Follow the CUI: 4 Steps to Starting Your CMMC Assessment
PUBLISHED IN
Enterprise Risk and Resilience ManagementOne of the primary drivers of the Department of Defense (DoD) Cybersecurity Maturity Model Certification (CMMC) 1.0 is the congressional mandate to reduce the risk of accidental disclosure of controlled unclassified information (CUI). However, a full CMMC assessment can seem daunting to organizations in the Defense Industrial Base (DIB), and many might not know where to start. This blog post gives DIB organizations four steps for identifying their CUI exposure in terms of their critical services and the assets that support them. This approach can help DIB organizations properly scope a CMMC assessment and contain the costs of protecting CUI.
CERT-RMM as a Foundation
As a member of the SEI CERT Division's Cybersecurity Assurance Team, I have conducted dozens of assessments of critical infrastructure organizations, including those in the DIB. These assessments focus on an organization's capability to protect and sustain critical services--and their CUI--during times of both normal and stressful operations. Essentially, we evaluated operational resilience through the lens of critical services.
This approach is consistent with the SEI-developed CERT Resilience Management Model (CERT-RMM), which defines the practices, metrics, and maturity-based processes needed to plan, communicate, and evaluate operational resilience improvements throughout an enterprise. (See a blog post by my colleagues Andrew Hoover and Katie Stewart for more information on process maturity.) CERT-RMM encourages organizations to evaluate their operational resilience through the lens of their critical services.
For many DIB organizations, those critical services depend on proper handling of CUI. Focusing on those critical services will help you prepare for a CMMC assessment, as discussed below, based on the steps derived from CERT-RMM.
First, Identify Critical Services
Start by focusing on the business services that are critical to your customer: those goods or services your organization produces to help your customers and partners execute their mission. For example, let's assume you work for a DIB company that has a contract to supply electronic components to a business partner with a DoD contract. One critical business service would be your ability to accept and fulfill orders from your business partners. Your B2B Order Portal would be a primary focus for this service because you need it to meet the needs of your business partner. Obviously, this component is supported by myriad internal services that help achieve the mission of delivering components to your customer.
Identifying an organization's critical services can be as simple as reviewing its mission statement, then associating the services that most obviously address the mission. Organizations may have already conducted this exercise and will only have to look at their most recent business impact analysis (BIA). A properly executed BIA will identify the most important services provided to both customers and partners.
In our example, the electronics supplier organization, and even relevant internal departments, should have a mission statement that aligns with the overall business mission. A BIA should also identify the B2B Order Portal as a critical component of your order fulfillment business service.
Second, Define Organizational Assets
Now let's define the organizational assets that help achieve your mission as four asset types:
- Technology - The hardware and software used to drive your critical services, which may include services provided to you through a cloud service provider (CSP) or managed (security) service providers (MSP/MSSP).
- Information - Primarily, the information produced by your critical services, such as product schematics, customer information, order information, and so on.
- People - Those people (including your supply chain) responsible for the operation of your critical services.
- Facilities - A physical structure that contains any of the other three asset types that support your critical service.
Now that your critical services and the types of organizational assets you want to include in this exercise are identified, we move to the next step: scoping the critical service.
Third, Scope Your Critical Services
Scoping a critical service consists of identifying the assets that support it: technology, information, people, and facilities. You'll then know exactly which assets are part of the service and which are not.
One of the most effective tools I use to scope critical services is a data flow diagram, similar to ones used in threat modeling. (Also read my blog post about Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege, or STRIDE, threat modeling.) A data flow diagram consists of the four asset types listed above, set in the order in which a critical service uses them. In our B2B Order Portal example, we start with the portal itself. The following are sample questions to ask during scoping.
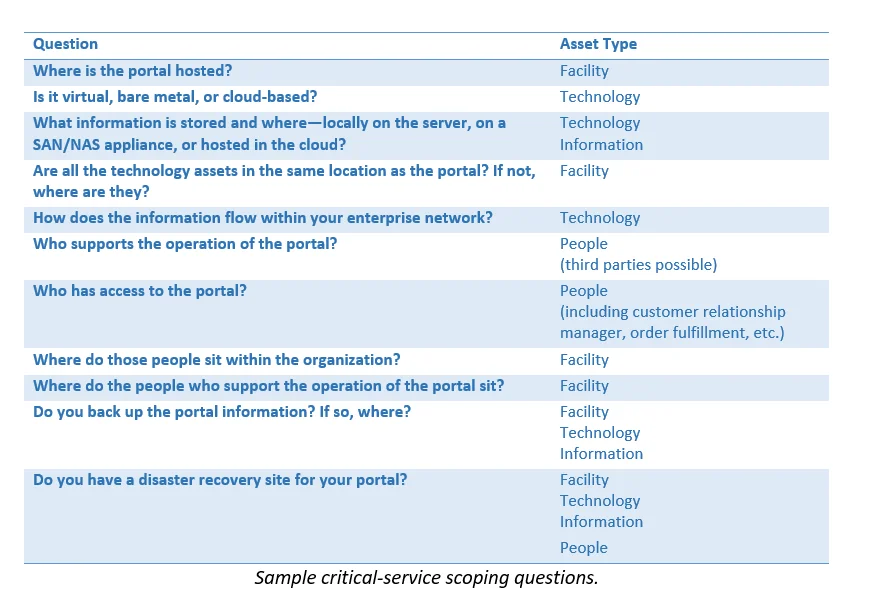
The answers to these questions help you create a data flow diagram, which provides a comprehensive picture of the facilities, people, technology, and information involved in delivering critical services to your customers. Figure 1 shows an example data flow diagram that includes all four asset types.
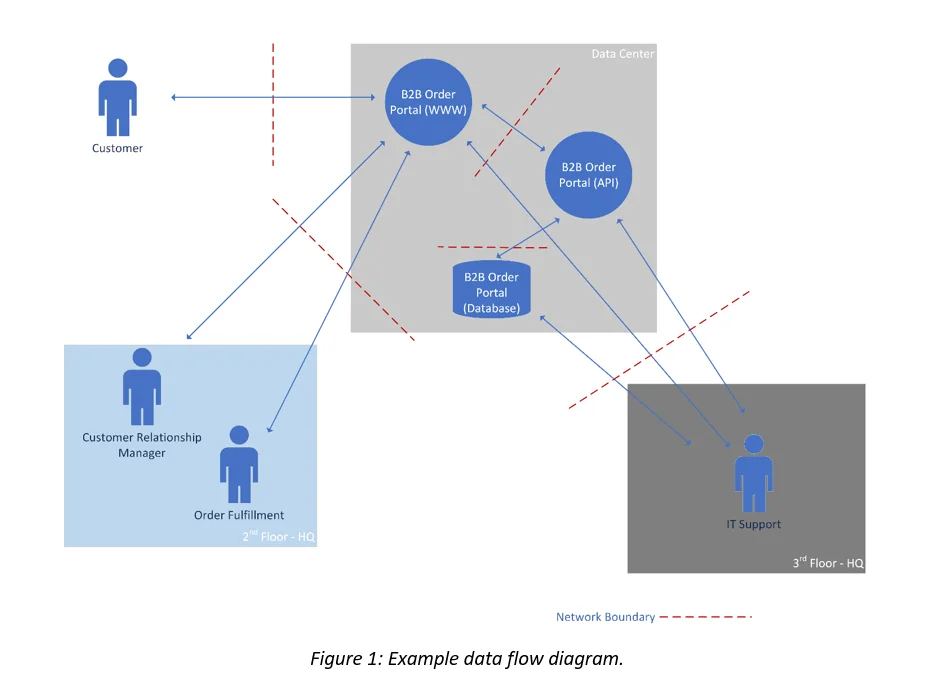
These answers lead us to the final step in the process: follow the CUI.
Wrapping Up
I have read many social media posts asking, "How do I begin to define the scope of a CMMC assessment?" At first, it may appear to be a huge undertaking. For smaller organizations, it may make sense to include all organizational assets within the scope of a CMMC assessment to simplify the management of the technology, information, people, and facilities across your organization. Consolidating the governance and management of these organizational assets to a single standard such as CMMC will reduce confusion and make processes more repeatable by employees who interact with multiple business services, even those not directly governed by a standard such as CMMC.
For medium, large, and even multi-national companies, however, applying CMMC practices and processes across lines of business not governed by CMMC may exceed the business requirements of your other initiatives in terms of time, money, and resources. These organizations should evaluate the use of organizational assets across their lines of business to determine if applying CMMC broadly is feasible. The steps presented above provide these organizations with a manageable approach to identifying the scope of their CMMC assessment.
The SEI is a co-author of the CMMC model and has several resources available to help you better understand the program. Visit the SEI's CMMC web page for more information.
Additional Resources
The CMMC Model and accompanying DoD information is available for download at https://www.acq.osd.mil/cmmc/index.html.
View the SEI webpage CMMC--Securing the DIB Supply Chain.
Download the fact sheet, CMMC--Securing the DIB Supply Chain with the Cybersecurity Maturity Model Certification Process.
Download the SEI Podcast, Documenting Process for CMMC.
Download the SEI Podcast, CMMC Levels 1-3: Going Beyond NIST SP-171.
The DIB SCC CyberAssist site provides resources to assist DIB companies and suppliers of varying sizes with the implementation of cyber protections, and awareness of cyber risk, regulations and accountability for their supply chain.
More By The Author
More In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
PUBLISHED IN
Enterprise Risk and Resilience ManagementGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
