Powered by Mirai
Distributed denial-of-service (DDoS) attacks have been dominating the IT security headlines. A flurry of reporting followed the September 2016 attack on the computer security reporter Brian Krebs's web site KrebsonSecurity when he reported attack traffic that was at the unprecedented scale of gigabytes per second. In November, my colleague Rachel Kartch wrote "DDOS Attacks: Four Best Practices for Prevention and Response," outlining what we can do to defend against these attacks. In this blog post, I tell the story of the Mirai powered botnet that's been harnessed in some of these recent attacks and which has also received its own share of press. My purpose is to explore the vulnerabilities that Mirai exploits and describe some simple practices that could help transform our Internet devices to mitigate the risk posed by botnets.
The botnets that power Mirai malware have three components: a client software that connects to a server and downloads the attack plan, a set of attack methodologies, and a network scanner that searches and attempts to log into devices. Mirai operates on a very large scale and has been involved in a series of large-scale DDoS attacks like the one referenced above. Let me get right to the story.
Although Mirai is Japanese for "the future," my observations start about 10 years ago in Bangalore--the Silicon Valley of India. I had just moved back to India after living out of the country for more than 20 years, and I was in for a few surprises. The one I want to highlight here was getting my home Internet connection with a local Internet Service Provider (ISP). The ISP sent a broadband employee to our house to install our asymmetric digital subscriber line (ADSL) Internet connection. It took a few hours, and the technician left me with a working 512-Kbps connection and a Beetel modem.
The Beetel router at my home was a full-fledged Linux router with a BusyBox shell--an all-purpose utility for Linux devices. I found that this router could be reconfigured with a single web request to do almost anything you can do on a Linux box with a "root" account and even get into the BusyBox shell. The access was protected by a default password. That is, anyone could reconfigure the router over the Internet.
Let's fast forward to today. Recently, I started working with a National Security Information Exchange working group to analyze the Mirai malware and the DDoS botnets that are powered by it. A valuable asset for this analysis was provided by a large US-based ISP in the form of scan data from October 2016 to January 2017. Apart from analyzing the released version of the malicious software source code, this scan data helped us perform a longitudinal study on the malware's footprint, its foundational growth, and the current and future potential of the malware.
About the Data
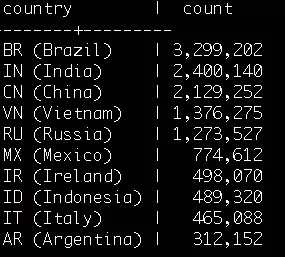
The à -la-carte scan data contained approximately 1.8 billion rows of de-duplicated scan attempts initiated by Mirai-compromised devices from October 2016 to Januray 2017. The data revealed the scan activity to have peaked on October 25, 2016. The data included 16,521,589 unique IP addresses of Mirai-compromised scanners, yes approximately 16 million. Note that this was not the number of botnet-compromised machines. A thorough analysis of a revolving 24-hour cycle shows the botnet size to be around 1.7 million compromised devices. The sources included machines in more than 190 countries around the world, with top countries being Brazil, India, China, Vietnam, and Russia in that order.
"Join the Dark Side and Clone Yourself, Router" - from the Command Center
Remember my Beetel router, and its single vector to compromise? What if I was a bad guy who wanted to easily maintain an army of devices to use for DDoS attacks? A router like my Beetel is the perfect conscript. Routers hardly get turned off and are always connected to the Internet. Even my Beetel router in Bangalore was connected to a surge protector and an uninterruptible power supply (UPS)--the router got hot but never got turned off. This router is an ideal place to install reliable malware that can clone itself and spread malware to other devices (like the Cuis clone, for Star Wars fans). What follows is what I found in the data shared by the large US ISP.
After randomly picking a number of the compromised devices spreading Mirai malware, I found most of them (80 percent) to be routers (also known as customer premises equipment or CPE), followed by closed-circuit television cameras and digital video recorders. For me the surprise was the number of routers that were compromised, while the focus has been on the newer problem with the Internet of Things (IoT) devices. For this analysis I used the Shodan.io data source on fingerprints of connected devices to detect if the compromised device was either a router or an IoT device that could be behind the router.
Pythagoras, Help Us
It is always a challenge to find patterns in large data sets such as 16 million IP addresses that span almost every country and every type of network. However, I am a fan of doing simple math with data to find aggregate information and recognize patterns in the data. My research on these techniques fell into a surprisingly simple machine-learning area of math called "clustering using Euclidean distance." This is a basic expansion of the Pythagorean theorem to calculate the distance between two points. Shown below is a simple calculation of the distance between two points.
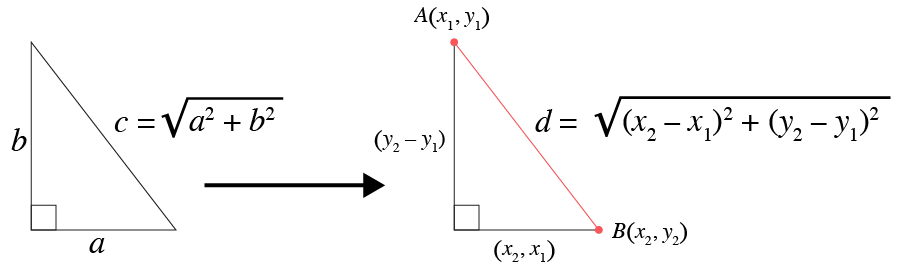
Euclidean distance expands this calculation to include any n number of dimensions, as shown in the formula below.
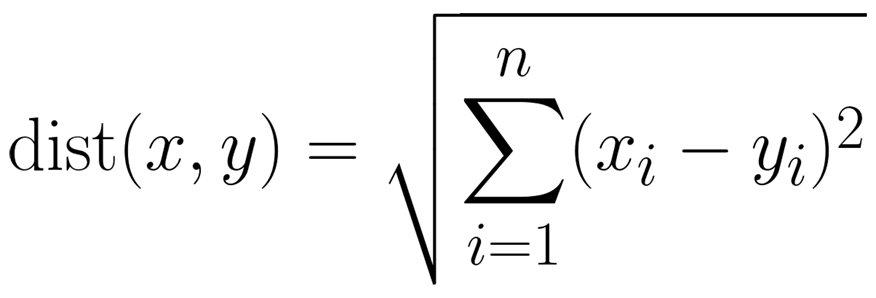
All you have to do is find n dimensions to represent each IP address and find if they "cluster" with some common properties. The rules are simple: Each dimension must be represented by a number and have a meaningful value and a meaningful distance. I picked dimensions to represent each IP address as follows: geolocation latitude; geolocation longitude; the IP address's Autonomous System Number (ASN, treating newer ASNs as newer networks); country's Gross Domestic Product (GDP; to represent the country name as a number); and the number of times an IP address appeared (frequency of scan).
I could add other dimensions, such as number of ports open or exploitable vulnerabilities present, to expand this analysis using Euclidean distance clustering. I found that the scans contained some interesting pointers. Active Mirai-compromised machines clustered around two interesting trends:
- newer ASNs
- lower GDP countries
The newer ASNs can generally be attributed to newer ISPs with what can be assumed as less maturity. The clustering map below shows that the highest concentrations are around Vietnam and the nearby Southeast Asia, followed by Brazil and then India.
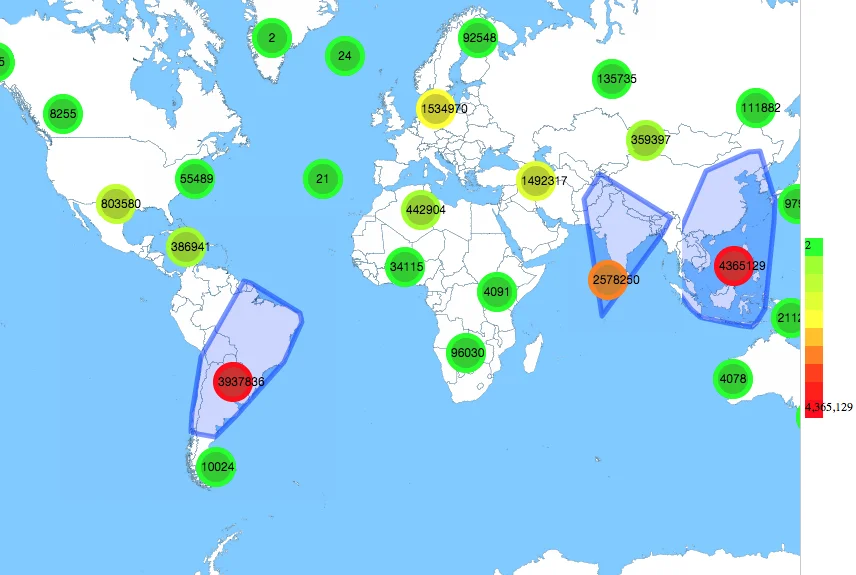
The low-cost routers seem to provide a very large base or foundational entry point to Mirai malware to compromise devices. The black-box routers available at very low cost from ISP providers in these regions are easy targets. The situation is comparable to a "tragedy of the commons" situation as we add more devices that get unintentionally abused for such nefarious activities as DDoS. Below I want to highlight two popular router models in Southeast Asia that have open vulnerabilities that make them easy to compromise:
Beating the Same Old Drum but Adding a New Rhythm
Although the IoT's lack of security is well known, I would like reconsider the age-old problem of routers and expand its approach to the IoT as a feasible solution for our way ahead. As recently as 2014, CERT researchers published a white paper, "Abuse of Customer Premise Equipment and Recommended Actions," that provided basic recommended actions to mitigate the threats inherent in CPEs. The SEI's CERT Division also systematically documents vulnerabilities on CPE devices, which enables vendor coordination to close the gaps that create these vulnerabilities.
Apart from following some basic best practices for CPE devices like routers (such as not allowing management access from external networks or interfaces), I would also recommend the following to device manufacturers and ISPs that bundle CPE devices:
- Use a simpler, read-only file system for these devices, crippling the installation of ad hoc software (or a read-only BusyBox shell if a command-line shell is at all needed).
- Disable packet crafting and spoofing at the operating system or kernel level, making it harder to abuse these devices.
While these changes would not be silver bullets, they will make it harder for botnet operators to develop malware that would enable Mirai to enlist these devices into botnets. We can easily translate what we have learned about hardening routers to IoT devices. These small technical changes would have a significant impact relative to their cost with virtually no additional burden placed on Internet providers or consumers.
Additional Resources
Read the paper "Abuse of Customer Premise Equipment and Recommended Actions" by Paul Vixie, Chris King, and Jonathan Spring.
See the video presentation at BlackHat (August 2012) : https://www.youtube.com/watch?v=0duYxPIx8gU by Craig Heiffner.
Read the Ars Technica article "Backdoor in wireless DSL routers lets attacker reset router, get admin" by Sean Gallagher.
More By The Authors
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


