Security Begins at the Home Router
PUBLISHED IN
Reverse Engineering for Malware AnalysisIn recent days, the VPNFilter malware has attracted attention, much of it in the wake of a May 25 public service announcement from the FBI, as well as a number of announcements from vendors and security companies. In this blog post, I examine the VPNFilter malware attack by analyzing the vulnerabilities at play, how they were exploited, and the impact on the Internet. I also outline recommendations for the next generation of small Internet of Things (IoT) device manufacturers, including home routers, which were the target of VPNFilter malware. Because this post also emphasizes the prioritization of vulnerabilities that have significant or large-scale impact, I will recap recommendations made in the March 2017 blog post on the Mirai botnet.
A Tale of Vulnerabilities
Cisco's threat blog post on VPNFilter provides details on the devices impacted by this vulnerability, which affected "at least 500K networking devices worldwide." VPNFilter in some ways is like Mirai in that it targets IoT devices, specifically home routers. It is also now known that Mirai botnet was powered by four zero-day exploits apart from the typical password guessing method of compromising small IoT devices. Even recently a newer version of Mirai botnet was discovered by Palo Alto networks that target home routers.
Among the reported router vendors impacted by VPNFilter, Linksys and Netgear caught my attention because, according to Statistica, these popular home routers make up 77 percent of the home router market. By exploring typical vulnerabilities using these two highly popular devices in the home market, I was able to define some broad recommendations that will reduce the risk from such unmanaged and unnoticed devices.
The SEI's CERT Division has been working with many vendors of home networking devices to identify and track vulnerabilities. This collaborative work aims to reduce the impact of such vulnerabilities on the larger Internet.
In the diagram below, I have captured and categorized vulnerabilities that were likely to be exploited on these devices. Many of the compromises also take advantage of typical default credentials on these IoT devices. Hackers exploit these vulnerabilities as part of their toolkit to expand their footprint of compromised devices.
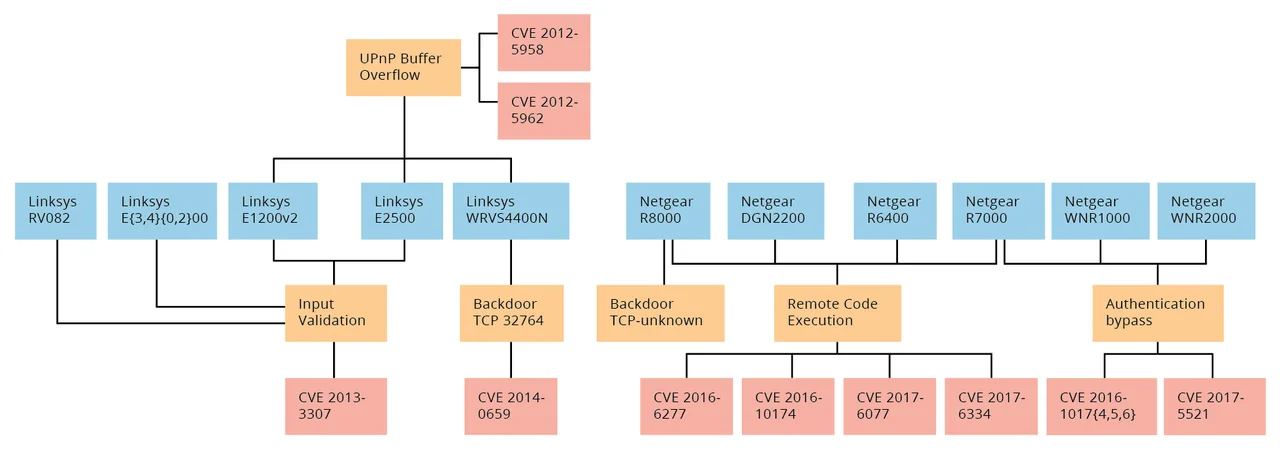
In its Vulnerability Notes Database, the CERT Vulnerability Coordination Center has published at least two significant router vulnerabilities that broadly impact these two major providers:
- Multiple buffer overflow vulnerabilities in multiple routers. A popular library used by multiple router vendors exhibits a buffer overflow vulnerability that can be used to compromise a router and install arbitrary programs.
- Arbitrary remote command injection vulnerabilities in Netgear. Multiple Netgear routers are vulnerable to remotely executed arbitrary commands.
These vulnerabilities can be traced to a number of exploits that are publicly available at http://www.exploit-db.com. In some ways, they demonstrate that software in these types of devices likely contains remotely exploitable weaknesses. While secure coding is important to mitigating these weaknesses, software vulnerabilities in mass-produced, quick-to-market devices are hard to eliminate. We believe that vulnerability coordination and mitigation to address and recover from these weaknesses are essential activities in making the Internet reliable and secure. More can be done, however, to ensure such weaknesses do not sustain the ongoing compromise and abuse prevalent in the Internet today.
The Problem of Close-to-Infinite Uptime
I suspect that if I asked the readers of this post to tell me when they last rebooted their home router, many would stop reading to go reboot their device. The close-to-infinite uptime of today's home routers gives an edge to attackers, who can exploit such uninterrupted uptime and maintain long-term access to a compromised system, as detailed in the popular five phases of hacking model. In fact, the Mirai botnet's malware and VPNFIlter stage-2 malware both are non-persistent malicious code that will not survive in the event of a reboot. This fact indicates attackers are confident that these devices will not be rebooted for a long time.
The Role of Sloppy Software Maintenance
The second factor that makes the home router susceptible to compromise is lack of patching or updating. Updating a home router typically requires a reboot and likely a brief interruption of service. Many home users never reboot their router as they depend on daily, uninterrupted service to the Internet for resources such as media, video, and e even education. In many developing countries where routers are bundled through the Internet service provider (ISP), the ISP recommends that the user not update the device to avoid incompatibility issues. In other locations, where bring your own device (BYOD) has been popularized, ISP's are not able to control what the consumers use as customer premise equipment (CPE) devices. When I visited Cote d'Ivoire recently for a class on DDoS and botnets, representatives from the ISPs explained that popular devices in their customer homes are cheap and may even include unknown models that the ISP will not be able update or change. Here is yet another reason that these devices are poorly managed and never get required updates or security fixes.
The Call to Action
In my earlier Mirai blog post, I offered some guidelines that are both practical and achievable in the home router and IoT device market. My hope with the following guidelines is to inspire innovative technical solutions among device vendors and service providers to redesign or update home routers to limit the risk that these devices will end up being used for nefarious purposes:
- Design home routers and IoT devices to operate with read-only filesystems, making run-time installations of malware impractical.
- Disable any packet crafting/spoofing/promiscuous mode on the firmware level to avoid malicious use of network resource on these devices.
- Provide automated updates for firmware with either planned downtime or no downtime to resolve vulnerabilities proactively.
The purpose of these lightweight, low-cost devices is to transit network data or stream live data (like IP cameras) with little reason for any persistence. In fact, some of the newer home routers do operate within a chroot and a read-only file system, making it hard to both exploit these devices and install third-party software for persistence. Even if a would-be attacker learns or guesses an administrative password, malicious code installation performed by VPNFilter and Mirai would not be successful on these devices.
In both cases, the malware is designed to take full control of the network stack, allowing packet crafting, spoofing, interception, and the ability to achieve full-listening promiscuous mode on the infected devices. These capabilities in these lightweight devices are not required or useful in most cases. Eliminating this abuse of promiscuous mode entirely will prevent compromised systems from being used for nefarious purposes, such as DDoS attacks, malware installation, intercepting communications, and modifying network packets.
Other Recommendations
In addition to my recommendations above, I have other practical recommendations that can help both device vendors and service providers consider more options for actively resolving vulnerabilities. Automated updates have been introduced on many devices, and they have become an essential part of smartphones, tablets, and PCs. Some of these updates are now being performed without any interruption of service to the customer.
In cases where a service interruption (such as reboot) is needed, the user should be able to request a preferable time period, such as midnight in the local time zone or a weekend, to ensure minimal service interruption. This type of update capability is essential for devices such as home routers and IoT devices. If vendors and service providers can innovate to provide incremental updates that require no reboots, and if they can further implement newer methods, such as live patching (kpatch), to update a vulnerable system, more home users can transparently receive newer security features and any related performance gains. In cases where a reboot is required, either due to security or non-availability of dynamic software updating features, vendors and service providers can provide their customers with whichever choice causes the least impact, thereby giving users friendly ways to keep their device up to date.
Recommendations for Consumers
If you are consumer reading this article, our first and most pressing recommendation is that you change default credentials on your home router. Next, update, maintain, and reboot your home router and the IoT devices in your home. A weekly reboot of your home router is not too burdensome and may even improve its performance. If you enjoy a well-secured home, don't forgot to digitally reinforce your home security, beginning with your home router.
Additional Resources
Read my earlier blog post, Powered by Mirai.
More By The Author
More In Reverse Engineering for Malware Analysis
PUBLISHED IN
Reverse Engineering for Malware AnalysisGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Reverse Engineering for Malware Analysis
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
