Life Beyond Microsoft EMET
PUBLISHED IN
Security VulnerabilitiesApproximately eight years ago (September 2010), Microsoft released EMET (Enhanced Mitigation Experience Toolkit) 2.0. In the world of software defenders, there was much rejoicing. EMET allows users to not be at the mercy of their software vendors when it comes to opting in to vulnerability exploit mitigations.
As we fast-forward to November 2016, Microsoft released a blog post called Moving Beyond EMET, which announced the end-of-life (EOL) date of EMET and explained why Windows 10 makes EMET unnecessary. I took issue with this blog post, primarily because, at that time, Windows 10 could NOT provide opt-in, application-specific protections like EMET can.
Microsoft dropped support for EMET on July 31, 2018. Let's see what has changed and what we can do to protect ourselves on Windows systems today.
Windows Defender Exploit Guard
Microsoft Windows 10 version 1709 (also known as Fall Creators Update, Redstone 3, or RS3) introduces a new feature called Windows Defender Exploit Guard (WDEG). While WDEG truly does add EMET-like capability to Windows 10, it wasn't released until the fall of 2017, which is one year after Microsoft published the Moving Beyond EMET blog post. Only since the 1709 release of Windows can we truthfully say that "Windows 10 includes all of the mitigation features that EMET administrators have come to rely on." In particular, because it now allows us to lock down applications that may not have chosen to opt in to all of the appropriate exploit mitigations.
WDEG Application-Specific Settings
In my testing, WDEG in current versions of Windows 10 automatically includes application-specific settings, similar to what you get in the EMET "Recommended Software" protection profile:
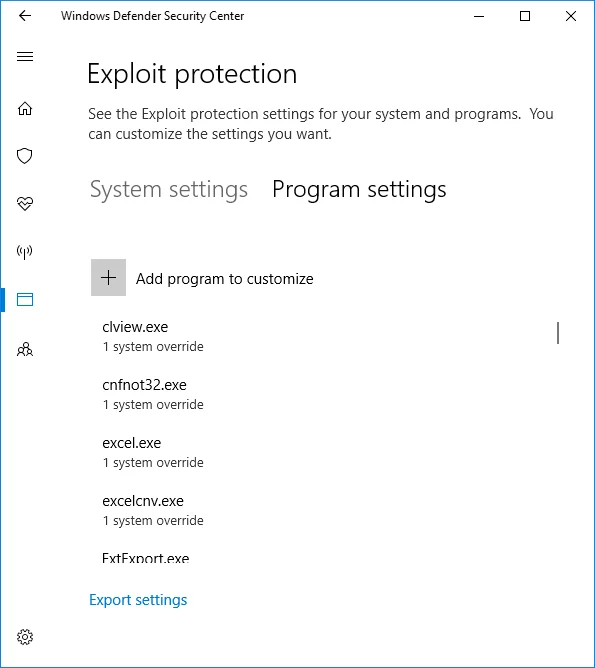
The applications configured in this part of WDEG have extra protections beyond the baseline defaults of Windows 10.
WDEG System-Wide Settings
In the WDEG Exploit protection section, it's important to understand the language that Microsoft uses. In particular, it's imperative to realize that "Use default (On)" does NOT mean the same as "On by default." It may help to look back at EMET to understand why these two settings are different. With system-wide settings in EMET, the setting "Application Opt In" is different (and less secure) than "Always On." Consider the following EMET screen:
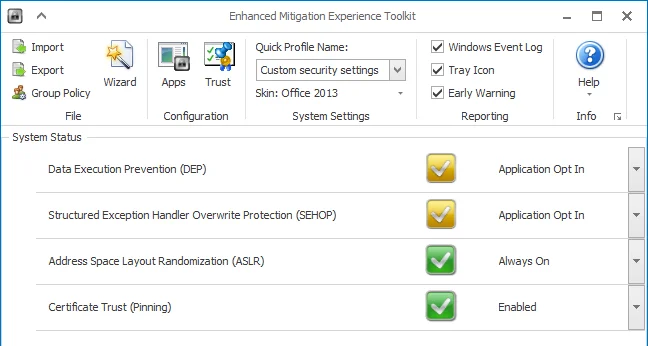
Here we can see that ASLR is set to "Always On," while DEP is set to "Application Opt In." "Always On" is the more secure setting. Now let's look at one of the WDEG system-wide settings (Bottom-up ASLR):
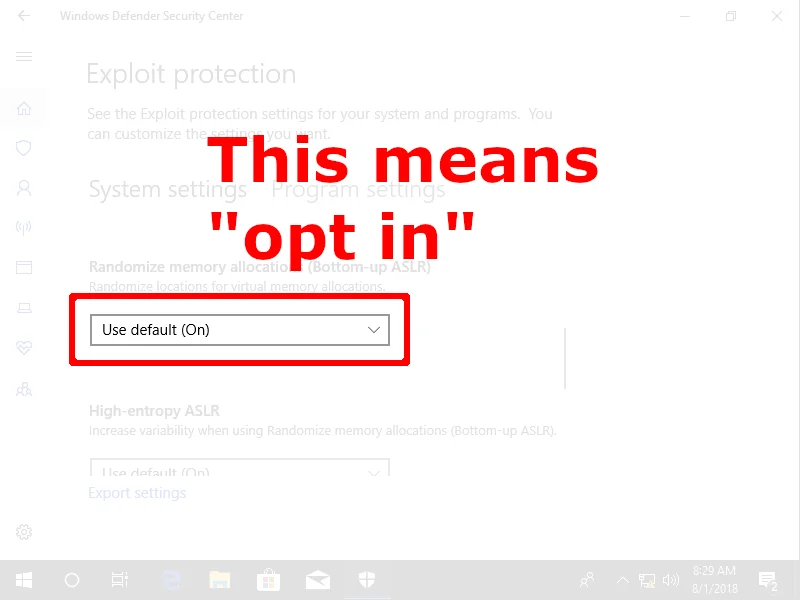
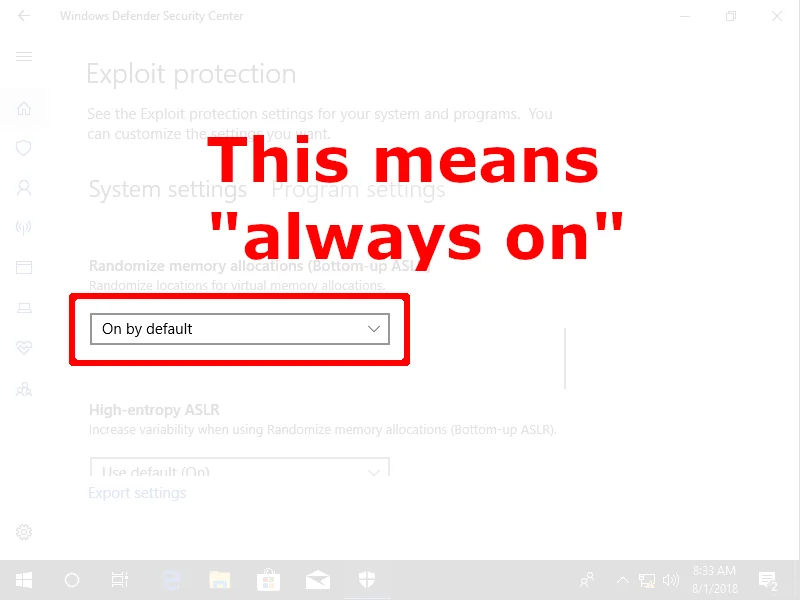
Both options include the words "default" and "on," but if you have selected anything other than "On by default," you may not be getting the protections you think you are getting.
Importing EMET Profiles into WDEG
For people who have invested effort into deploying EMET, you may be pleased that Windows 10 includes the ability to convert an EMET protection profile to a WDEG protection profile using PowerShell. The resulting protection profile can be directly imported into Windows 10 WDEG.
Here Be Dragons
Although Windows 10 build 1709 introduced the ability to import an EMET profile into WDEG, it is important to know that this feature isn't used unless you are running Windows 10 build 1803 (also known as the April 2018 Update, Redstone 4, or RS4). Depending on the mitigations present in the EMET protection profile that is imported, Windows 10 builds prior to 1803 may result in a system crash (BSOD) upon booting:
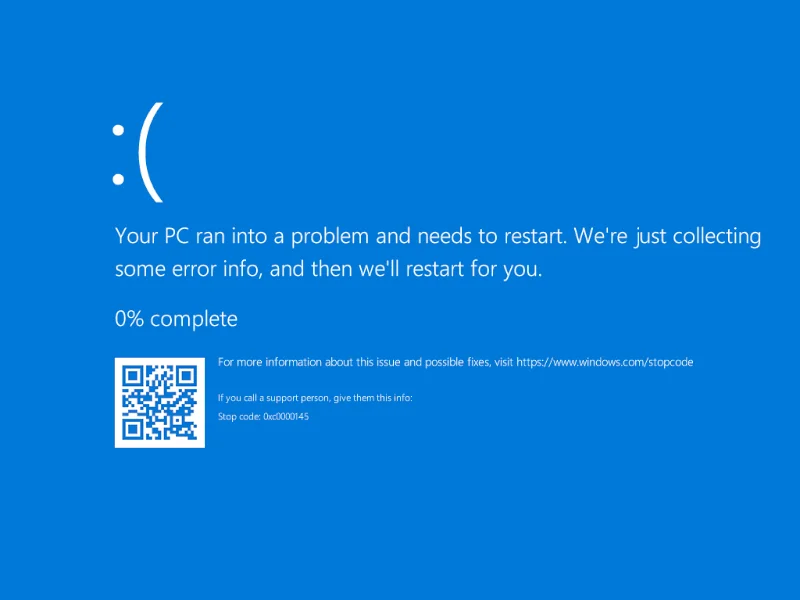
This crash occurs because the PayloadRestrictions capabilities are intended to be enabled per-process on Windows 10. But until version 1803 of Windows 10, importing an EMET protection profile can cause the PayloadRestrictions capability to be installed at a system-wide level as well. This results in Windows smss.exe failing to start, which results in the above system-wide crash screen.
If you end up in this situation, removing the HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Kernel\MitigationOptions registry value allows Windows 10 to boot again. Just realize that this action will undo any system-wide mitigations that may be present.
Advice for Users Not Running Windows 10
Personally, I have a love/hate relationship with Windows 10. On one hand, Windows 10 is arguably the most exploit-resistant version of Windows, thanks to the brilliant minds of Matt Miller and crew. On the other hand, there are other minds at Microsoft that are tasked with directly monetizing the platform.
This monetization results in systems that spontaneously end up with apps like Candy Crush Soda Saga and Disney Magic Kingdoms shoved down their throats:
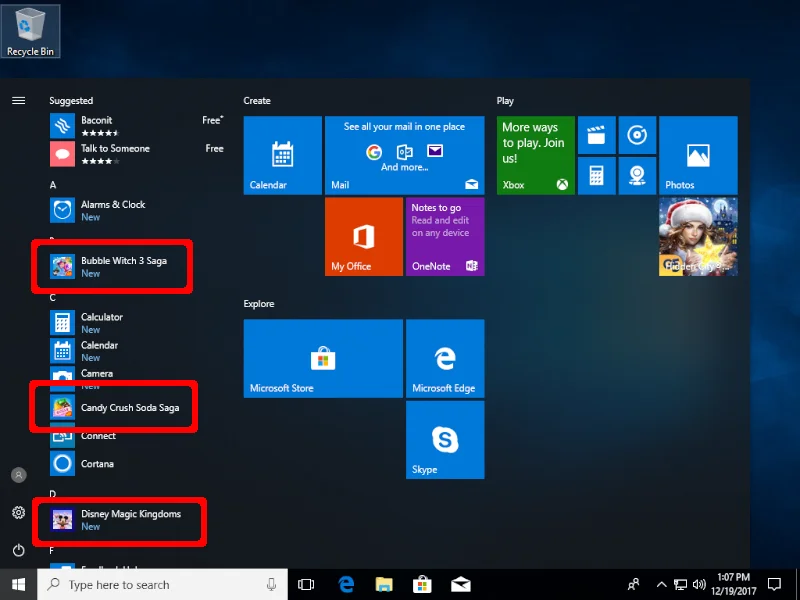
One problem with unwanted software being installed without user interaction is that your hard drive will continually be filled up. But perhaps, more importantly, this behavior results in an ever-increasing attack surface within Windows 10.
If you don't happen to be running Windows 10, what does this mean for exploit protection strategies now that EMET is no longer supported?
The fact that EMET 5.52 is no longer supported by Microsoft does not mean that you need to uninstall it from your systems. EMET provides viable protections against successful exploitation memory corruption and other vulnerabilities. Continuing to use unsupported software is a bad idea in the general sense. However, EMET is a special case, since its presence makes it less likely for it to be compromised, regardless of its official support status.
The exploit mitigations present and available in Windows 10 are fast eclipsing prior Windows versions. But if you are running a version of Windows prior to Windows 10, having EMET installed is still a good idea.
Conclusion and Recommendations
As of version 1709, Windows 10 finally has EMET-like capabilities in the form of Windows Defender Exploit Guard. As of version 1803, Windows 10 has an upgrade path to safely import EMET configuration profiles. With this knowledge and the topic covered in this blog post, I can offer the following advice:
- Users of Windows 10 version 1803 and newer should import existing EMET protection profiles they used in the past.
- When configuring WDEG, be sure to understand the difference between "Use default (on)" and "On by default." The former setting is used for a default-configured Windows 10 platform, while the latter is used in hardened Windows 10 environments.
- Windows versions older than 10 should continue to use EMET, as it will continue to provide protection against a number of vulnerability classes.
More By The Author
More In Security Vulnerabilities
PUBLISHED IN
Security VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Security Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
