Insider Threat Incidents: Assets Targeted by Malicious Insiders
As part of the CERT National Insider Threat Center's ongoing efforts to refine and improve our Incident Corpus, and to provide more data to the community, we have updated our taxonomy for targeted assets in insider threat incidents. We have identified a number of dimensions--asset owner, asset type, and classification--we can use to aggregate and analyze targets of insider threat incidents. In this blog post, I detail this new taxonomy and highlight some of our latest findings about the assets targeted by malicious insiders.
The diagram below shows the dimensions of the CERT Insider Threat Incident Corpus target taxonomy.
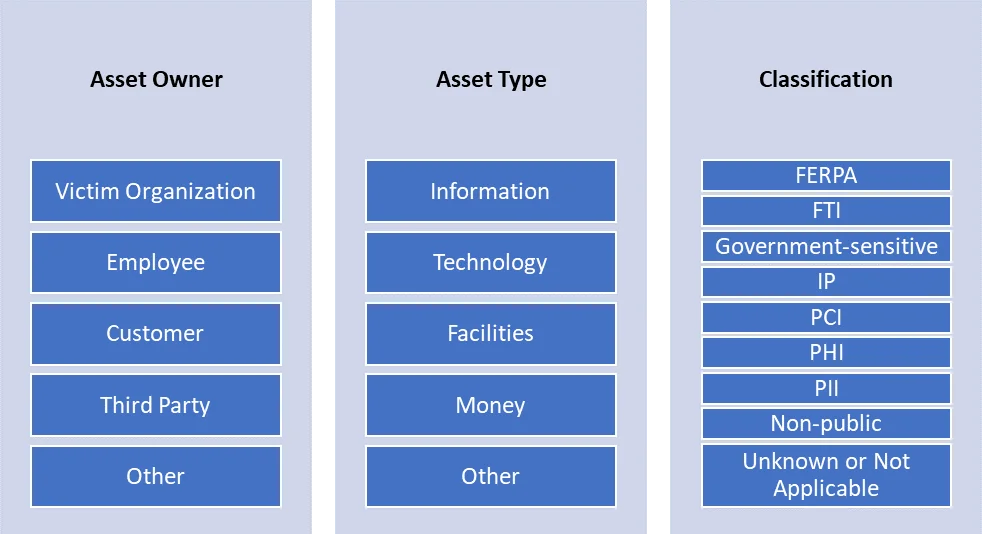
Asset Owner
The asset owner corresponds to the entity responsible for an asset's management or to the subject of the asset. For example, the employee would be the owner of their data saved on employer systems, such as human resources information or personal files saved on work devices. The customer would be the owner of customer payment information. The asset owner categories are informed by the CERT Resilience Management Model (CERT-RMM) Asset Definition and Management (ADM) domain.
Perhaps unsurprisingly, the most common asset owner across insider threat case types--fraud, theft of IP, sabotage, and multiple--is the victim organization. Consumer assets are targeted nearly half as often. We observed far fewer targeted assets owned by employees, third parties, or others. The graph below shows the assets in the CERT Insider Threat Incident Corpus, broken down by owner and case type.
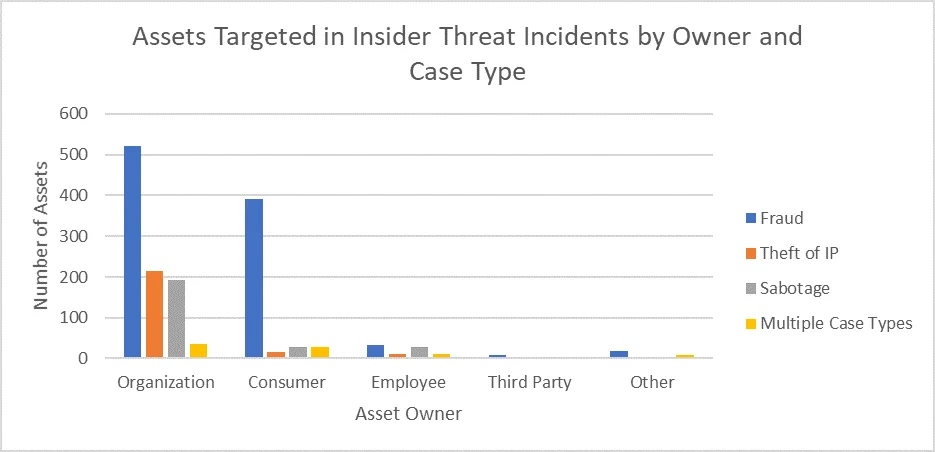
Fraud incidents, which make up the majority of incidents in the corpus, were associated with the greatest number of targeted assets, owned primarily by organizations and secondarily by consumers.
Asset Type
The asset type is the medium in which the asset exists.
Unlike the CERT-RMM ADM domain, our taxonomy includes money as an asset type. The CERT Insider Threat Incident Corpus includes many fraud incidents, so identifying money as a unique asset helps to highlight the actual intent of these incidents. Also, our asset taxonomy does not include people, which is an asset type in the CERT-RMM. In scenarios where an insider used social engineering on a coworker, we would identify the target asset as the asset that the insider wanted to access through the coworker, not the coworker.
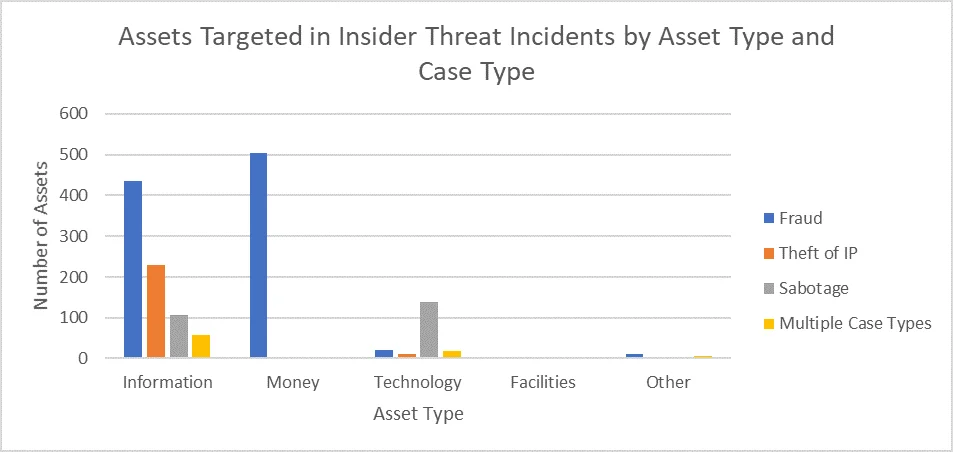
As seen in the graph below, information is the most commonly targeted asset type across all types of incidents. Money is targeted exclusively in fraud incidents. Information is the most commonly targeted asset across all incident types. We have identified few instances where a victim organization's facilities were targeted.
Classification
The classifications used in our asset taxonomy refer to specific kinds of sensitive data, but not national security information designated as "classified" by the federal government. This dimension refers to any protections or designations that would be afforded to the asset. Our insider threat asset classifications include the following categories:
- Family Educational Rights and Privacy Act (FERPA): refers to the type of data, such as student education records, protected by the FERPA federal law
- Federal Tax Information (FTI): a regulated class of information, with specific guidance provided by Internal Revenue Service (IRS) Publication 1075. This classification would be seen in federal, state, or local government organizations.
- Government-sensitive data: any data that is not classified but is otherwise sensitive and managed by a government entity. This may also include law enforcement sensitive information.
- Intellectual property (IP): can refer to a number of different kinds of assets, but is that which could be protected via patent, copyright, trademark, etc.
- Payment card information (PCI): any account information or other personally identifiable information (PII) associated with a payment transaction, or the storage of such data. Organizations would need to follow the Payment Card Industry Data Security Standard (PCI DSS) if they were a processor of such data.
- Protected health information (PHI): information subject to the protections of the Health Information Portability and Accountability Act (HIPAA), if the organization was a covered entity
- Personally identifiable information (PII): information about a person (or persons) that, when used alone or in combination, can be used to identify a specific person. Common examples of PII include identifiers like name, birthdate, and Social Security Number (SSN). PII, for our purposes, refers to identifiers not better described as PCI or PHI.
- Non-public: generally, data involved in insider threat incidents where other classifications do not apply
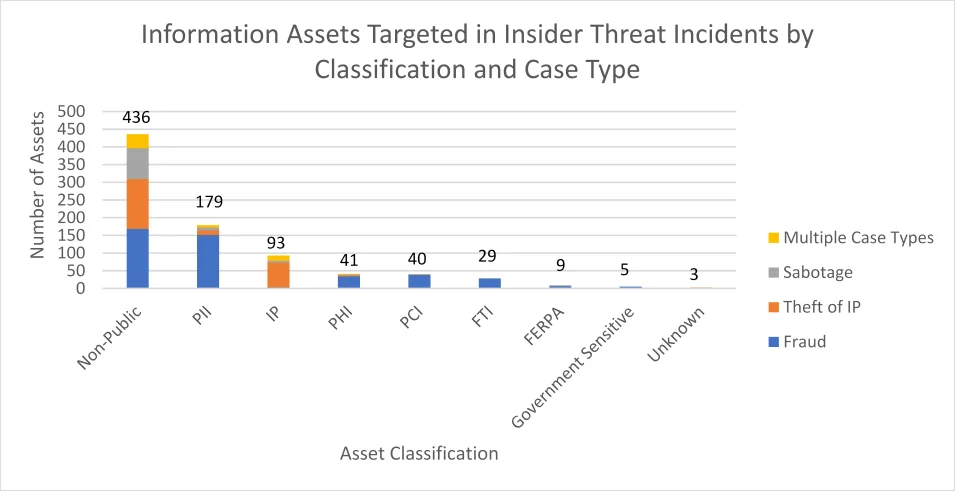
The graph below shows targeted information assets only, broken down by classification and known incident type. The most commonly identified classification was non-public. Rarely was FERPA information impacted, reflecting the small number of incidents in our corpus affecting the education sector.
Specific Assets
The fourth, less rigid, dimension of our taxonomy is the specific asset or assets targeted by the insider. Out of 1,643 total targets across 1,262 insider incidents, we have identified 105 specific assets. Here are some examples.
- Company funds, part of the "money" asset type. Company funds were exclusively targeted in fraud incidents and accounted for 11.9% of all targeted assets.
- Proprietary information was the most common target of theft-of-IP incidents, but it was also targeted across all case types. Proprietary information accounted for 3.7% of all targeted assets.
- Product information, which the taxonomy would classify as intellectual property, was also a common target in thefts of IP. It was also targeted across case types and accounted for 3.7% of all targeted assets.
- Computer systems were the primary target of IT sabotage incidents, but they were targeted across all case types. Computer systems accounted for 2.5% of all targeted assets.
As seen in the graph below, insiders targeted between 1 and 10 assets per incident.
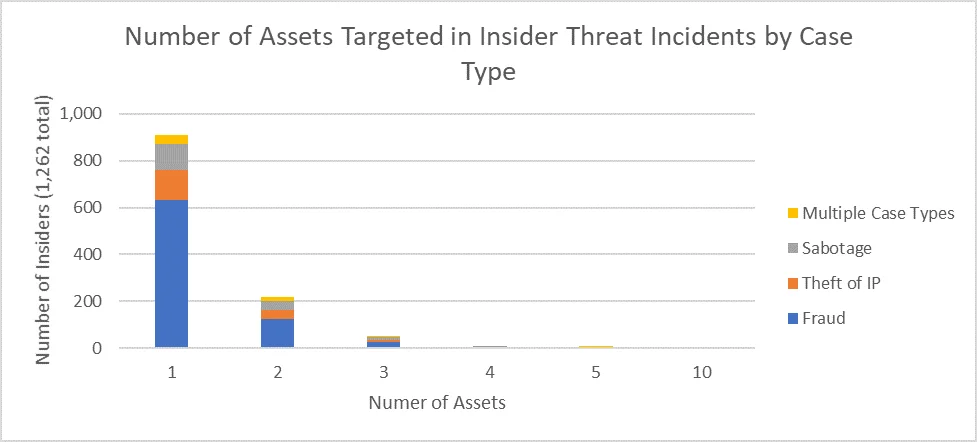
Over three-quarters (76.2%) of insiders targeted only one asset. Less than one-fifth (17.8%) of insiders targeted two assets. Approximately 1 in 20 (5.2%) insiders targeted three assets or more. Only one insider, in a theft-of-IP incident, targeted as many as 10 assets.
The most commonly targeted assets in fraud incidents were company funds (193 targets, 24.6% of fraud incidents), PII (141 targets, 18.0%), and issued checks (137 targets, 17.5%). Given the nature of fraud incidents, there may have been only one kind of asset targeted, but these assets may have involved multiple records or instances.
The most commonly targeted assets in theft-of-IP incidents were proprietary information (42 targets, 23.7%), product information (39 targets, 22.0%), business plans (26 targets, 14.7%), and source code (20 targets, 11.3%).
The most commonly targeted assets in sabotage incidents were computer systems (27 targets, 15.9%), servers (20 targets, 11.8%), passwords (18 targets, 10.6%), files (15 targets, 8.8%), and data (15 targets, 8.8%).
Protect Your Assets
Organizations can leverage the CERT-RMM and similar frameworks to help categorize and classify their data, which can inform insider risk management activities. Check out the CERT Division's OCTAVE FORTE and OCTAVE Allegro methods for managing information security risks. Learn more about how you can leverage the OCTAVE FORTE process for scoping your insider threat program and assessing insider risk in our presentation from the 2019 RSA Conference.
For questions about the CERT Insider Threat Incident Corpus, contact us at insider-threat-feedback@cert.org.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
