Theft of Intellectual Property and Tips for Prevention
PUBLISHED IN
Insider ThreatOne of the most damaging ways an insider can compromise an organization is by stealing its intellectual property (IP). An organization cannot underestimate the value of its secrets, product plans, and customer lists. In our recent publication, An Analysis of Technical Observations in Insider Theft of Intellectual Property Cases, we took a critical look at the technical aspects of cases in which insiders who stole IP from their organization. Insiders commit these crimes for various reasons such as for the benefit of another entity, to gain a competitive business advantage, to start a competing organization or firm, or for the personal financial gain. By understanding the specific technical methods that insiders use to steal information, organizations can consider gaps in their network implementation and can identify ways to improve controls that protect their IP.
Technical discussions of IP theft are helpful for operational staff to understand how an insider can compromise their organization. Additionally, organizations should always attempt to better understand the human behavioral elements of insider crimes. The report, A Preliminary Model of Insider Theft of Intellectual Property details two preliminary models of behavior associated with insider theft of IP.
The table below identifies types of assets that were attacked in a sample of 50 cases from our 85 total theft of IP cases.
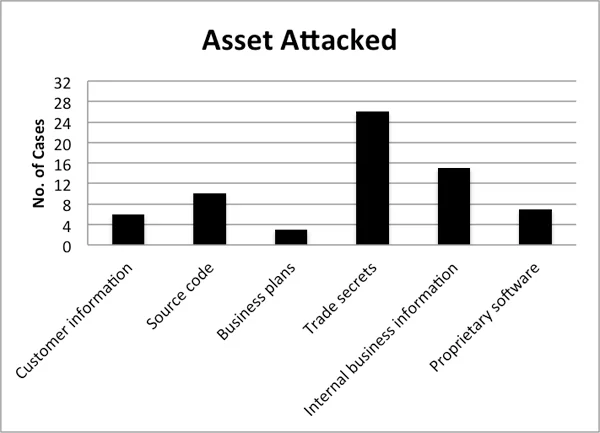
It is clear that trade secrets and internal business information are the most frequently attacked assets. Included in the trade secret and internal business categories, we see assets such as future product designs, customer/price lists, and internal policies not intended for public consumption. These results might seem surprising, especially the relatively low number of customer information items stolen. Personal information such as social security numbers or health records is generally considered to be personally identifiable information (PII) rather than intellectual property. Theft of PII is classified as insider fraud in our database and is thus out of scope for this analysis.
We also found that in more than half of the theft of IP cases we analyzed, use (or misuse) of the network was the primary method of exfiltration. In 32 cases where the network was the primary vehicle for getting the data out of the organization, approximately 50% involved insiders using their corporate email accounts to send data off to personal email accounts, competitors, and foreign governments. Organizations should strongly consider reviewing the monitoring capabilities they use with respect to email, particularly those being sent to suspect recipients. Conversely, the least utilized network channels involved more technically complex crimes, such as setting up covert channels over ssh or other improperly blocked/filtered channels outside the network to move data off of internal servers.
Our study indicated that the most common method of physical exfiltration of data was removable media. Prior to 2005, the most common removable medium was writable CD. However, recent incidents indicate that removable USB mass storage devices like thumb drives and external hard disks are now more popular. USB devices have a much greater storage capacity than CDs, which makes it easier for insider to move their entire desired data set at once.
What can organizations do about these problems? First, they can always consider the role of best practices and established standards in defending against insider attacks. Insider attacks frequently exploit policies or controls that are covered in accepted best practices for IT system security. Second, organizations should always consider more than just the technical aspects of the crime. In a recent report Deriving Candidate Technical Controls and Indicators of Insider Attack from Socio-Technical Models and Data, we examined the importance of creating technical indicators for behavioral actions so that we can gain a more complete understanding of how to defend against insider crimes. Organizations should pay specific attention to these technical vulnerabilities while they attempt to understand what controls are practical to put in place for removable media in the organization. If removable media is necessary to keep operations moving, an organization may want to establish technical measures to limit which machines allow use of removable media, take an inventory of authorized media, and implement some measure of physical security to prevent removal or introduction of new uninventoried devices from the facility. When considering network security, organization should attempt to identify suspicious email communications (particularly with attachments) to direct competitors, foreign governments, or other illegitimate recipients of corporate mail. Organizations should consider using a log aggregation and indexing tool to look for patterns in behavior that might warrant further investigation. This is especially true during major organizational events that may cause stress among employees, such as mergers, downsizing, acquisitions, or reorganizations. These events could possibly influence employee behavior in a negative way, and a heightened awareness of security might be necessary.
If you have questions, comments, or cases to share, please contact us using the feedback link. We are interested in hearing more about what your organization has done about these problems and how well the approaches have worked. Operational feedback helps direct our work, so your contributions and feedback are valuable. All responses will remain confidential, and no data that you share will ever be released or included in future reports.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed