Who Needs to Exploit Vulnerabilities When You Have Macros?
PUBLISHED IN
Security VulnerabilitiesRecently, there has been a resurgence of malware that is spread via Microsoft Word macro capabilities. In 1999, CERT actually published an advisory about the Melissa virus, which leveraged macros to spread. We even published an FAQ about the Melissa virus that suggests to disable macros in Microsoft Office products.
Why is everything old new again? Reliability of the exploit is one reason, but the user interface of Microsoft Office is also to blame.
Exploiting Vulnerabilities
Attackers like to target weaknesses in the design of an application whenever possible. Using implementation bugs, such as ones that can be found through fuzzing, can be viable for an attacker. Successful and reliable exploitation can rely on a number of variables, such as
- What OS is the target running?
- What version of the vulnerable software is being used?
- Is Microsoft EMET being used?
In some cases, an exploit for a vulnerability may only work on very specific targets. Attackers look for the widest range of compatibility for their exploits.
Exploiting Design Weaknesses
Design weaknesses are a much more valuable target for an attacker, as opposed to an implementation flaw that relies on memory corruption, for example. The benefit of such weaknesses is that they can work universally. For example, consider the Microsoft Windows design flaw that caused Windows to automatically execute code that is specified in shortcut files. This weakness was used by the Stuxnet worm.
Microsoft Office Macros
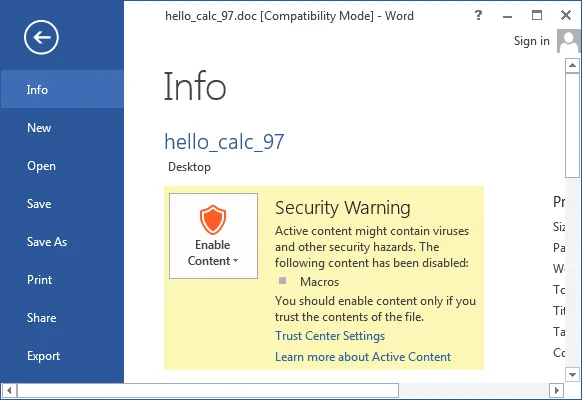
Malicious Microsoft Office documents that leverage macros are exploiting capabilities that are provided by Microsoft Office by design. Microsoft Office macros can help automate repetitive tasks, but in the end they are equivalent to running native code. As a proof of concept, I made a simple Word document that launches calc.exe by way of a one-line VBScript macro. The screenshot below is from Office 2013 running on Windows 7.
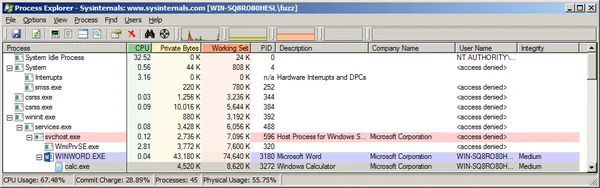
Word does give me a warning about the document having a macro, but how well does the program convey the potential dangers of enabling the macro?
A Trip Down Memory Lane
Microsoft Office for has provided some level of warning to the user, and has required some steps to enable macros before they are executed. However, both of these aspects of enabling macros have changed over the versions of Office for Windows.
Office 97
Microsoft Office 97 was pretty clear that enabling macros can harm your computer:
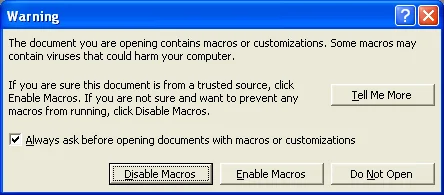
The options to proceed include
- Disable Macros - Open the document, but with macros disabled
- Enable Macros - Open the document with macros enabled
- Do Not Open - Do not open the document
- Tell Me More - Give the user details about the risks of opening a document with macros:
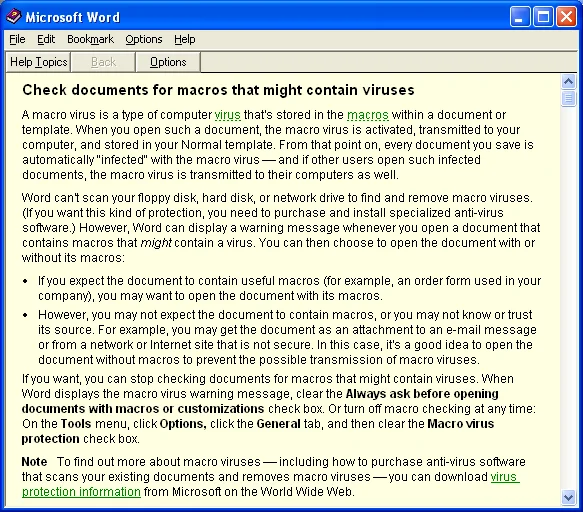
Even with these warnings, the Melissa macro virus still spread in 1999.
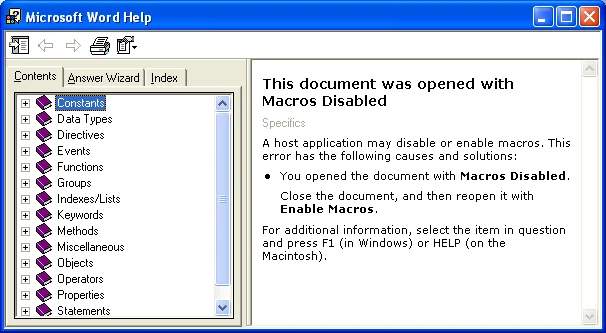
Office 2000
Starting with Office 2000, the dialog was a little less informative. However, the possible actions to take are safer for the user:
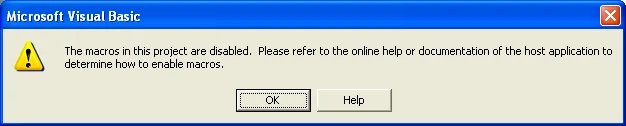
- OK - Open the document, but with macros disabled
- Help - Give the user details about the risks of opening a document with macros:
Office XP
Office XP has similar dialogs, functionality, and help as Office 2000.
Office 2003
Office XP has similar dialogs, functionality, and help as Office 2000 and Office XP.
Office 2007
Office 2007 appears to be the first version of Office where the traditional dialogs have been abandoned. Presumably this was done to avoid the "dialog fatigue" problem that could lead users to give in and make a poor decision.
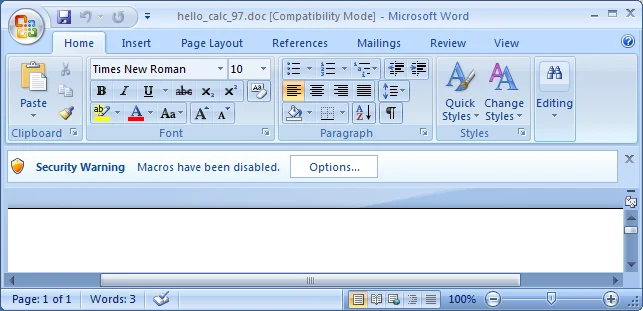
Here, the warning bar isn't very clear about the potential consequences of macros. But there is only one option to proceed:
- Options - Display additional information and options at the same time:
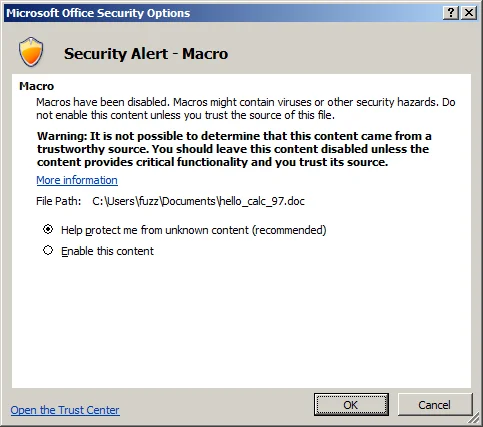
From this dialog, there are several options:
- OK - Open the document, but with macros disabled
- Cancel - Close dialog, but leave warning bar at the top
- Enable this content - Open the document with macros enabled once OK is clicked.
- Open the Trust Center - Open a dialog that allows macros to be disabled without prompting the user:
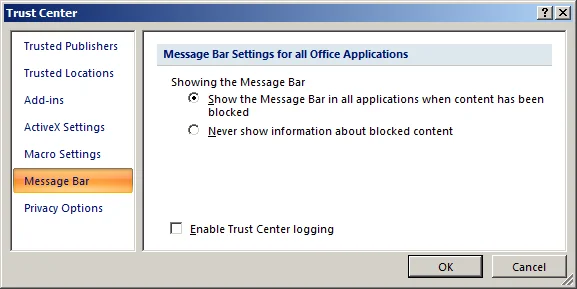
The Office 2007 options seem reasonable. The default is to block macros, but the user is given the option of enabling them on the same screen that clearly indicates the risk.
Office 2010
Presumably with the goal of simplifying the options presented to the user, Office 2010 changed the Message Bar functionality:
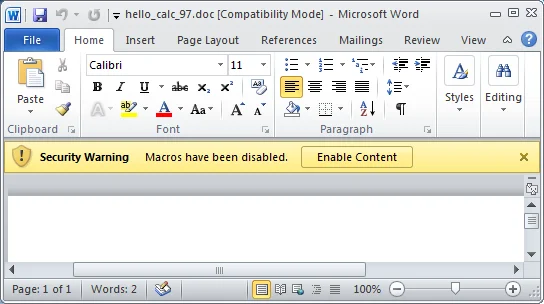
Here the user seems to be given one option:
- Enable Content - Run the macros present in the document
From a security perspective, this approach is a step backwards. The user is not given any information about the consequences of enabling macros, and the user is given only one obvious option: enable macros. This is dangerous. Attackers are using several social engineering techniques to convince users to click the "Enable Content" button as well.
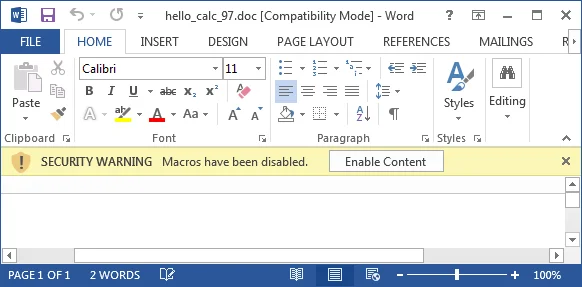
Office 2013
The Office 2013 experience appears identical to that of Office 2010:
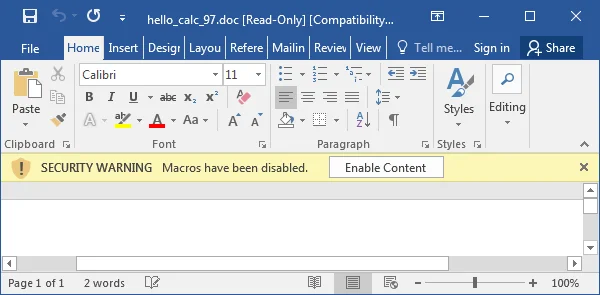
Office 2016
The Office 2013 experience appears identical to that of Office 2010 and 2013:
Microsoft Office 2016 for Mac
Microsoft Office 2016 for Mac has a macro experience similar to Microsoft Office 97 for Windows:
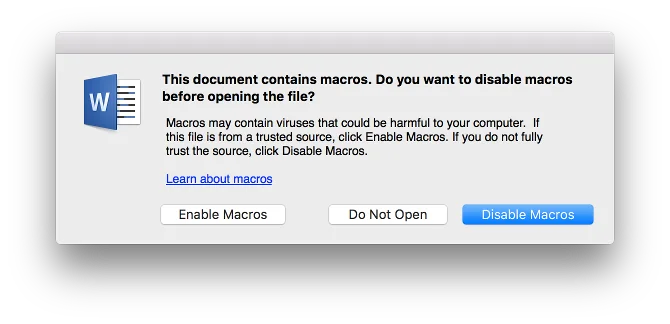
It does not appear to be possible to permanently disable macros in the Mac versions of Microsoft Office. The Disable Macros button in the above dialog is only valid for the current document in the current session. While there is a Macro Security option in the preferences:
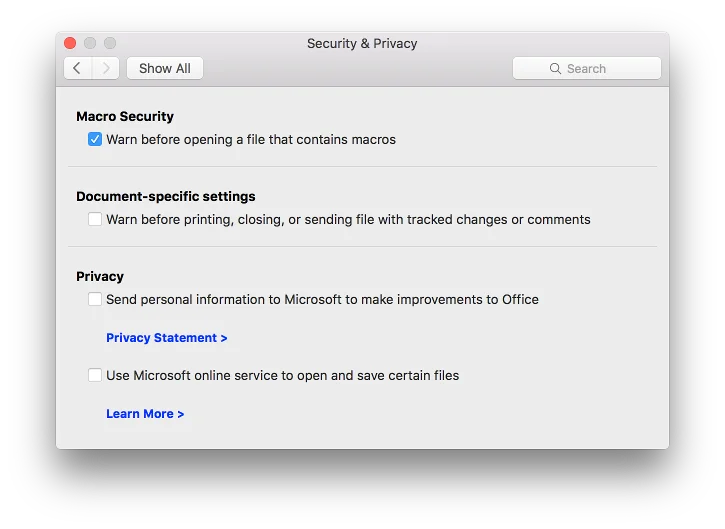
The only setting is Warn before opening a file that contains macros. There is no option to disable macros. Unchecking this box will leave macros enabled, but there will be no warning before they are executed. Do not uncheck this box, as that change would put Office in a very dangerous configuration!
Macro Protections
Unfortunately, the default Microsoft Office settings for macros are not secure. Users of newer versions of Office (2010 or 2013) are even more likely to enable macros without understanding the consequences of doing so. Luckily, Microsoft has provided guidance for how to restrict macro functionality. These changes can be rolled out via Group Policy, which should aid in enterprises being able to configure Office in a secure manner.
The options are
- Enable all macros
- Disable all macros with notification
- Disable all macros except those digitally signed
- Disable all macros without notification
Option 2 above is the less-secure default option for Microsoft Office. Option 4 above is the most secure, as it will eliminate the chance of a user inadvertently executing a malicious macro.
Some enterprises may have legitimate uses for Office macros, however. In such situations, questions that must be answered include
- Who in my enterprise has a business need for macros?
- Of those officially sanctioned uses for macros, what Microsoft Office applications need the macro capability?
The first question is important from an attack surface perspective. For example, let's say that my 10,000-person organization has 10 people in finance that need macro capabilities, but the other 9,990 people do not. It makes no sense to give everybody the ability to execute macros.
The second question also helps protect the systems that need some sort of Office macro capabilities. In the example above, let's say that the 10 people in finance only use macros in an Excel spreadsheet that they use. In this case, macros should be disabled without notification for all Microsoft Office components except Excel (e.g., Word, PowerPoint, Project). And for Excel itself, the more-secure setting would be "Disable all macros except those digitally signed." This way, the organization can sign the approved macros. When Excel opens a malicious file with an unsigned macro, the macros will be silently blocked.
Office 2010, 2013, and 2016 Revisited
As it turns out, Office 2010, 2013, and Office 2016 can show the user details about what enabling macros can do. In the following example

the phrase "Macros have been disabled" is actually clickable. This doesn't seem obvious to me, and I suspect other users may not realize it as well. Only in the late stages of preparing this blog entry did I realize that "Macros have been disabled" is clickable. If the user does click on that phrase, a dialog is presented that explains the risks of enabling macros:
This information is hidden far enough away from the "Enable Content" button that I suspect not many people would even see it.
Conclusions
Macro viruses are back. See
The default behavior of Microsoft Office has usually allowed for inadvertent execution of malicious macros, but recent versions of Microsoft Office make it much easier for the user to make the wrong decision.
If you wish to protect your systems, restrict access to macros. Regardless of the level of information provided to an end-user, don't always rely on that user to make the right choice.
Solutions
Disable Microsoft Office macros for as much of your organization as is practical. If you are using Office 2016 or Office 365, the simplest option is to enable the feature that blocks macros in documents that originate from the internet.
For all other Office versions, it is important to disable macros without notification for all Microsoft Office applications by default for all systems. For systems that do need macro capabilities:
- Only enable macros for certain users or groups.
- For those users or groups that need macro functionality, only enable macros for applications that need them. For example, if you have a business need for Excel macros, only allow macros in Microsoft Excel, and be sure that they are disabled for the other Office applications.
- Only allowing signed macros can reduce the fraction of attacks that could be successful. However, be aware that attackers may be able to obtain trusted signing keys for macros.
- As a last resort, consider using the Trusted Locations feature of the Microsoft Office Trust Center. When a document is loaded from a Trusted Location that is configured, macros will be enabled regardless of the macro settings specified in the Trust Center. Also note that Protected View is also disabled in the Trusted Location. While documents in a Trusted Location bypass a number of protections that Office provides, limiting macro-enabled documents to this location can greatly reduce the attack surface of your Microsoft Office deployment.
More By The Author
More In Security Vulnerabilities
PUBLISHED IN
Security VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Security Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
