Structuring the Chief Information Security Officer (CISO) Organization
PUBLISHED IN
Cyber Workforce DevelopmentMost organizations, no matter the size or operational environment (government or industry), employ a senior leader responsible for information security and cybersecurity. In many organizations, this role is known as chief information security officer (CISO) or director of information security. CISOs and others in this position increasingly find that traditional information security strategies and functions are no longer adequate when dealing with today's expanding and dynamic cyber-risk environment. Publications abound with opinions and research expressing a wide range of functions that a CISO organization should govern, manage, and perform. Making sense of all this and deciding on an approach that is appropriate for your specific organization's business, mission, and objectives can prove challenging. In this blog post, we present recent research on this topic, including a CISO framework for a large, diverse, U.S. national organization. This framework is the product of interviews with CISOs and an examination of policies, frameworks, maturity models, standards, codes of practice, and lessons learned from cybersecurity incidents.
In exploring the role of CISO, our team of researchers at the SEI's CERT Division explored the expanding operational risk environment with respect to IT operations, cybersecurity, business continuity, and disaster recovery. We interviewed several CISOs in various organizations and conducted an in-depth analysis of recent, large-scale, high-impact cybersecurity incidents. The challenge of identifying an effective organizational structure is a critical dimension of cybersecurity research, which is a primary focus area of the SEI's CERT Division.
As detailed in our technical note on this research, Structuring the Chief Information Security Officer Organization, and depicted in the figure below, we used these inputs and our experience developing and applying the CERT Resilience Management Model to identify four key functions that capture the majority of a CISO's responsibilities:
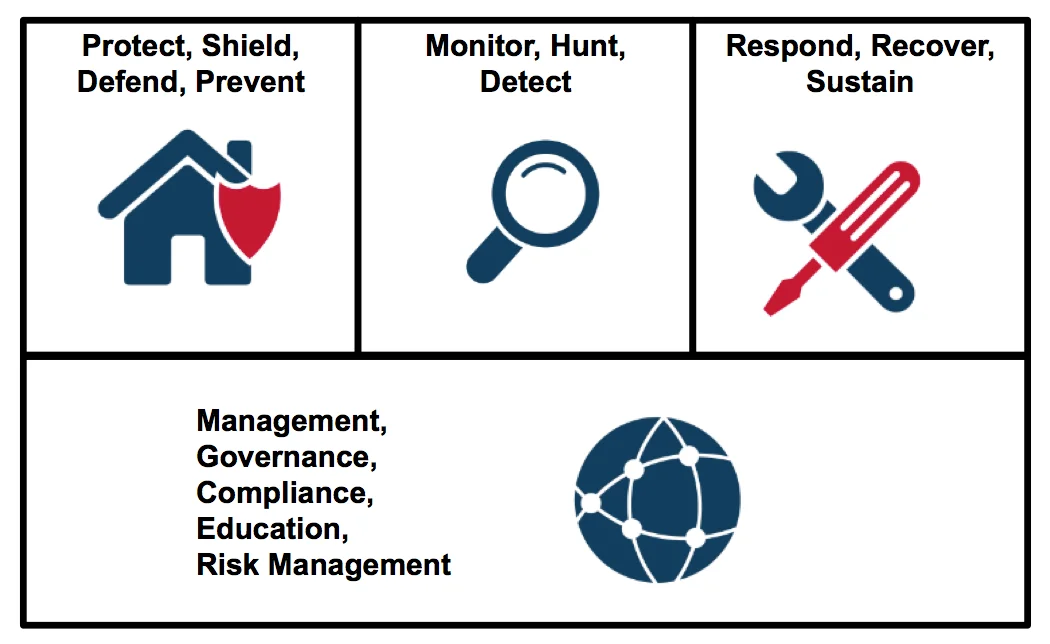
- Protect/Shield/Defend/Prevent. Ensure that the organization's staff, policies, processes, practices, and technologies proactively protect, shield, and defend the enterprise from cyber threats, and prevent the occurrence and recurrence of cybersecurity incidents commensurate with the organization's risk tolerance.
- Monitor/Hunt/Detect. Ensure that the organization's staff, policies, processes, practices, and technologies monitor ongoing operations and actively hunt for and detect adversaries, and report instances of suspicious and unauthorized events as expeditiously as possible.
- Respond/Recover/Sustain. When a cybersecurity incident occurs, minimize its impact and ensure that the organization's staff, policies, processes, practices, and technologies are rapidly deployed to return assets to normal operations as soon as possible. Assets include technologies, information, people, facilities, and supply chains.
- Management/Governance/Compliance/Education/Risk Management. Ensure that the organization's leadership, staff, policies, processes, practices, and technologies provide ongoing oversight, management, performance measurement, and course correction of all cybersecurity activities. This function includes ensuring compliance with all external and internal requirements and mitigating risk commensurate with the organization's risk tolerance.
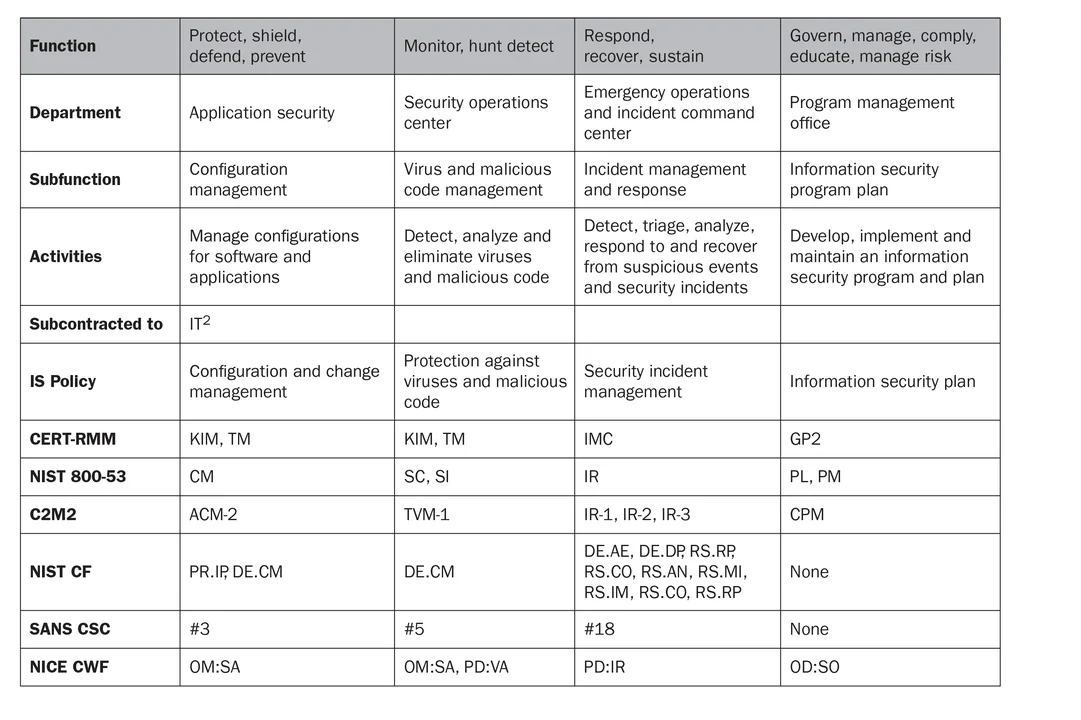
To expand the definitions and scope of the four functions listed above, we reviewed the following policies, frameworks, maturity models, standards, and codes of practice that cover the scope of cybersecurity, information security, and continuity of operations as it relates to cybersecurity. These documents helped us address the topics typically addressed in a large organization's information security policy. They include the following:
- U. S. National Institute of Standards and Technology (NIST) Special Publication 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
- NIST Framework for Improving Critical Infrastructure Cybersecurity
- National Initiative for Cybersecurity Education (NICE) The National Cybersecurity Workforce Framework
- SANS Critical Security Controls (Top 20)
- CERT Resilience Management Model (CERT-RMM)
- U.S. Department of Energy Cybersecurity Capability Maturity Model (C2M2)
We mapped the sources above to the four functions that we identified earlier-protect, monitor, respond, and govern. We next grouped the mapping by function into sub-functions and activities, which resulted in departments. We next organized the departments into the CISO structure shown below:
We also identified activities or sub-functions that could be performed by parties other than the CISO. Even when that happens, the CISO still retains governance, oversight, and leadership responsibility. This responsibility can be enacted, in part, by effective performance measurement.
Four Organizational Units
We defined the following four organizational units reporting to the CISO, as well as areas of work and responsibilities that each units encompasses.
- program management: project management office; governance, risk, and compliance; workforce and supplier management; interface with the business
- security operations center: situational awareness, ongoing monitoring, security helpdesk, computer incident response
- emergency operations and incident management: high-impact incidents; planning for incident response, business continuity, disaster recovery; tests, exercises, and drills; incident post mortems; investigations
- security engineering and asset security: security engineering, identity and access management, applications security, host and network security, information asset security, and physical access control
An information security executive council serves as an advisory group for the CISO and may have an internal and an external body. This advisory group ensures that information security functions align with organizational objectives and that policy and governance obligations are met.
Members may include, but aren't limited to, the following:
- chief operating officer
- chief information officer
- chief financial officer
- legal/privacy
- human resources
- communications / marketing
- business unit VPs
- engineering VP
- information technology VP
We recommended merging security engineering (development and/or acquisition) and security aspects of IT operations (security of assets including applications, hosts and networks, information, physical access controls) into one unit based on DevOps and other current experiences.
Given the demand for rapid development and/or acquisition and release of new capabilities, it is increasingly critical that development staff be tightly coupled with IT ops staff.
Implementing Across the Lifecycle
Our research also included an examination of existing publications detailing resources for CISOs to help determine the appropriate staff size and budgets for their organizations. (Note: These results are highly dependent upon the functions and activities that the CISO is responsible for performing and overseeing.)
A more detailed list is available in our technical note, but the InfoSec Island article "How Many Information Security Staff Do We Need?" examines nine other reports and surveys on the subject of information security staffing and reports the following summary findings:
- 3 to 6 information security staff per 100 IT staff
- 1.75 information security staff per 1 internal IT auditor
- 1 information security staff per 5000 networked devices (workstations, switches, firewalls, servers, etc.; this list does not appear to include mobile devices.)
- 3 percent to 11 percent of the total IT budget is allocated to information security. (The authors have often seen 3 percent--5 percent from CISOs and other literature sources.)
Wrapping Up and Looking Ahead
We recommend that readers consider using the approach and guidelines detailed in our blog post and technical note as a guideline for structuring a CISO organization and for allocating roles and responsibilities to its various organizational units. Clearly, CISOs will want to adapt and tailor what is suggested here to meet their organization's specific priorities and requirements.
For organizations and CISOs considering using this guidance, we recommend the following next steps:
- Map your current CISO structure to our recommended structure, departments, sub-functions, and activities. Identify where you have full coverage of the current structure, partial coverage, and gaps (no or minimal coverage). For partial, minimal, or no coverage, determine whether these activities are being performed elsewhere in the organization.
- Determine which organizational units can continue as is, which need to change (i.e., expand or contract), and whether new units need to be created. Consider insourcing and outsourcing solutions as well as encouraging more active collaboration with existing units that perform cybersecurity activities.
- Develop an implementation roadmap. Consider using defined maturity indicator levels to measure progress. You can derive these indicator levels from, for example, the CERT-RMM. This model has been successfully used by the U.S. Department of Energy (Cybersecurity Capability Maturity Model) and by the U.S. Department of Homeland Security (Cyber Resilience Review) to assess and improve the cybersecurity programs of their constituents.
Example maturity indicator levels include incomplete, performed, planned, managed, measured, and defined (also referred to as optimized).
While we have implemented this approach with a large, diverse, U.S. organization--the United States Postal Service--we would be interested in speaking with CISOs from organizations that have taken a drastically different approach or that have implemented our research on a smaller scale. To contact us, please send email to info@sei.cmu.edu.
We welcome your feedback on this research in the comments section below.
Additional Resources
Read the technical note Structuring the Chief Information Security Officer Organization.
Listen to the CERT podcast Structuring the Chief Information Security Officer Organization, featuring Julia Allen and Nader Mehravari interviewed by CERT researcher Lisa Young.
View the SEI Webinar Structuring the Chief Information Security Officer Organization, December 2015.
Additional Resources
By Nader Mehravari
Principal Member of the Technical Staff
Cyber Risk Management Team
More By The Authors
PUBLISHED IN
Cyber Workforce DevelopmentGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


