Handling Threats from Disgruntled Employees
PUBLISHED IN
Insider ThreatDisgruntled employees can be a significant risk to any organization because they can have administrative privileges and access to systems that are necessary for the daily operation of the organization. These disgruntled employees can be identified and monitored, but without knowing what types of outcomes disgruntled insiders might accomplish, monitoring can become strenuous and overbearing.
Hi, I'm Richard Bavis, Insider Threat Graduate Intern at the CERT Insider Threat Center. In this blog post, I will discuss the top three outcomes of an attack conducted by a disgruntled insider to provide you with better insight into situations that could lead to an attack. By looking at these situations and outcomes, you and your organization will be able to better handle the possible threats of a disgruntled employee.
According to The CERT Guide to Insider Threats, an employee normally becomes disgruntled due to an unmet expectation or an unfortunate event (e.g., the insider was under the impression that he/she was about to be promoted, but was evidently passed over). Additionally, the employee is typically technically sophisticated and uses the same resources or performs similar actions during his/her job as done during the attack, making it difficult to differentiate between the two.
The CERT insider threat database contains over 1000 incidents where insiders have either harmed their organization (sabotage); stolen proprietary information (theft of intellectual property); or modified, added, or deleted data for the purpose of personal gain or identity theft (fraud). Of these cases, 33 were reported to involve a disgruntled employee--as documented by either court documents or witness testimonies. This statistic shows that even though the database holds a large number cases, the documentation of such behavior is limited and it is likely that other cases involved a disgruntled employee. But, because such involvement has not been explicitly stated or documented, I will not include these cases in the following examples.
Of those 33 cases, 70% have been categorized as sabotage, with 85% of those sabotage cases documenting revenge as the primary reason behind the attacks. Other incidents identified motives of benefiting a new employer or the need for recognition. With these findings, it is no surprise that that the top three specific outcomes of disgruntled employee attacks are data deletion (13 cases), system blocked from access (11 cases), and data copied (10 cases). It is possible for an incident to have multiple outcomes. In these 33 cases, there are 6 that have both data deletion and system blocked from access as the impact to the organization. However, there were no cases in which the insider deleted data or blocked access the system and copied data.
The incidents involving the deletion of data ranges from deleting specific records to deleting source code that corrupted a critical system that the company and its customers relied on. In one case, the insider, who had full access to the company's network and systems, had a falling out with his employer and was terminated. On the day of the insider's termination, he proceeded to remotely attack the organization for four months. The insider deleted crucial files on servers, removed key backup disks, and deleted numerous records from an important database used by other systems. The insider was able to attack the organization in such a manner because his credentials were still enabled.
In a separate incident an insider remotely blocked access to a system within 30 minutes after being terminated. The insider was able to access to the victim organization's network because his credentials had not yet been disabled. The insider's job duties gave him remote authorized access to the firewall, which allowed him to repair it offsite. The insider used this access to disable the CEO's account from accessing the internet and modified files to disable the system.
Another incident involved an insider who had various external personal issues, including a custody battle and financial issues. These issues were multiplied by a poor performance review and the notification that he was being terminated in two months. The insider's supervisor characterized him as volatile, angry, and inflexible. The insider became hostile at work, even threatening the HR department, causing him to be immediately terminated. The insider had previously installed backdoors into the network and used a generic administrative password, that wasn't changed after he was terminated, to change additional administrative passwords and prohibit specific individuals' access to the system who had a direct role in the insider's termination.
A fourth incident involved an insider who created the organization's network that provided critical systems to thousands of individuals. However, the insider was the only one who knew the passwords; he refused to provide these passwords to any new administrators. This caused a dispute between the insider and the employer. Additionally, this insider set the network up to fail if anyone attempted to reset the network without the proper passwords, effectively prohibiting anyone from working towards resolving the issue.
Two additional incidents involving insiders copying data, stemmed from disagreements with their supervisors over possible security issues and the insider's attempts to address the vulnerability. In both cases, the insider complained and made suggestions to correct security vulnerabilities and improve the companies' policies. The insiders' suggestions were not accepted, causing the insiders to become disgruntled. Both insiders decided to prove that their suggestions were best by exploiting the vulnerabilities, resulting in the insiders cracking more than 30 user passwords. One insider reported his work to his manager, while the other one decided to use the passwords to gain access to other systems.
The following bar chart shows the number of times an outcome was documented in cases where an insider was observed to be disgruntled:
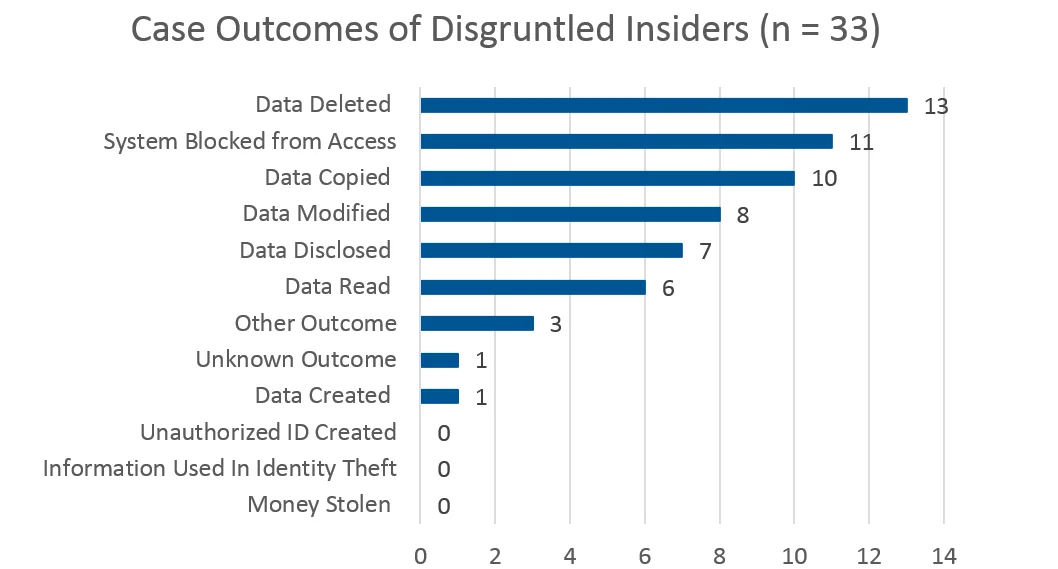
The 6 incidents discussed at length are a small number compared to the other cases involved in this analysis. Yet they provide powerful examples and insight that allow companies to focus their monitoring efforts to incorporate the outcomes discussed in this blog post. Furthermore, it allows companies to be aware of potential impacts of an attack by a disgruntled employee and recommends the implementation of security tools or policies around critical data to prevent these outcomes from occurring.
To learn more about how to monitor and mitigate disgruntled employee attacks, see The CERT Guide to Inside Threats: How to Prevent, Detect, and Respond to Information Technology Crimes (Theft, Sabotage, Fraud), by Dawn Cappelli, Andrew Moore, and Randall Trzeciak or see The "Big Picture" of Insider IT Sabotage Across U.S. Critical Infrastructures by the same authors.
Please let us know what other insider threat topics interest you or would be helpful. Contact us to send your ideas.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed