A New Scientifically Supported Best Practice That Can Enhance Every Insider Threat Program!
PUBLISHED IN
Insider Threat(Or..."How This One Weird Thing Can Take Your Program to the Next Level!")
The CERT National Insider Threat Center (NITC) continues to transition its insider threat research to the public through its publications of the Common Sense Guide to Mitigating Insider Threats (CSG), blog posts, and other research papers. We recently released an updated version of the CSG: the Common Sense Guide to Mitigating Insider Threats, Sixth Edition. In this post, I'll highlight the new additions and updates: best-practice mappings to standards and more attention to workplace violence, monitoring, and privacy. I'll also walk you through the new best practice, on positive incentives in the workplace.
21 Best Practices
In the fifth edition of the CSG, we described 20 best practices that any organization can implement to help prevent, detect, or mitigate insider threats. The sixth edition describes 21 best practices. The new and revised best practices in the sixth edition are based on the latest research findings and case studies. The table below summarizes the best practices from the sixth edition of the CSG.

Best Practice 21: Adopt Positive Incentives to Align Workforce with the Organization
All groups within an organization, as shown above, are involved in the newest, capstone best practice: "Adopt positive incentives to align the workforce with the organization." Best Practice 21 refers to workforce management practices that increase perceived organizational support as positive incentives because they attempt to entice (rather than force) an employee to act in the interests of the organization.
Enticing employees to act in the interests of the organization through positive incentives reduces the baseline insider threat risk. Positive incentives that align workforce values and attitudes with the organization's objectives form a foundation on which to build traditional security practices that rely on forcing functions. The combination of incentives and forcing functions improves the effectiveness and efficiency of insider threat defense.
Best Practice 21 is derived from the research published in an SEI technical report: The Critical Role of Positive Incentives for Reducing Insider Threats. The research identified and analyzed three avenues for aligning the interests of the employee and the organization--job engagement, perceived organizational support, and connectedness with co-workers--to reduce the risk of an insider becoming a threat. The model developed from this research shows how these factors can encourage employees to act in the interests of the organization. One particularly strong outcome showed that as perceived organizational support went up, the risk of an insider incident went down (see figure below).
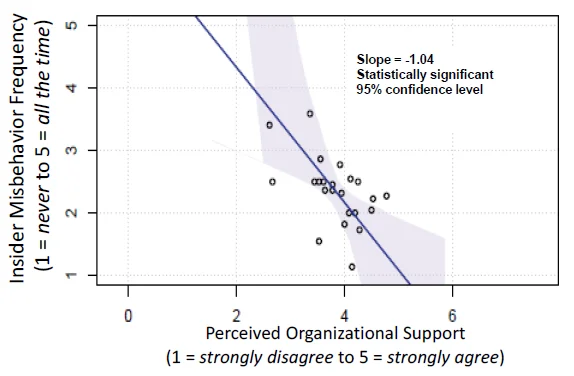
Figure 1. Negative Correlation Between Perceived Organizational Support and Insider Misbehavior
We adapted the key components of this research into Best Practice 21 in the Common Sense Guide to Mitigating Insider Threats, Sixth Edition.
This practice is related to Best Practice 5, "Anticipate and manage negative issues in the work environment," and Best Practice 8, "Structure management and tasks to minimize insider stress and mistakes." The difference is that Best Practice 21 focuses on using positive incentives to improve employee attitudes independent of whether a specific negative issue or insider stress exists or is even identifiable. In other words, positive incentives are proactive and reduce the frequency of insider incidents before they, or even their indicators, occur.
Best Practice 21, consistent with all the other best practices, contains the following sections:
- Protective Measures
- Challenges
- Case Studies
- Incident Analysis
- Survey on Organizational Supportiveness and Insider Misbehavior
- Quick Wins and High-Impact Solutions for All Organizations
Other New Features: EU-GDPR, Privacy, Workplace Violence, Standards Mapping
In the sixth edition, we also integrated new information into the other best practices to reflect aspects of the European Union's General Data Protection Regulation (EU-GDPR); we paid special attention to issues surrounding insider threat and associated employee-monitoring concerns. In the sixth edition, we also interwove aspects of workplace violence prevention into many of the best practices. Finally, we updated mappings of the best practices to other relevant standards and added new mappings to the following:
- NIST Cybersecurity Framework
- Center for Internet Security Controls V7
- National Insider Threat Task Force Program Maturity Framework
- European Union General Data Protection Regulation (GDPR)
The table below shows an example of this mapping of best practices, using Best Practice 1, to security control standards.
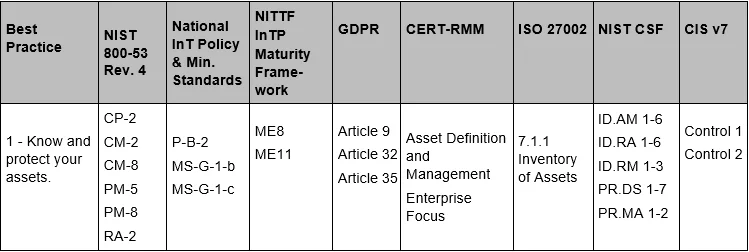
Example of Best Practice 1 Mapped to Security Control Standards
Looking Ahead: New Practices for New Threats
We continue to research new insider threat vectors and develop mitigation strategies for organizations to prevent, detect, and respond to these threats. We plan to incorporate these strategies into future versions of the CSG.
Additional Resources
We invite you to search for and read our blog series on CERT Best Practices to Mitigate Insider Threats and read our report titled The Critical Role of Positive Incentives for Reducing Insider Threat.
Subscribe to our Insider Threat blog feed to be alerted when any new post is available. For more information about the CERT National Insider Threat Center, or to provide feedback, please contact insider-threat-feedback@cert.org.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
