Insider Threat Incidents: Most Commonly Affected Devices
PUBLISHED IN
Insider ThreatAt the CERT National Insider Threat Center, we collect, analyze, and categorize insider incidents to populate our CERT Insider Threat Incident Corpus and monitor the evolving insider threat landscape. We recently expanded our taxonomy to classify the devices that insiders affect. This post will discuss the types of devices affected by insider threat incidents and how they impact insider risk management and incident response.
Affected Devices
We use the term "affected device" to describe a system that has been altered or leveraged in the course of an insider threat incident. The effects on these devices can range from slight modifications of system file logs to transmission of malicious code that takes a server offline. Intent and motive can vary as well: the insider may directly target the system or device, accidentally impact it over the course of the attack, or modify it to conceal the attack.
Because the CERT Insider Threat Incident Corpus focuses on technical insiders, or insiders who use technology to commit or conceal their actions, at least one device is affected in each included incident. At times, the court records that inform the corpus do not specify what kind of device the insider targeted, only that an organization-controlled device was affected. Even so, our corpus contains more than 500 cases of categorized, affected devices.
Overall, the most commonly affected devices in the CERT Insider Threat Incident Corpus are database servers.
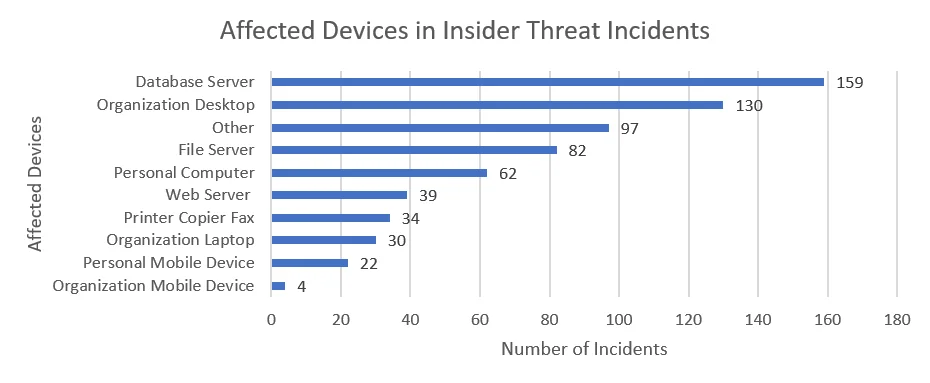
We can further break down the above data to show the distribution of affected devices in each of the four major types of insider incidents: fraud, theft of intellectual property (IP), sabotage, and misuse.
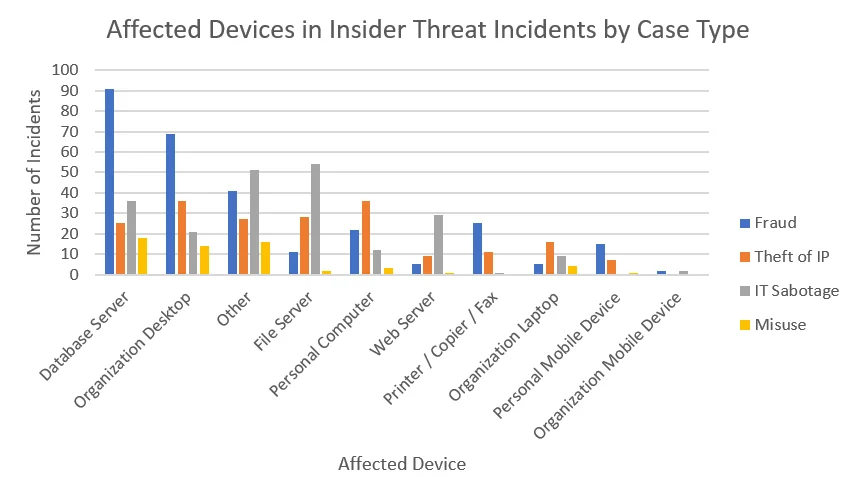
The totals for the most frequently affected devices per insider incident type are as follows:
- Fraud: database servers, followed by organization desktops. These devices may be affected when insiders modify organizational records to conceal missing funds.
- Theft of IP: personal computers and organization-owned desktops. Insider might store stolen IP on organization-owned desktops before exfiltrating the data to their personal devices for later use.
- Misuse: database servers. Insiders may misuse organization access to a database to violate others' privacy.
- IT sabotage: file servers. In many instances, insiders delete critical data from file servers to take systems offline.
Each case type involves a number of other affected devices that do not fit cleanly into our taxonomy. The most common of these devices, with 28 in the corpus, are servers with an unspecified purpose. Other examples include casino machines, point-of-sale (POS) systems, virtual machines, and supervisory control and data acquisition (SCADA) controllers.
Implications for Insider Risk Management: Consider All Affected Devices
The findings from the CERT Insider Threat Incident Corpus underscore the need for insider risk management practices, including scenario development. While traditional risk management approaches might have organizations consider just the assets that malicious insiders ultimately target, such as database servers and web servers, it may be just as worthwhile to consider how other assets (e.g., organization desktops, organization mobile devices) may be leveraged to further an insider attack. The potential for devices to be avenues for data exfiltration, as in fraud or theft of IP, is just as great, if not greater, than their potential to be targeted for disruption, as in IT sabotage. Some practices to consider as part of this risk management approach include the following:
- Implement two-person rules for database modifications and backups of critical data, to prevent loss of availability associated with IT sabotage.
- Deploy endpoint monitoring on organization desktops and laptops to identify anomalous access and downloading of trade secrets and IP.
- Institute mobile device management (MDM) on organization- and employee-owned mobile devices with access to an organization's assets.
- Use encryption systems on organization-owned laptops to prevent ongoing exfiltration once it is detected.
Implications for Insider Threat Incident Response: Consider Personal Devices
Though the acceptance of bring-your-own-device (BYOD) policies varies from organization to organization, the use of personal devices in 84 insider incidents suggests that, at the very least, some insiders are abusing those policies. Court documentation, however, does not always make it clear what policies are in place in victim organizations. It is also possible that insiders were able to bypass technical controls on organization-owned devices or that technical controls were insufficient to reinforce administrative restrictions on the use of personal devices. Regardless of the circumstances, organizations should consider having policies in place to account for forensic examination of employee-owned devices in the event of an insider threat incident.
Conclusion
These results can give some insight about what organization assets should be prioritized for monitoring and analysis, as well as what devices to check during or after an insider attack.
For more information about what controls your organization can put in place to monitor its infrastructure, check out Dan Costa's blog post Improving Insider Threat Detection Methods Through Software Engineering Principles. For other information concerning monitoring and mitigating insider threat, see The Common Sense Guide to Mitigating Insider Threats, Sixth Edition. Watch this blog later this month for a post on communication channels used in insider threat incidents involving collusion.
More By The Authors
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


