2017 U.S. State of Cybercrime Highlights
Each year, the CERT Division of the SEI collaborates with CSO Magazine to develop a U.S. State of Cybercrime report1. These reports are based on surveys of more than 500 organizations across the country, ranging in size from fewer than 500 employees to more than 10,000. Each organization self-reports on information security issues that have impacted them in the past calendar year. The 2017 report covers activity that occurred in 2016. In this blog post, we share some of the findings from the upcoming report as they relate to insider threats.
Nearly 30 percent of all respondents reported that incidents caused by insider attacks were more costly or damaging than outsider attacks.
Excluding participants unsure of the costs of incidents, nearly half (43%) of survey respondents reported that electronic crimes committed by insiders were more costly than those committed by outsiders. These figures are on par with those reported in the 2016 U.S. State of Cybercrime report.
According to the responding organizations, insiders were the source (or cause) of the following:
- 45% of incidents where private or sensitive information was unintentionally exposed
- 40% of incidents where customer records were compromised or stolen
- 38% of incidents where employee records were compromised or stolen
- 35% of incidents where private or sensitive information was intentionally exposed
- 33% of incidents where confidential records (e.g., trade secrets or intellectual property) were compromised or stolen
The number of incidents attributable to insiders where employee records were compromised or stolen increased by 5% in the 2017 survey compared to the 2016 survey.
Nearly a third of participants experienced an insider incident.
In the 2017 survey, only 34% of survey participants experienced an incident and only one in five (20%) attacks were committed by insiders. However, in the 2016 survey, as many as 43% percent of survey participants reported that an insider incident was committed against their organization and that more than one in four of the attacks against their organization were committed by insiders (27%). In other words,
- The proportion of organizations experiencing a known insider incident decreased.
- The proportion of incidents attributable to insiders decreased.
- External attacks still outnumber insider incidents, but insider incidents persist.
The following graph illustrates how the rates described above have changed somewhat over time:
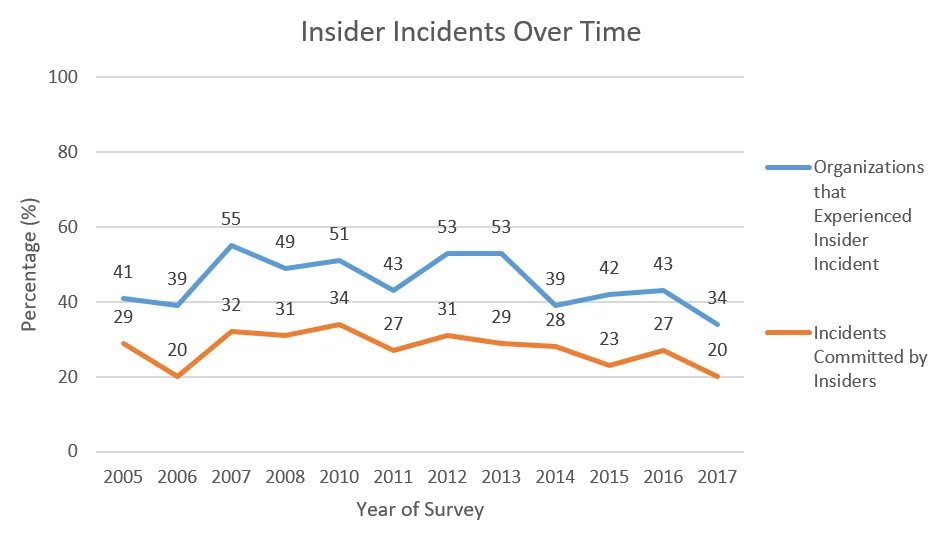
Although the proportions may have decreased both for organizations experiencing an incident and for incidents committed by insiders, this change may not hold for the future. As the graph shows, there are slight increases and decreases over time. For that reason, while there may have been a slight decrease between the 2016 and 2017 surveys, that is not to say that there will be less incidents by the time of the 2018 survey.
Incident response strategies remained consistent with those used in previous years.
One of the benefits of conducting an annual survey is the ability to note changes, or a lack thereof, over time. In the following table, note the consistency of the strategies used to respond to insider intrusions from the 2015 to 2017 surveys, despite the drop in incidents between the 2016 and 2017 surveys.
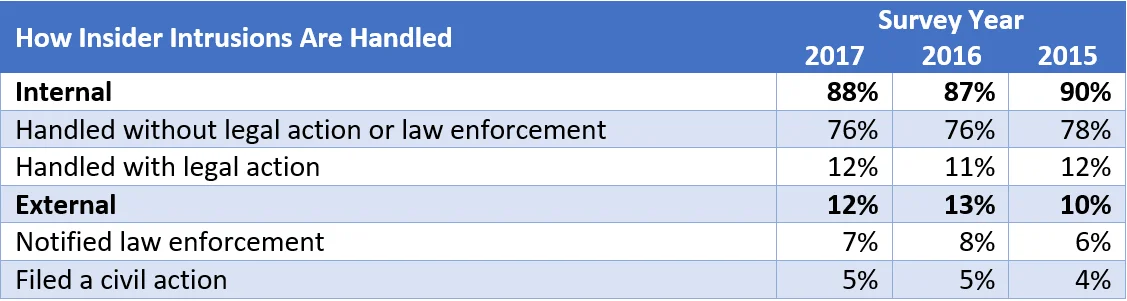
Note: Percentages are rounded up to the nearest percent.
In contrast, the following table shows that the perceptions of insider incidents have changed in some areas over the past year.
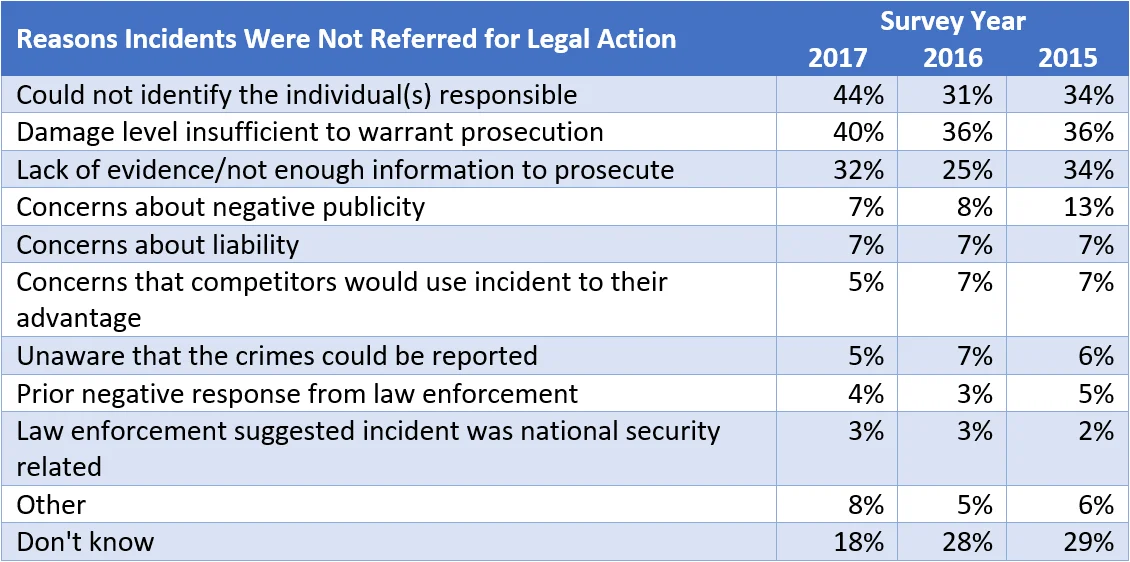
Nearly half (44%) of organizations responding to the survey indicated that they could not identify the individual(s) behind an incident; this is a 13% increase from the previous report. Additionally, 7% more organizations said that they lacked evidence or did not have enough information to prosecute. These apparent changes in organizations' overall preparedness in addressing insider incidents could contextualize what appears to be a drop in the number of insider incidents; perhaps it is not that there are fewer insider incidents, but instead organizations are not able to identify them as such. Taken together, these statistics might suggest the need for continuous monitoring: Organizations need to have sufficient information to identify (1) incidents (ideally before assets are taken and not recoverable the organization) and (2) the actors involved.
The complete 2017 State of Cybercrime Survey Report is available through CSO Online. If you are interested in State of Cybercrime reports from years past, you can find them in the SEI Digital Library.
1The 2017 U.S. State of Cybercrime Survey, in partnership with Forcepoint, CSO, U.S. Secret Service, and CERT Division of Software Engineering Institute at Carnegie Mellon University
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
