Technical Detection of Intended Violence: Workplace Violence as an Insider Threat
The threat of insiders causing physical harm to fellow employees or themselves at an organization is real. In 2015 and 2016 alone, there were shootings in the U.S. by current or former employees in various workplaces, including at a television station in Virginia, a mowing equipment manufacturer in Kansas, an air force base in Texas, a transportation company in Texas, and a supermarket in Pennsylvania. These incidents resulted in seven fatalities and an additional 17 people injured. Additionally, the December 2015 shooting in San Bernadino, a mixture of workplace violence and radicalization, resulted in 14 deaths and 22 people injured.
According to an FBI report on workplace violence, 80 percent of the active-shooter situations that happened in the United States between 2000 and 2013 took place at work. Of those active-shooter incidents cited in the report, more than 46 percent were perpetrated by employees or former employees and 11 percent involved employees who had been terminated that day. The CERT Insider Threat Center conducted two back-to-back research initiatives to gain a deeper understanding of incidents of workplace violence in the context of insider threat. In this blog post, I describe our most recent research initiative to explore the technical detection of intended harm to self and/or others.
A Broader Definition of Insider Threat
Earlier this year, the CERT Insider Threat Center updated its definition of insider threat:
the potential for individuals who have or had authorized access to an organization's assets to use their access, either maliciously or unintentionally, to act in a way that could negatively affect the organization
This updated definition includes malicious and non-malicious (unintentional) insider threats and physical and cyber impacts. The definition continues to apply in both government and industry settings. It encompasses insider cyber threats, as well as incidents of workplace violence and aggression perpetrated by insiders against fellow employees or themselves, potentially leading to a loss of life. The evolving definition of insider threat across industry and government entities has spurred the research detailed in this post.
Insider Threat and Technical Detection of Intended Harm to Self or Others
Our most recent research involves the technical detection of insiders' intent to harm themselves and/or others. The purpose of this research is to fill a gap in insider threat detection, where current tools, such as user activity monitoring (UAM) and user behavioral analytics (UBA), do not have the known capabilities to detect a heightened risk of workplace violence. Newer cyber data and records, such as online human resource and personnel records, provide more information than ever before that can help identify employees who may be on the path to harming themselves and/or others. To fill this gap, we ultimately want to determine the extent to which insider threat detection tools, or detectors, are capable of monitoring indicators of self-harm and/or homicidality seen in cyber data that was not available a short time ago.
We are evaluating suicidality and self-harm in this context for several reasons including: 1) the loss of life in any form affects mission assurance and organizational effectiveness, 2) many workplace shootings end in suicide and may be due to initial suicidal ideations, and 3) it is often hard to ascertain if someone is feeling suicidal, homicidal, or a mixture of the two.
Our Research Method
We took the following steps in our research:
1) Following a thorough literature review, we developed a factor tree model of the incident lifecycle that can be used to systematically generate scenarios across five states, the combination of which we call the pathway to intended harm: predispositions, stressors, grievances, ideation, and planning and prep. The pathway to intended harm is loosely based on Calhoun and Weston's pathway to violence and the critical pathway, which was developed in collaboration with Eric Shaw. The background information in the image below is a breakdown of key indicators of suicidality and targeted violence, many of which overlap.
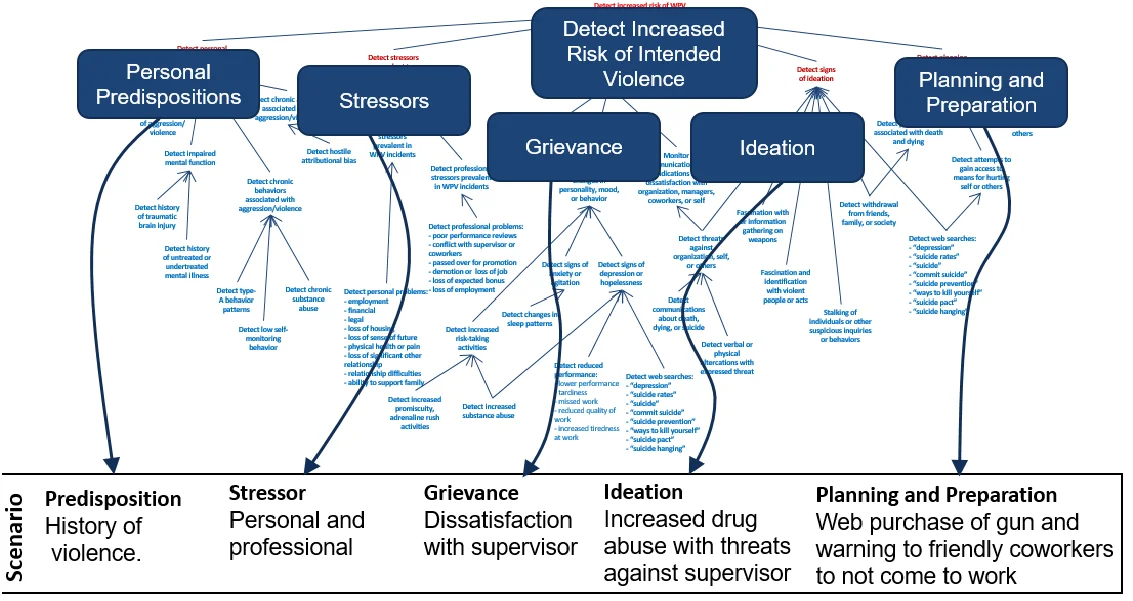
2) We developed threat scenarios of workplace violence events using the indicators for suicidality and/or homicidality that were vetted by mental health professionals. These scenarios cover various levels of severity and imminence ranging from suicidal ideations to suicide attempts and from bullying to homicide in the workplace. The pathway to intended harm is not all inclusive but rather highlights groups of indicators in each category.
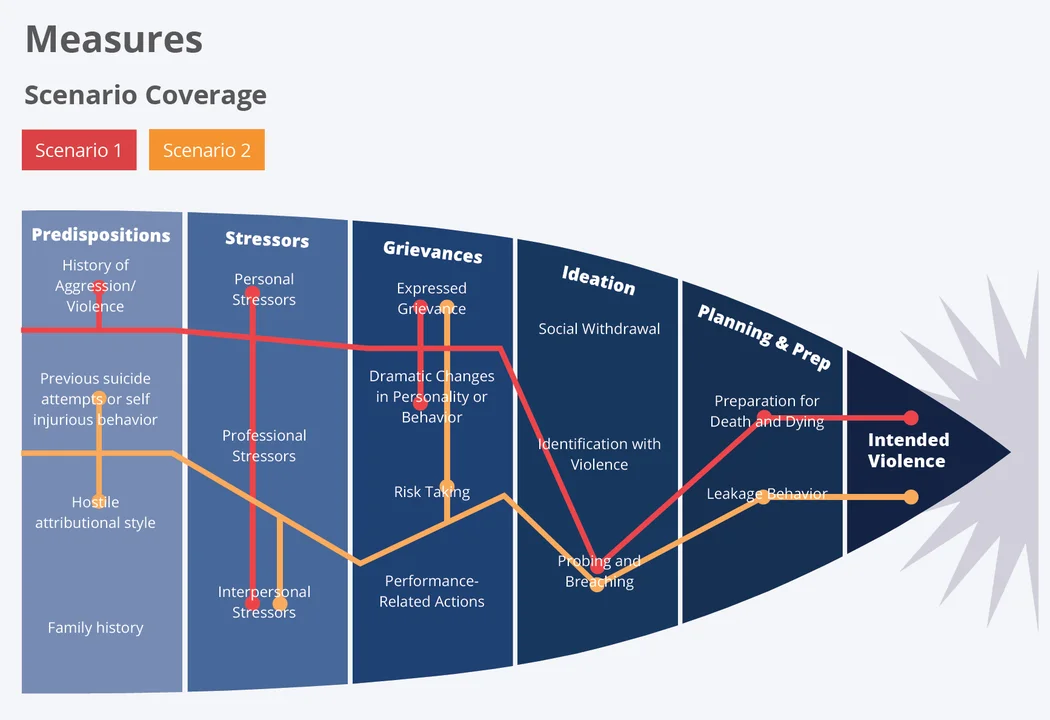
3) We mapped potential indicators of intended harm to self and/or others to data sources that may be used in insider threat detection tools and noted ways they may be implemented in insider threat detection methods. Our tool-agnostic approach allows organizations to identify data sources that can be used to monitor for specific manifestations of workplace violence indicators. For example, in a case of an employee having a conflict with a supervisor, the indicators might be seen in email/telephone records, performance evaluations, disciplinary actions, grievance filings, status change logs, and HTTP logs.
4) We laid the foundations for future work by collaborating with fellow researchers to transition the threat scenarios into scripts for ingestion into NeedleStack, which is a virtual simulation and testing environment. NeedleStack is part of our new National Insider Threat Center (NITC) and is designed to simulate insider threat scenarios to aid training, hypothesis testing, and insider threat tool evaluations. Future research will involve inserting these threat scenarios into a "noisy" operational environment to see if the psychosocial indicators show up in data sources used to monitor insider threats or in newer data sources, such as human resource data.
Our research is in the preparatory stages of validating, testing, and implementing technical detection capabilities of intended harm to self and/or others. We expect that this research will be repeatable for other insider threats, such as the technical detection of indicators of radicalization. This research builds on previous insider threat research conducted by the CERT Insider Threat Center that included cyber sabotage, espionage, theft of intellectual property, and fraud.
Goals and Benefits of Our Research
Our solution supports the Department of Defense and other organizations that try to find technical and socio-technical indicators that can strengthen the capabilities of their insider threat detection tools. The goal of this ongoing research is to mitigate the risk employees may pose to their organizations, their coworkers, or themselves. This research does not seek to predict if someone is a threat to themselves or others, but simply determines if insider threat tools or detectors can detect these indicators in noisy background data. Of utmost importance, monitoring should be done with the full approval of legal, privacy and civil liberty teams within the organization and team members addressing this sensitive matter should be trained to appropriately do so, ensuring the protection of the privacy and civil liberties of employees, contractors, and other trusted business partners.
Wrapping Up and Looking Ahead
According to the FBI Workplace Violence: Issues in Response report, work environments with threats and violence can lead to issues for employers, such as economic loss from violence, reduced employee productivity and morale, lost work time, medical expenses, an increase in worker's compensation payments, and liability and lawsuit costs. Not addressing these incidents can also lead to malicious and unintentional insider threats. Recent research from the CERT Division National Insider Threat Center on the organization's role of providing positive incentives in addition to negative incentives (i.e. restricted access, punishment for poor performance) in order to provide a more balanced work environment; thus, aiding in insider threat prevention.
As more and more insider threat programs spin up and move towards fuller operational capabilities, it is important to continue to recognize the critical importance of their workforce and the importance in protecting it from incidents of internal workplace violence. Our work assists in moving that process one step further by linking socio-technical and behavioral indicators with potential data sources for detection of an insider's potential intent to commit harm to fellow employees.
Our work has taken initial steps in the development of indicator mapping to potential data sources and tool agnostic means in which organizations may consider implementing them into their insider threat detection efforts. Future work would involve taking the synthetic threat scenarios and ingesting them into Needlestack, the virtual simulation environment, to determine if indicators of workplace violence are detected in a noisy operational virtual environment.
For more information about our insider threat research, visit the CERT Division National Insider Threat Center's research page. We plan to publish an SEI Podcast on the Insider Threat: Technical Detection of Workplace Violence, a project report Technical Detection of Insider Workplace Violence and a report on balancing insider threat defense by combining positive and negative incentives to counter insider threats, such as workplace violence, cyber sabotage, and unauthorized leaking of information.
If you have questions or comments about this research, send email to us at info@sei.cmu.edu.
Additional Resources
Learn more about the CERT Division National Insider Threat Center.
More By The Author
Negative Issues in the Work Environment (Part 5 of 20: CERT Best Practices to Mitigate Insider Threats Series)
• By Tracy Cassidy
More In Insider Threat
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
