Best Practices in Network Security
Blog Posts
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
Weak processes can be as risky as technical vulnerabilities. This post describes how both of them worsened a cyber attack on a chemical plant.
• By Daniel J. Kambic
In Enterprise Risk and Resilience Management

DNS Over HTTPS: 3 Strategies for Enterprise Security Monitoring
DNS over HTTPS (DoH) can impair enterprise network visibility and security by bypassing traditional DNS monitoring and protections. In this post, I'll provide enterprise defenders three strategies for security monitoring …
• By Sean Hutchison
In Cybersecurity Engineering

Pandemic Home Security for Your Enterprise
The COVID-19 pandemic has greatly increased remote work among enterprise employees. Home-network environments are not professionally managed, so they are an appealing target for attackers. In this post, we advise …
• By Phil Groce, Harry Caskey
In Situational Awareness


Remote Work: Vulnerabilities and Threats to the Enterprise
How has this change in the way we work altered our security posture? How has it changed our attack surface, and what should we be doing to defend it? In …
• By Phil Groce
In Situational Awareness

Cat and Mouse in the Age of .NET
This SEI Blog post explores evolving .NET threat landscape with challenges faced by red and blue teams and suggests ways to stay ahead of attackers.
• By Brandon Marzik
In CERT/CC Vulnerabilities

How to Protect Your High Value Assets

This blog post will outline the background of the federal High Value Asset (HVA) Program, explain the resources available to guide the securing of high value assets, and discuss ways …
• By Brian Benestelli, Emily Shawgo


Network Segmentation: Concepts and Practices
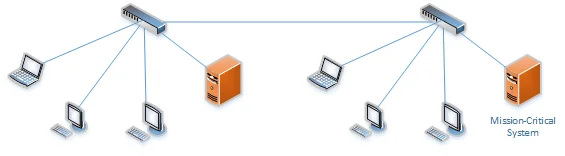
In this blog post, we review the basics of network segmentation and describe how organizations should implement it as an ongoing process.
• By Daniel J. Kambic, Jason Fricke


Anti-Phishing Training: Is It Working? Is It Worth It?
Phishing attacks target human, rather than technical, vulnerabilities. Some organizations, companies, government agencies, educational institutions, and individuals put on blinders....
• By Mike Petock
In Insider Threat

Could Blockchain Improve the Cybersecurity of Supply Chains?
A September 2018 report to the President, Assessing and Strengthening the Manufacturing and Defense Industrial Base and Supply Chain Resiliency of the United States, raised concerns about cybersecurity....
• By Eliezer Kanal
In Cybersecurity Engineering

Mapping Cyber Hygiene to the NIST Cybersecurity Framework
In honor of Cybersecurity Awareness Month, I decided to put fingers to keys and share some basic practices that every organization should consider for their cyber hygiene initiatives....
• By Matthew Trevors
In Insider Threat
