The Frequency and Impact of Insider Collusion
PUBLISHED IN
Insider ThreatCollusion among malicious insiders can produce a larger attack surface in terms of access to organizational assets. In theory, multiple actors could perform reconnaissance from within the "need-to-know" aspect of their job responsibilities to commit fraud or theft of intellectual property. Consequently, these malicious actors could then evade detection, presenting a real threat to an organization. In this blog post, I explore the concept of collusion among malicious insiders.
For the purposes of this analysis, collusion refers to incidents in which insiders work together to commit an attack against an organization as opposed to using social engineering to manipulate other employees (i.e., an employee did not intentionally or consciously realize that they were manipulated by another insider as part of an attack).
Currently, at least 395 incidents of those in CERT's insider threat data set (48.32%) involve insiders working with known accomplices, including outsider accomplices and/or insider accomplices. More specifically, about one-third of those (137 incidents) involve insiders working with accomplices within the victim organization. Ergo, at least 16.75% of the entire insider threat data set involve insiders working with other insiders.
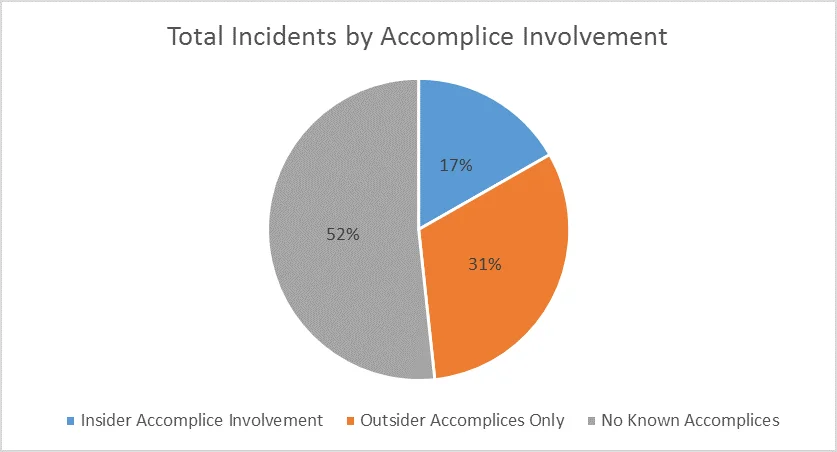
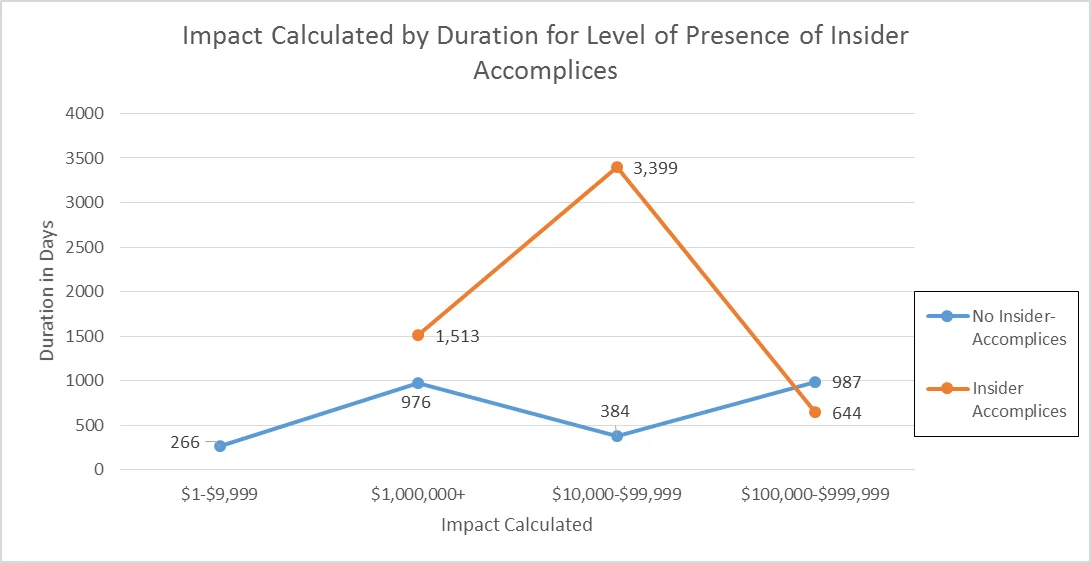
Many collusion incidents with insider accomplices involved fraud (51 incidents, 37.23%), theft of intellectual property (45 incidents, 32.85%), or a combination of the two (8 incidents, 5.84%). For the 46 incidents of insider collusion where the duration was known, the average duration was 989 days (2.7 years). Within the overall data set, excluding the incidents involving collusion, there were 384 incidents where the duration of the incident was known, which had an average duration of 234 days (0.64 years).
Therefore, on average, an incident that involves collusion will have a duration that is nearly four times as long as one that is committed solely by a single insider. The following chart displays the average duration in days of incidents without and with insider accomplices as related to financial impact.
One insider collusion incident involved a group of three insiders (an insider-leader with two accomplices) who were able to embezzle millions of dollars in taxpayer dollars from a local government over the course of a decade. In at least twelve other incidents, insider collusion resulted in the creation of identity documents to benefit criminal enterprises and, in some incidents, illegal aliens.
Looking into malicious insider collusion incidents on the whole, trends emerge as to the financial impact they have on organizations.
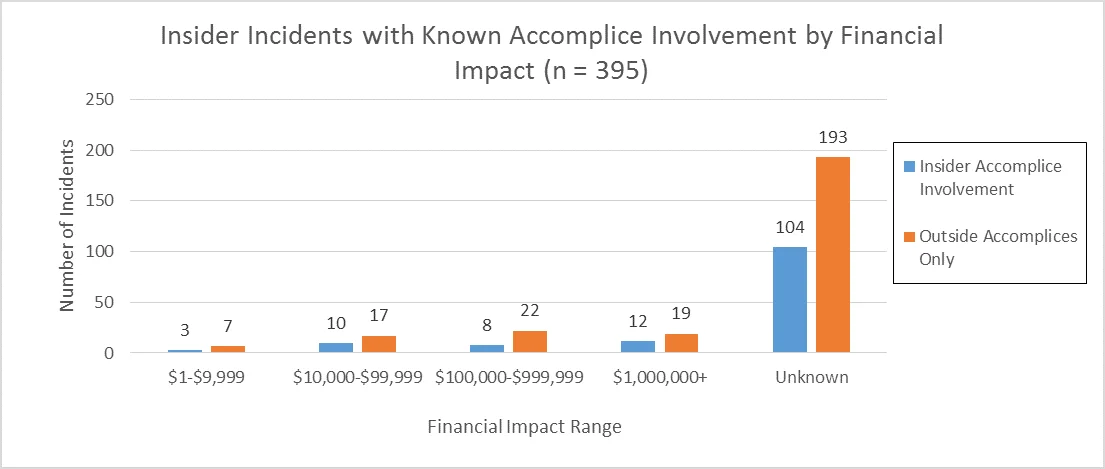
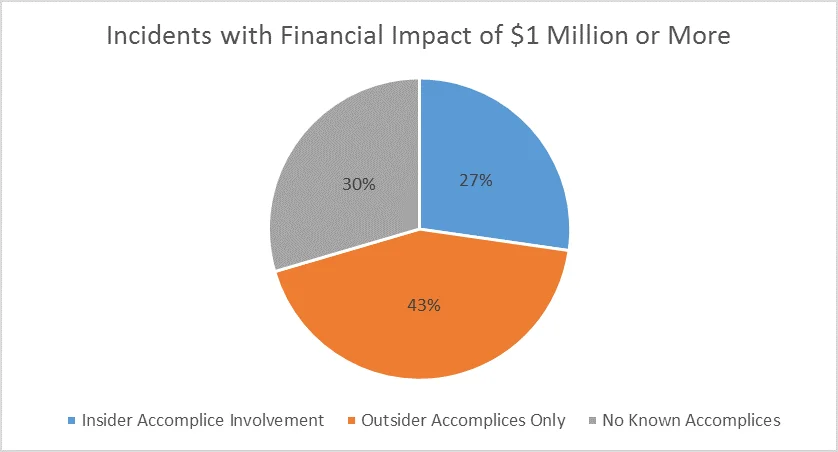
Note: Some incidents with impacts of $1 million or greater involved no known accomplices of any kind.
Twelve of the incidents that involved insider collusion had a financial impact to the organization of $1 million or greater. In comparison, only 44 of 818 incidents in CERT's Insider Threat Incident Corpus (5.3%) had an impact of $1 million or greater.
In other words, 27.27% of the incidents with a financial impact of $1 million or greater were taken from a subsample of insider collusion incidents that represent 16.75% of the overall sample. So the incidents with insider collusion disproportionally account for the incidents with the greatest financial impact.
Note the differences in the following chart, which shows the incidents with a financial impact of $1 million or greater by accomplice type.
With an ever-evolving threat landscape, organizations may want to consider the intersection of technical methods and social interaction when developing insider threat programs.
Refer to CERT's Common Sense Guide to Mitigating Insider Threats - 4th Edition for best practices that can help prevent and respond to insider threat incidents.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
