Lifecycle that shows how to include security into a project's lifecycle. The bottom line is that a security professional should collaborate with your DevOps team from the beginning of a project, because this individual will think of security-related items that others in the room will not, and you'll be glad for it.
Is DevOps used for Agile methodology only or can it be really useful for any kind of development life cycle?
DevOps is really an extension of Agile methodologies, but it is also more of a culture or philosophy (See the Three Ways link in the first question). You can adopt DevOps without practicing Agile methodologies since there is clearly more to DevOps than just your software development lifecycle (SDLC), but it may be harder. Agile certainly compliments DevOps with its iterative processes more than other SDLC's, such as the Waterfall model. You can still be successful without following Agile methods, but software development projects typically realize more successes with Agile practices.
Every two weeks, the SEI will publish a new blog post that offers guidelines and practical advice to organizations seeking to adopt DevOps in practice. We welcome your feedback on this series, as well as suggestions for future content. Please leave feedback in the comments section below.
Additional Resources
To view the webinar Culture Shock: Unlocking DevOps with Collaboration and Communication with Aaron Volkmann and Todd Waits please click here.
To view the webinar What DevOps is Not! with Hasan Yasar and C. Aaron Cois, please click here.
To listen to the podcast DevOps--Transform Development and Operations for Fast, Secure Deployments featuring Gene Kim and Julia Allen, please click here.
To read all of the blog posts in our DevOps series, please click here.
More By The Author
PUBLISHED IN
DevSecOpsGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
