4 Technical Methods for Improving Phishing Defense
PUBLISHED IN
Insider ThreatAccording to the Verizon 2018 Data Breach Investigations Report, email was an attack vector in 96% of incidents and breaches that involved social actions (manipulation of people as a method of compromise). The report also says an average of 4% of people will fall for any given phish, and the more phishing emails they have clicked, the more likely they are to click again. The mantra of "more user training" may be helping with the phishing problem, but it isn't solving it. In this blog post, I will cover four technical methods for improving an organization's phishing defense. These methods are vendor- and tool-agnostic, don't require a large security team, and are universally applicable for small and large organizations alike.
1. Separate user accounts from administrator accounts (and use them properly)
A successful phish is usually only the first step that gets attackers into the network. They still must move deeper to gain access to a point-of-sale system, database, or other target of crime or espionage. This access is made immensely easier if the successfully phished target is a network or system administrator. Any elevated access--even just local administrator access on a single machine--makes credential theft and stealthy persistence easier.
Selectively create separate administrator accounts only for users who need them. If possible, restrict these accounts from accessing email and browsers. This restriction decreases the likelihood of an administrator account being compromised and forces the attacker to spend more time and resources escalating on the network. This extra effort increases the likelihood of detection and the attacker's time-to-cost ratio. If you have network monitoring in place, creating separate administrator accounts has the added benefit of increasing awareness of elevated user activity in the network, since these accounts will be used for fewer and more specific tasks.
2. Implement network segmentation
Anything that makes it difficult for attackers to move toward their goal is a security win. Separate users into controlled network segments, either physically or virtually. Users will then only have access to network resources essential to their jobs. Network segmentation makes the target list for an attacker much smaller and helps mitigate the damage a compromised system can have on your network.
An important part of network segmentation is identifying your organization's critical assets and establishing proper access controls for each. Require a jump box or VPN, preferably using two-factor authentication, to access specific, sensitive segments of the network. This will make an attacker's objectives more difficult to obtain and makes tracking and auditing access to those assets much easier. Properly implemented network segmentation has the added benefit of establishing a predictable baseline of "normal" network behavior. Access anomalies will stand out rather than blend in with other events.
3. Harden the host
Phishing comes in two broad forms: credential collection and payload (malware) delivery. Successful payload delivery can lead to a system becoming part of a botnet, installation of a Remote Access Trojan (RAT), or installation of ransomware or cryptoware.
Blocking Microsoft Office macros is one of the most impactful ways an organization can combat malware delivered through phishing, and it can be easily done through Active Directory Group Policy. Also use Software Restriction Policies to restrict common methods of executing scripting languages, such as wscript.exe and mshta.exe, and prevent many common initial payload execution methods. If you're using Windows 10/2016, consider the new Windows Defender Exploit Guard attack surface reduction rules. These rules are outstanding, easy to implement, and go a long way to preventing the majority of common payload execution techniques used by attackers. Finally, make sure to use attachment filtering (or similar methods if not using Microsoft Exchange) to prevent executables and other common file types used by malware from being emailed in your environment. Overwhelmingly, the most common initial payloads are JavaScript (.js), visual basic (.vbs), or Microsoft Office files, and the previously mentioned controls are extremely effective at combatting malicious delivery of these file types.
4. Properly configure your DNS
Properly configuring DNS means setting up SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) for your domain. Much has been written about these protocols, and while their technical specifications are fairly complicated, they aren't terribly difficult to set up.
Briefly, SPF allows an organization to specify which IP addresses are allowed to send emails from the organization's domain. This helps prevent a malicious actor from spoofing that domain and, consequently, sending spoofed emails from that domain to your users.
DKIM essentially uses public and private keys to validate that an email was sent by the organization that claims to have sent it. DKIM limits spam and phishing by allowing the receiving organization to test the validity and ownership of an email.
DMARC overcomes some weaknesses in SPF and DKIM. According to DMARC.org, "The way it works is to help email receivers determine if the purported message 'aligns' with what the receiver knows about the sender. If not, DMARC includes guidance on how to handle the 'non-aligned' messages." DMARC policy allows senders to create "rules" that give email providers actions to take if the message received from the sender does not properly authenticate.
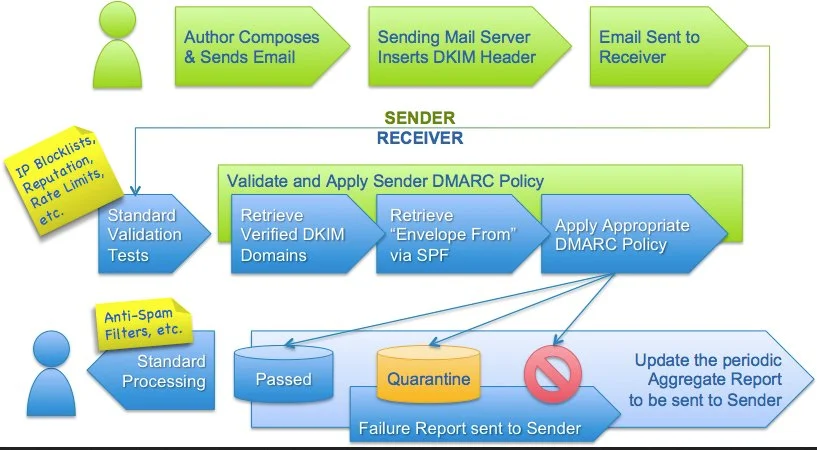
DMARC Example (source: https://dmarc.org/overview/, used under license CC By 3.0 by DMARC.org)
SPF, DKIM, and DMARC make it harder for an attacker to pose as your organization and create convincing phishing campaigns. As a bonus, they also help protect your reputation by preventing attackers from spoofing emails from your organization to others.
Conclusion
Phishing awareness training is important, but someone almost always takes the bait. The four technical methods I described require no new products or purchases and can be implemented by most IT staff with the right support. Check out a previous post by my colleague Mike Albrethsen on other technical defenses against phishing.
No single technical method or product is a silver bullet. Implemented together, however, they can help prevent phishing attacks against your organization.
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
