Situational Awareness for Cybersecurity: Assets and Risk
PUBLISHED IN
Situational AwarenessThis post was co-written by Lauren Cooper.
When key business assets are not adequately protected from cybersecurity breaches, organizations can experience dire consequences. Lumin PDF, a PDF editing tool, recently had confidential data for its base of 24.3 million users published in an online forum. The personal data of almost every citizen of Ecuador was also recently leaked online. Data breaches exposed 4.1 billion records in the first six months of 2019, and data breaches in the healthcare industry in 2019 have already doubled all of those last year.
The purpose of situational awareness (SA) is to protect organizations from experiencing the loss or compromise of key assets, such as those that were compromised in these recent examples. With our series of blog posts on cyber SA for the enterprise, we aim to provide a practical, high-level view of SA for cybersecurity. We began the series with an introduction to SA. Beginning with this post, we cover information necessary to achieve SA, the architectural components necessary to support maintaining SA, analytic issues, and how SA helps a security operations center. In this post, we look at the types of organizational assets, how we can measure risks to those assets, and how we can identify potential business-related consequences if those assets were to be affected by a security event.
Categorizing Assets
Business assets can be categorized in a number of ways. For example, the CERT Resilience-Management Model (CERT-RMM) uses four categories: people, facilities, information, and technology. For this series of blog posts, we will use the CERT-RMM categories, but for technology assets, we will consider whether they do processing, storage, communications, or a combination, which will help us to think about asset visibility and SA analysis. These categories align with both the objectives of cyber-attacks and aspects of physical systems that can be utilized to accomplish an objective.
In this categorization, a physical entity contains one or more of the categories of assets listed above. Each asset may require its own method of protection and monitoring. For example, a personal desktop computer consists of data that is stored on a hard drive or in random-access memory (RAM), software programs, central processing units (CPUs) that enable processing, and network interfaces that enable communications. Data and the hard drive can be protected from loss of confidentiality by means of access controls. Software can be monitored for integrity using hashes. Communications can be protected from denial of availability with firewalls. Note that the mechanisms of protection and monitoring can themselves be aligned with the asset categories (e.g., hashes and access-control information are data, whereas firewalls consist of data--the configurations--and processing).
From the perspective of business impact, categorizing organizational assets by the method of protection and monitoring needed helps identify areas of risk and potential vulnerabilities or weaknesses. For example, because a network-attached storage device contains only data and storage, we know that potential problems for this device consist of a breach of data confidentiality or data integrity, unavailability of existing data in storage, or denial of service in preventing the addition of new data to storage. Moreover, depending on the data, the breach could negatively affect the organization's reputation.
Applying this categorization of all entities in terms of method of protection and monitoring can help the organization measure risk; measuring risk enables the organization to prioritize security allocations and quickly assess consequences during a security event. In an understaffed, underfunded, and over-compromised environment, prioritizing protections for certain assets is a necessity. Prioritizing must occur in
- security hardening of individual devices and specific network segments or business units
- responses to compromises
- hiring for specific roles
For more about prioritization, see our first post in this series, Situational Awareness for Cybersecurity: An Introduction. Guidance for prioritizing assets is also available in the CERT-RMM Asset Definition and Management (ADM) process area. Figure 1 below shows a template from Appendix A, Volume 1 (Asset Management) of the Cyber Resilience Review (CRR) Supplemental Resource Guide, which was derived from the CERT-RMM. This template or something similar could be used by organizations to maintain an inventory of business assets.
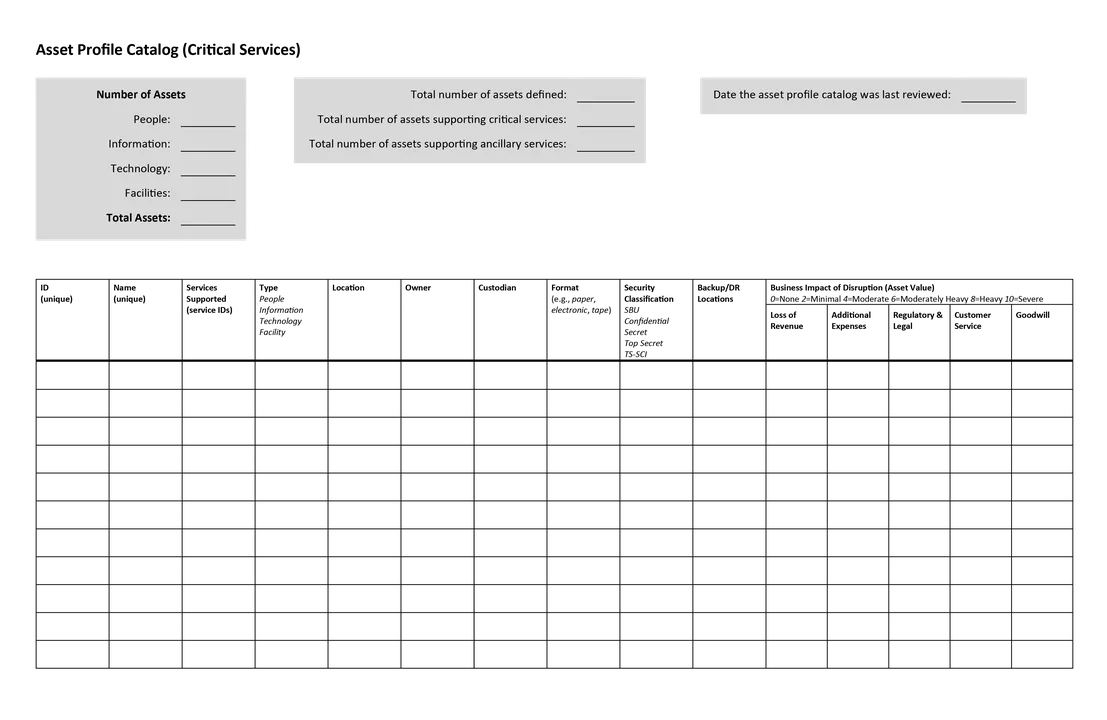
Figure 1: Asset Profile Catalog (Critical Services) Template, From Volume 1 (Asset Management) of CRR Supplemental Resource Guide
Measuring Risk
To measure risk, you have to go beyond looking at what can go wrong and determine both the likelihood of something going wrong and how severe the consequences would be. This analysis requires knowing how the asset is used to support enterprise operations. There are several methods for risk measurement, such as OCTAVE and FAIR. For more about threats to the enterprise and how to model them, see the SEI blog post, Threat Modeling: 12 Available Methods.
Evaluating risk is not a one-time activity. Organizations must continuously track assets and their corresponding risks to ensure that resources remain aligned with business objectives and priorities. Ideally, business units will maintain and make available to security operators a comprehensive, up-to-date inventory of all cyber-related assets, such as the asset profile catalog shown in Figure 1. If such an inventory is not readily available, the security team will need to use available tools, such as Nmap or network flow collection to generate a list. Note: this process is almost guaranteed to miss assets and does not provide information on the importance of the identified assets. The Risk Maturity Model (RMM) (not to be confused with CERT-RMM) provides guidelines for handling risk.
Risk management is often viewed through the lens of manager needs, but the outcomes and documentation developed and maintained by the risk-management process are useful to security analysts and incident responders, as well. Relevant and timely information about assets and their risks is an important part of the track what is component of situational awareness. (For a full description of the four components of situational awareness, see Situational Awareness for Cybersecurity: An Introduction). This information allows analysts and responders to make better inferences in infer when is and should be do not match and to prioritize responses in do something about the differences.
Moreover, the outcomes of situational awareness should be used to help inform and update the organization's current view of risk. For example, a gap may be discovered between is and should be in your enterprise. In this case, you can incorporate it into your ongoing risk assessment and then prioritize the search for additional gaps in your situational awareness program.
In our next blog post, we will discuss two important elements of know what should be: policies and controls.
Additional Resources
Learn more about situational awareness and other next-generation security operations techniques at FloCon 2020, which will be held January 6-9, 2020 in Savannah, Ga. Do you have a topic that you would like to present at an upcoming FloCon? If so, send information on the topic to flocontact@cert.org.
Read the first blog post in this series on situational awareness, Situational Awareness for Cybersecurity: An Introduction.
Read about the SEI's work in network situational awareness.
Read other SEI blog posts about network situational awareness.
Read the SEI blog post, Threat Modeling: 12 Available Methods.
Learn more about the CERT Resilience-Management Model (CERT-RMM).
Review the Asset Definition and Management (ADM) CERT-RMM process area.
More By The Authors
More In Situational Awareness
PUBLISHED IN
Situational AwarenessGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Situational Awareness
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
