Cybersecurity of Logistics Decision Models
PUBLISHED IN
Cyber-Physical SystemsGoods, services, and people simply cannot get to where they are needed without effective logistics. Logistics are essential to nearly all aspects of the economy and national security. Despite this, a number of challenges can disrupt logistics from severe weather and global pandemics to distribution bottlenecks. In this blog post we will focus on cyber attacks to logistics decision models.
National security and military organizations consider contested logistics as “the environment in which an adversary or competitor intentionally engages in activities or generates conditions, across any domain, to deny, disrupt, destroy, or defeat friendly force logistics operations, facilities, and activities.” For example, in World War II, the Allied Transportation Plan included strategic bombing of major road junctions, bridges, tunnels, rail lines, and airfields to hamper German movements to the Normandy area. This played a decisive role in the success of the D-Day landings.
While protecting the physical components of logistics operations is critical, modern logistic systems also include extensive software-based decision support that is essential to logistics planning phases, and this software also must be protected from attack.
Beyond general cybersecurity, there are no standard methods for monitoring, detecting, and preventing cyber attacks to logistics decision models. However, there are well-studied adjacent fields such as artificial intelligence (AI) security, machine learning operations (MLOps), and more broadly AI engineering that can contribute to the securing of our logistics decision models.
Hypothetical Attack to a Logistics Model
Consider a logistics model that determines how to distribute supplies to hurricane victims in Florida. We need to decide where to locate supply storage facilities, as well as how supplies from each facility are to be distributed to surrounding populations.
In the context of national security and military operations, scenarios might include designing logistics systems to transport fuel, munitions, equipment, and warfighting personnel from their originating locations to the front lines of a conflict. Another military use case might be determining the optimal routing of vehicles, ships, and airplanes in a way that minimizes casualty risk and maximizes mission effectiveness.
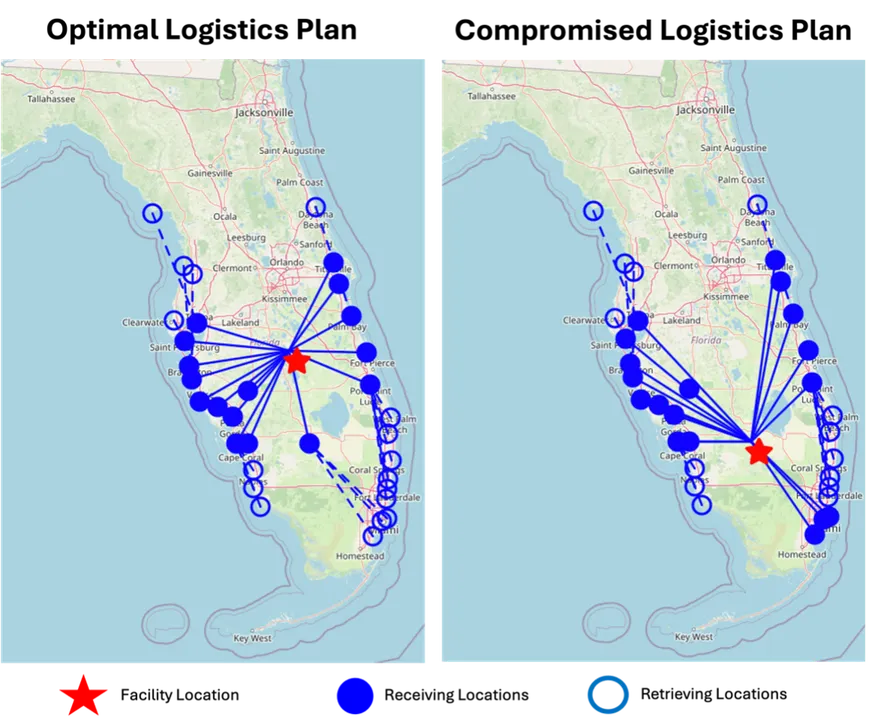
Figure 1 illustrates using a variation of the k-center formulation to compute an optimal policy for the Florida hurricane scenario (left panel). If a cyber-attacker had access to this model and was able to modify its coefficients, then we might end up with a plan such as depicted in the right panel. The recommended central facility location has changed, which could degrade the efficiency of our hypothetical system, or worse, prevent disaster victims from receiving needed supplies.
In a military conflict, even seemingly subtle changes like a recommended facility location could be enormously damaging. For example, if an adversary were to have some capability to attack or degrade a particular location unbeknownst to the defender, then manipulating the defender’s decision model could be part of an effort to physically damage the defender’s logistics system.
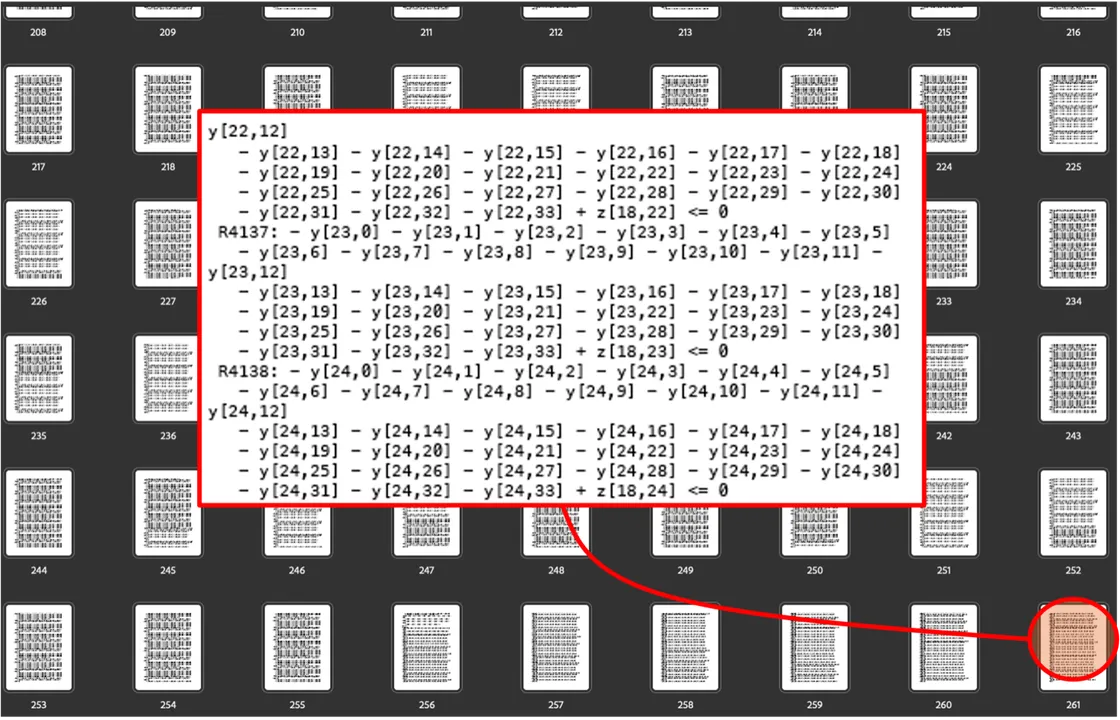
In practice, logistics decision models can be extremely large. For example, the small linear model used for Figure 1 solves a system of 266 pages of linear equations, which Figure 2 depicts. If 100 locations need to be covered, the model would have about 20,000 decision variables, about 40,000 constraints, and up to about 800 million coefficients. Due to the problem of scale, practitioners often use approximation algorithms that can generate reasonably good policies for their specific problems.
There are many types of logistics problems, including facility location, vehicle routing, scheduling, machine assignment, and bin packing. Logistics problems are often formulated as linear programs. Figure 3 shows the general form of a linear program, which (1) minimizes an objective function (the vector of objective coefficients, c, multiplied by a vector of decision variables, x); (2) subject to a set of constraints (the constraint coefficient matrix, A, multiplied by the vector of decision variables, x, is equal to the constraint requirements vector, b); and (3) with the decision variables, x, taking on positive values. Most logistics problems involve a variation of this model called a mixed integer linear program, which allows some of the decision variables to be integer or binary. For example, a binary decision variable might represent whether to open a supply depot (one) or not (zero) at a given location. Note that Figure 3 is a compact (small) model representation, and its use of vectors and matrices ( c, x , b , and A ) can model any sized problem (for example with thousands of decision variables, tens of thousands of constraints, and millions of coefficients).

George Dantzig invented the simplex method in 1947 to solve linear programs, which are so pervasive that the simplex method is considered one of the great algorithms of the 20th century. In the early 2010’s, it was estimated that 10-to-25 percent of all scientific computation was devoted to the simplex method. Today, even with computing advancements, solving linear programs at-scale remains an enormous challenge.
In logistics practice, these models can be huge. Not only are they very difficult to solve, but they can be physically impossible to solve with current computing technology. Today, much of the operations research field is devoted to developing approximation algorithms that yield high quality (although not necessarily optimal) solutions to real-world logistics problems. Recent research (see here and here) provides examples of such approximation algorithms. Because these mathematical programs are often NP-hard (i.e., the problem size grows exponentially, and optimal solutions cannot be generated in polynomial time), optimization is one of the promising use cases for quantum computing.
Discrete event simulation and system dynamics are also modeling styles used to solve logistics problems. While we discuss linear programming as an exemplar model form in this blog, other model forms can be similarly vulnerable to cyber attacks.
Concept of Operations
There is little published research, or even operating experience, regarding cyber attacks on logistics decision models. An attack would require undetected network intrusion; persistence to allow reconnaissance on the target model and attack planning; followed by model or data manipulations that are subtle enough to be undetected while strategic enough to be damaging.
In practice, a successful attack would require a sophisticated combination of skills likely only available to motivated and experienced threat groups. Such threat groups do exist, as evidenced by intrusions into U.S. critical infrastructure and technology enterprises like Google.
The Cyber Kill Chain developed by Lockheed Martin is a 7-step model of how sophisticated cyber attacks are often performed. The seven steps are: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and finally acting on the attacker’s objectives. Attacking a decision model would similarly require these steps to establish a persistent network intrusion, access to the model, and finally manipulate the model or its output.
Once attackers gain access to a logistics model, the damage that they can inflict depends on many factors. Like AI security, much depends on the type of access gained (e.g., model read-only access, model write access, training data read-only access, training data write access, ability to exfiltrate a copy of the model or data, etc.). Unlike many AI applications, logistics often introduces sprawling supply chains of contractors and subcontractors. If an upper echelon decision model depends on data from organizations at lower echelons in the supply chain, then the model could conceivably be attacked by poisoning data in systems beyond the model operator’s control.
Recommendations for Securing Logistics Decision Models
We call on the logistics, cybersecurity, and operations research communities to systematically investigate the susceptibility of decision models to cyber attack and to provide formal recommendations for how best to protect those models.
In the meantime, there are well-studied adjacent fields that offer current logistics model operators opportunities to improve security. For example, machine learning operations (MLOps) is a systematic framework for ensuring reliable deployments into production environments. More broadly, the SEI is leading the National AI Engineering Initiative, which systematizes what is needed to develop, deploy, and maintain AI systems in unpredictable and chaotic real-world environments. Monitoring is a central tenet of MLOps and AI engineering, including methods to identify significant model and data changes between revisions.
Finally, we recommend that AI security organizations consider logistics decision models within their purview. The linear programing that underpins logistics models shares many attributes with AI: both can be massive scale, compute intensive, rely on data, and be difficult to interpret. Like AI, attacks to logistics decision models can create significant, real-world damage.
More By The Authors
More In Cyber-Physical Systems
Don’t Wait for ROI on Model-Based Analysis for Embedded Computing Resources
• By Alfred Schenker, Jerome Hugues
PUBLISHED IN
Cyber-Physical SystemsGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Cyber-Physical Systems
Don’t Wait for ROI on Model-Based Analysis for Embedded Computing Resources
• By Alfred Schenker, Jerome Hugues
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


