Microcosm: A Secure DevOps Pipeline as Code
Separate: useful. Together: invaluable.
Using six separate virtual machines, Microcosm creates a secure DevOps pipeline using infrastructure as code with Vagrant and Chef. All virtual machines separate act as integral pieces of the DevOps pipeline that are useful tools on their own. When used collectively, however, these services create a continuous integration and continuous deployment platform that takes advantage of security automation and implements secure DevOps best practices.
The Microcosm pipeline provides a wiki service for team collaboration, a code repository for version control, and a chat bot to integrate with ChatOps services. Incorporating threat modeling during requirements determination, hardening environments, conducting security-focused code reviews, and automating security testing through continuous-integration builds throughout the SDLC helps to create a security foundation in any DevOps pipeline.
Using the provided GitHub repository, a user will be able to issue a simple "vagrant up" command to build and provision the following:
Secure Environment and Continuous, Automated Security Testing
The following secure DevOps pipeline diagram includes a workflow and a series of best practices. Each Secure DevOps Best Practice is represented by a lock with accompanying red text. Notice that "Secure/Hardened Environments" is the secure DevOps best practices at the project configuration phase. Microcosm uses a custom Vagrant base box as opposed to a publicly available Vagrant box for every virtual machine. The specifications of the custom Vagrant base box comply and adhere to any information security policies that an organization may have (Tim Palko's Vagrant Box Wrangling post explains this concept in its entirety).
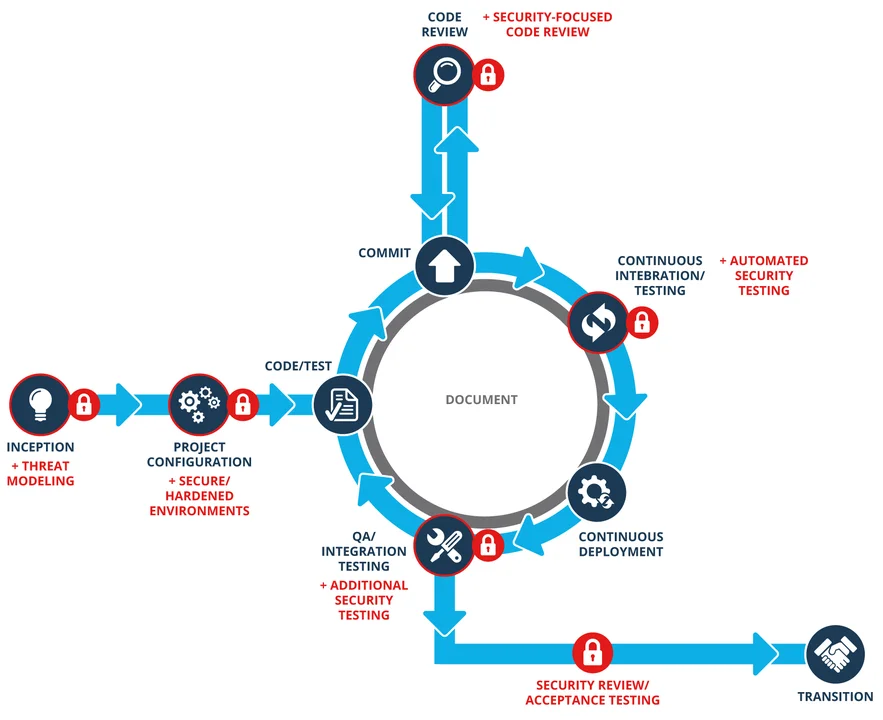
Next, by taking advantage of the official OwaspZap plugin for Jenkins and addressing the fourth secure DevOps best practice, Automated Security Testing, Microcosm provides the foundation to automate security testing by running Selenium functionality tests through the OwaspZap Attack Proxy as part of Jenkins continuous integration builds. This foundation enables automated penetration testing of a web application to occur alongside automated functionality testing for different specified browsers. Allowing the results of scans from OwaspZap to be included as pass/fail criteria for part of daily Jenkins builds will help to ensure that insecure versions of a web application are not built and pushed further along in the DevOps pipeline.
Additionally, Microcosm provides a GitLab server for developers to manage project code, a Mediawiki server with the Bugzilla issue tracking service, as well as the Hubot chat bot which can integrate with many popular ChatOps software, such as HipChat or Slack. ChatOps is crucial to DevOps because it allows development, operations, and security teams to remove communication silos and smoothly make the cultural shift to constant, open communication.
Although these services aren't primarily intended for security enhancement, they do offer some features that address security. GitLab utilizes Security Priority Labels, which have a likelihood/impact rating of 1-3 (with 1 being the most severe), that allow team members to appropriately tag bugs or feature proposals while addressing security concerns. For example, a bug tagged with a level 1 likelihood/impact rating could symbolize that the bug is causing the application to be vulnerable to SQL injection or remote code execution. GitLab can also be configured to notify relevant project managers or team leads, ensuring that the bug is considered a top priority for the current sprint. Moreover, the Hubot chat bot offers an available hubot-script called hubot-auth that assigns roles to users and restricts command access in other hubot-scripts. This access control feature helps ensure that only authorized users are permitted to execute certain hubot-scripts.
Conclusion
The Microcosm suite of prebuilt and pre-provisioned virtual machines can act as a great learning tool for anyone who is interested in learning about continuous integration and continuous deployment with security as a priority. Taking advantage of the secure DevOps best practices that are addressed through the use of custom Vagrant base boxes and continuous, automated penetration testing will help to ensure that vulnerable versions of an application are caught and addressed by information security and developer teams before it is deployed to the staging environment. Looking forward, we're excited to continue our blog post series on addressing security throughout the DevOps process as "Security as Code" in an automated fashion.
Additional Resources
To view the webinar DevOps Panel Discussion featuring Kevin Fall, Hasan Yasar, and Joseph D. Yankel, please click here.
To view the webinar Culture Shock: Unlocking DevOps with Collaboration and Communication with Aaron Volkmann and Todd Waits please click here.
To view the webinar What DevOps is Not! with Hasan Yasar and C. Aaron Cois, please click here.
To listen to the podcast DevOps--Transform Development and Operations for Fast, Secure Deployments featuring Gene Kim and Julia Allen, please click here.
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
