Insider Threats Related to Cloud Computing--Installment 2: The Rogue Administrator
PUBLISHED IN
Insider ThreatHi, this is Bill Claycomb and Alex Nicoll with installment 2 of a 10-part series on cloud-related insider threats. In this post, we present three types of cloud-related insiders and discuss one in detail--the "rogue administrator." This insider typically steals the cloud provider's sensitive information, but can also sabotage its IT infrastructure. The insider described by this threat may be motivated financially or by revenge.
We consider the cloud-related insider threat from three different perspectives: the rogue administrator employed by a cloud provider, the employee in the victim organization that exploits cloud weaknesses for unauthorized access, and the insider who uses cloud resources to carry out attacks against the company's local IT infrastructure. Though we describe cloud-specific insiders, we believe the people behind these malicious insider attacks will continue to fit the profiles of other insider crimes identified by CERT in the book The CERT Guide to Insider Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud). As a result, mitigation strategies may be extrapolated from prior insider threat models; we will briefly discuss those options as well.
The Rogue Administrator
Let us first consider the type of insider described by Top Threats to Cloud Computing, Version 1.0, by the Cloud Security Alliance: the rogue administrator employed by a cloud provider. This cloud-related insider is the most commonly addressed by researchers. An attack often posited by this insider is the theft of sensitive information, resulting in loss of data confidentiality and/or integrity. The insider described by this threat may be motivated financially, a common motivator for theft of intellectual property or fraud.
But another attack possibility to consider is IT sabotage, where an employee seeks to harm an employer's IT infrastructure. Some may dismiss this type of crime in cloud environments, where administrators work for the provider, not the customer. However, this attack possibility should not be entirely discounted. Even if it is unlikely an insider has a grudge against the victim organization, an insider's grudge against the cloud provider could result in harm to a victim organization with the intention of damaging the cloud provider's reputation.
The following excerpt is adapted from an actual case in CERT's database of insider threat; it describes an attacker motivated by financial gain:
The insider was employed as a system administrator at a data-mining firm contracted by a victim organization to process customer information. Though unnecessary for the job function, the insider had access to servers and data owned by the victim organization. An unprotected file containing encrypted password information was found on one of these servers. The insider brute-force attacked over 300 passwords, accessed data belonging to dozens of the victim organization's customers, and downloaded millions of personal records. Fortunately, the information was never sold or released by the insider prior to arrest.
This example highlights a case involving a trusted business partner in a relationship very similar to cloud computing. Despite CERT's ongoing process for gathering current insider threat incidents, this is one of only a few cases we collected that describes a cloud-related scenario. However, we have many cases that involve contractors, temporary employees, and employees of trusted business partners who exploited authorized access to an organization's systems and information to steal data. Those cases aren't quite cloud-related, but they do pose some of the same challenges; specifically, who does an organization choose to trust with access to sensitive information, and how does the organization control the access it grants?
Another often-overlooked threat posed by the rogue administrator is impact to customer data availability. Another incident captured by CERT describes a system administrator at an organization very similar to the one described above, one that managed data and operations for other companies. However, rather than compromising customer information, this insider simply removed critical software from the hosting systems, which prevented the provider from responding to customer requests. While customer data remained intact and confidential, customers were adversely affected by their lack of access to important information.
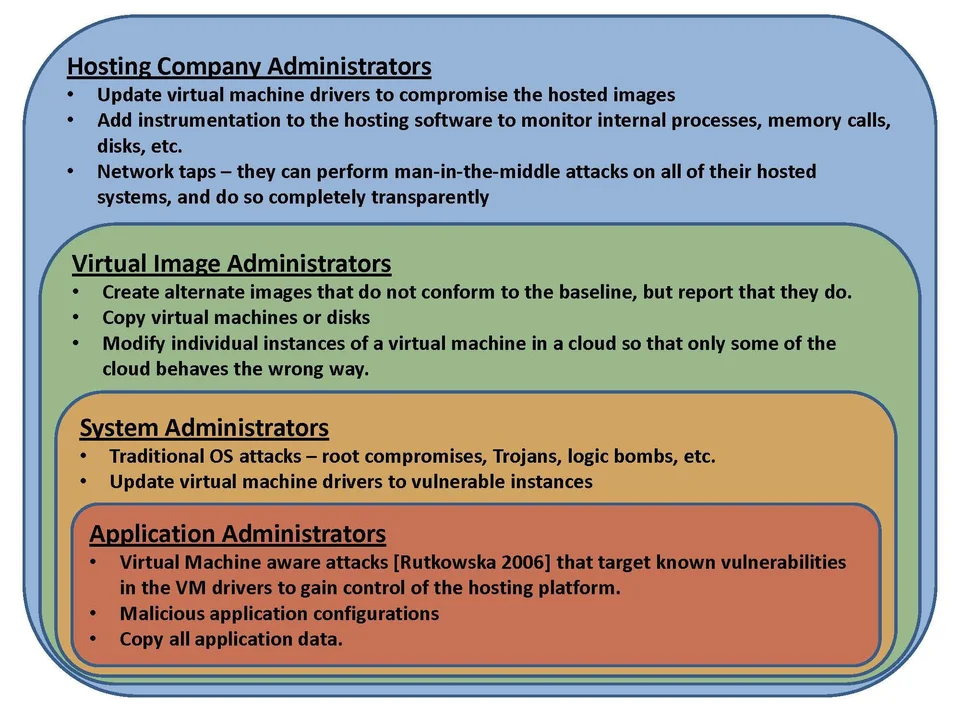
The threat from rogue administrators is layered differently for a cloud architecture than a standard enterprise environment. There are at least four levels of administrators to consider in the cloud:
- hosting company administrators
- virtual image administrators
- system administrators
- application administrators
We propose this collection of administrator levels is a hierarchical relationship; in other words, the higher level administrators have the capabilities of lower level administrators. The figure below shows this relationship and gives a summary of example attacks and/or vulnerabilities each level of administrator could exploit.
Coming up next: We'll discuss exploiting weaknesses introduced by use of the cloud.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed