2 Approaches to Risk and Resilience: Asset-Based and Service-Based
Understanding an organization’s risk and resilience posture can be a heavy undertaking. The concept of risk can be overwhelming and leave less mature organizations wondering where to begin and more mature ones struggling to improve their risk management programs. In this blog post, we will discuss the benefits and challenges of two possible approaches to risk and resilience management, one based on an organization’s assets and the other on its services.
Risk and Resilience Overview
Risk and resilience management are significant areas in the SEI’s body of work. The SEI has developed several models for operational resilience, most famously the CERT Resilience Management Model (CERT-RMM). In partnership with the SEI’s sponsors in the Department of Homeland Security and Department of Energy, our staff have performed numerous resilience assessments with critical infrastructure organizations.
There are many definitions of risk, sometimes even within a single organization. I am going to focus on operational risk as defined by the CERT-RMM: “the potential impact on assets and their related services that could result from inadequate or failed internal processes, failures of systems or technology, the deliberate or inadvertent actions of people, or external events.” An organization may face many different kinds of risk, and each presents unique concerns and challenges. However, operational resilience concerns the risks that affect the operation of the organization—those that can put stress on its mission or even bring it to a halt. Managing those operational risks is how an organization becomes more resilient.
Similarly, I will refer to operational resilience, which is “the emergent property of an organization that can continue to carry out its mission in the presence of operational stress and disruption that does not exceed its operational limit.” Achieving resilience can present a real challenge to organizations. Resilience is not a product of any one set of security controls or any particular document, and it can often be very hard to conceptualize.
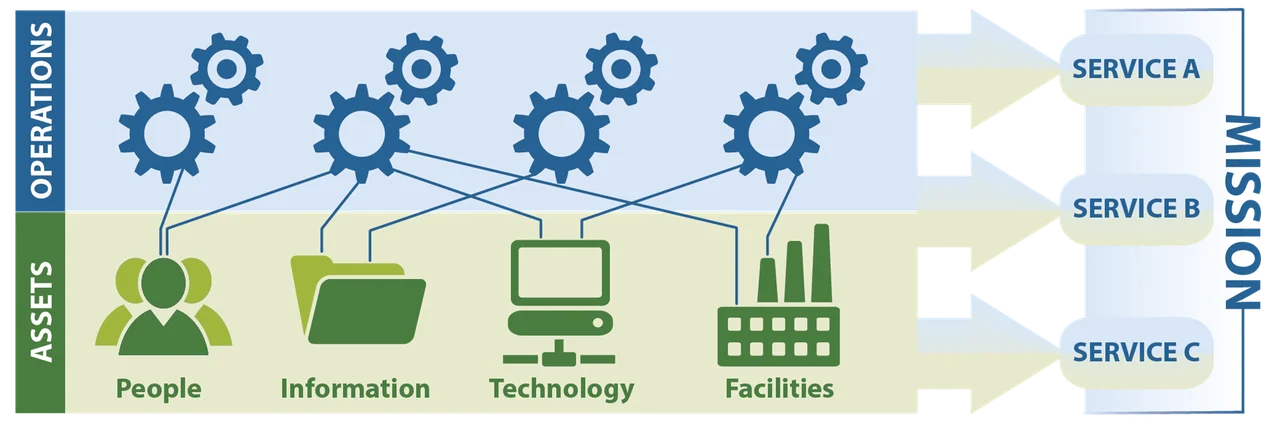
Services and assets are two other terms security professionals should know. The CERT-RMM defines a service as “a set of activities that the organization carries out in the performance of a duty or in the production of a product.” An asset is “something of value to the organization, typically, people, information, technology, and facilities that high-value services rely on.” These definitions are intentionally very broad. I will refine them further, but for now, consider assets to be anything an organization has and services to be anything the organization does. Assets and services are closely linked: services cannot function without assets, and an asset’s value is inherent in the support it offers to services.
Assets and services are at the very heart of an organization’s operations. They provide the foundation for day-to-day business activities, and that makes them a prime focal point for risks to the mission. Organizations may label their risk management foci in a variety of ways, or they might simply have a broad, enterprise-wide focus. Ultimately the activities to manage risk will tend to center around assets, services, or both, even if the organization does not immediately realize it.
The Asset-Based Approach
To increase an organization’s resilience, organizations may choose to focus on the security of individual assets. Those that take this approach will typically start by identifying security categorizations for their assets. They might use a security standard, such as FIPS 199, which categorizes an asset by whether its loss of confidentiality, integrity, or availability would have a low, moderate, or high impact on the organization. Then they will select the proper security controls for each asset based on its categorization. Some organizations may start by performing this exercise with a few of their most important assets and then use the resulting security controls as a foundation for the rest of their enterprise-wide security program.
Benefits: Compliance, Customization, Autonomy
The asset-based approach to resilience can help organizations ensure they are achieving regulatory compliance in regulation-heavy industries, such as health care and finance. These organizations are required to know exactly where they store and process personally identifiable information (PII), protected health information (PHI), or other sensitive information. They know exactly what security controls have been applied to the systems that interact with this information. They can document this information quickly and easily because they probably built their whole security program with those assets in mind and took notes along the way. They can easily compare their own checklists to the compliance standards and identify opportunities to implement controls that exceed those that are prescribed by regulation.
An asset-based approach will likely be more popular with an organization’s asset owners and custodians because it provides them more autonomy. Asset owners often feel that they know the requirements of their assets best, and in many situations this indeed is the case. Allowing asset owners to identify requirements and set security controls for their assets allows them to tailor the specifications to the asset and its business needs.
Many standards and frameworks assume that protection and sustainment is done at the asset level. For example, the NIST Risk Management Framework (RMF) is based on a lifecycle of assigning security categorizations to individual systems, selecting and implementing controls on those systems, and assessing and monitoring the effectiveness of the controls. Federal bodies or organizations that have voluntarily adopted use of the RMF may tend to start their security activities with the authorization of these systems and work outward from there to the rest of their assets.
An asset-focused approach to security may be optimal for organizations that own one or more federal high-value assets (HVAs). According to U.S. policy, these assets, typically information or information systems, are so crucial to the safety of the nation that their security requires additional oversight. Owners of federal HVAs must use specific procedures to categorize these assets, choose security controls for them, and document it all. HVAs are also subject to additional security assessments. These organizations may choose to use their HVAs as their starting point for security and build out from there.
Challenges: Inefficiency, Inadequate Resilience
The primary downside of the asset-based approach is that it may fall short of the overall goal of resilience. The resilience of an asset may improve, but the asset does not exist in a bubble. It is supported by many other organizational assets: people, information, technology, and facilities. Can one of them support the chosen asset in the event of a failure? Can one of them cause or contribute to a failure of the asset? It is likely. Has every single one undergone risk management activities? Unlikely.
Attempting to manage risk at the asset level can lead to inefficiencies in a couple of ways. First, different owners or custodians may handle similar assets differently. One owner may determine that an asset has a high confidentiality rating, and another may decide that a similar asset has a moderate rating. They should be rated similarly, but one of these assets will be over- or under-protected. Working separately, the asset owners might never identify their discrepancy. A more comprehensive approach to asset categorization would reveal this problem, but the asset-based approach to risk management often encourages more compartmentalization, not less.
The asset-based approach can also cause redundant activity. Consider the scenario above, but both asset owners select a moderate security rating and settle on similar security controls. The organization has effectively gone through an identical exercise twice to reach the same result, wasting time and resources.
Another risk of centering on assets during risk and resilience activities is that most attention may be given to technology assets. People and facilities are also crucial pieces of the resilience puzzle, but they tend not to be the focal point of controls and compliance activities. For example, what plans are in place if critical personnel suddenly quit or cannot be reached in an emergency? What if a natural disaster or civil unrest impacts a facility? If asset-focused security becomes siloed in the IT department, the organization may struggle to engage other business units that ultimately share responsibility for the protection and sustainment of the organization’s mission.
The Service-Based Approach
Rather than focus on assets as the center of risk and resilience activities, an organization may instead focus on one or more of their mission-critical services. While this approach will necessarily consider the assets that support these services, the assets are not considered in a vacuum. Instead, the organization determines the assets’ protection and sustainment requirements based on their role in the critical services, and these requirements inform the practices used to secure them.
Benefits: Holistic, Efficient Sustainment of Mission
When fully implemented, a service-based approach can have vast benefits. This approach allows the organization to consider risk and resilience in a holistic manner across its most important functions. Rather than simply considering the protection and sustainment of each asset, a service-based approach considers how assets interact and support each other.
Focusing on the resilience of a whole service can optimize sustainment of the organization’s mission or restore operations in case of a disruption. An asset-centered approach may concentrate effort on sustaining an individual system, only for another asset that supports it to fail. This scenario is less likely if the organization considers the service as a whole, supporting critical assets together and focusing on what really matters: the organization doing what it exists to do.
Focusing on services can also better align activities among business units. Independent security decisions by asset owners and custodians, as in the asset-based approach, can lead to discrepancy and redundancy. With a service-based approach, different parts of the organization work together to determine the appropriate protection and sustainment activities. Their cooperation can reduce gaps in security management among different assets and systems. It can also reduce redundant activities that cost the organization valuable resources.
Challenges: Compliance Burden, Difficult Implementation
A common challenge with basing security practices on services is that most common standards and frameworks do not operate this way. If an organization uses NIST RMF, has a federal HVA, or must show compliance to some other asset-focused program, asset-based resilience directly addresses this need. Compliance can take more work with a service-based approach. Instead of simply checking the compliance of security controls on individual systems, the organization must consider what controls are inherited from existing practices and what additional controls must be applied to show compliance.
Choosing a mission-critical, externally focused service is crucial to getting the most benefit from the service-based approach to resilience. Many organizations mistakenly choose internal functions or critical assets, such as “IT” or “the database,” as a service. Doing so negates the benefit of using the service-based approach, as it unintentionally drives the focus either back to the asset level or toward internal services that are not the crux of the organization’s mission. These components may make up important parts of the organization’s mission, but protecting and sustaining them alone will not ensure resilience of the critical service and thus the mission itself. The selected services should be specific, critical activities of the utmost importance to achieving the organization’s mission.
Specific services will vary wildly between organizations of different sectors. Wastewater treatment might be a critical service to a water company, but a financial services company might identify consumer banking. Large or complex organizations will have multiple key services that require consideration for resilience. The day-to-day activities of these services may overlap, be fully separated, or somewhere in between. Once an organization begins to consider all the components that support this service, the internal, secondary services (such as IT and payroll) emerge. Identifying critical services can be highly involved and may not be intuitive to smaller organizations or those with less mature risk management programs.
Finally, the service-based approach requires that the organization not be siloed and that lines of communication are open between different business units. This structure necessarily takes away some autonomy from system owners and individual business units and may introduce some additional steps in the decision-making process. The service-based approach may require some process changes in how the different parts of the organization interact. This approach may force the organization to fundamentally rethink how its units communicate and work together. Growth and change can be painful, but it ultimately makes the organization stronger.
What Is the Best Approach?
When evaluating risk and resilience activities, is it better to base the approach on assets or services? It may not come down to choosing one universal approach, but rather knowing which one to use in what circumstance.
In general, focusing on services tends to be more conducive to true resilience. Resilience is not a product to buy and use, nor is it a test to run at the push of a button. Resilience emerges from holistic activities across an organization, and these are best done with the mission of the organization in mind. Using a service-based approach ensures that the organization is focusing its efforts on the most important activities.
Ultimately, a hybrid of both approaches is typically the best situation, though it can present some challenges. It will look different for each organization. Large and complex organizations should ideally use a service-based approach to ensure the resilience of their mission-critical services while also evaluating whether their individual assets require any special controls for compliance or regulatory purposes. Other organizations, particularly those with small or less mature risk and resilience programs, using an asset-based approach may wish to begin shifting their organization’s mindset toward a service focus gradually.
Using both approaches together will require a great deal of communication within the organization—and that is a good thing. Resilience, security, and risk management all demand effective business communication. Sharing strategies for risk and resilience across the business can be a great way to begin conversations about security and strengthen the posture of the organization.
Additional Resources
For more of the SEI’s research on organizational resilience, check out our other blog posts on this topic or explore the CERT-RMM.
More By The Author
More In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
