Instant KARMA Might Still Get You
PUBLISHED IN
Security VulnerabilitiesAbout a year ago, I started looking into Android applications that aren't validating SSL certificates. Users of these applications could be at risk if they fall victim to a man-in-the-middle (MITM) attack. Earlier this year, I also wrote about the risks of MITM attacks on environments that use SSL inspection. Lately I've been checking whether IOS applications are consistently checking SSL certificates, and they appear to be pretty similar to Android applications in that regard.
Some might wonder how easy it might be to fall victim to an MITM attack. The KARMA attack, which was outlined over ten years ago, can cause a client system to unknowingly connect to an attacker's Wi-Fi, allowing an MITM attack. Despite the age of this attack, I've found that it can still be effective on modern platforms.
KARMA Explained
The KARMA attack takes advantage of clients that send probe requests to determine which wireless networks are nearby. The attack is relatively straightforward, but I find that some pictures can help illustrate the situation. First, let's look at an association that is not vulnerable to KARMA:

The Wi-Fi access point periodically sends out a beacon frame that indicates the network SSID, which identifies the Wi-Fi network. When a client system receives a beacon frame with an SSID that it remembers, it may associate with the wireless network.
Now let's look at a client system that is vulnerable to KARMA:

Rather than passively monitoring beacon frames from access points, the client here sends out a probe request for networks that it knows about. The KARMA attack becomes obvious. The attacker simply needs to listen for the client to send a probe and respond as the SSID that the client requested. The impact is that a client system may connect to a network other than the one the user expects. At this point, the attacker can perform MITM or other attacks on the client system.
Wi-Fi and Authentication
Before getting into too much detail about KARMA, it's important to understand how most wireless networks handle authentication. When you connect to an open wireless network called "coffeeshop," how do you know that it really is the coffee shop that you think it is? The short answer is that you don't. In the case of an open Wi-Fi network, the SSID is pretty much the only thing that a client uses to determine what network is being advertised. And the SSID is something that is easily under an attacker's control.
If an attacker is hanging out in your coffee shop and has a stronger signal or if he/she otherwise interferes with the legitimate coffee shop wireless access point, customers will likely connect to the attacker's access point. And at this point, the attacker can carry on any MITM or other attacks that he/she likes. This is known as the evil twin attack.
For wireless networks that use encryption, such as WPA2, a client system will not associate with an access point that does not use the same passphrase. This practice prevents a client system from immediately connecting to the network; however, it can give the attacker the ability to crack the password if it's weak.
KARMA vs. Evil Twin
KARMA improves on the simple evil twin attack. The evil twin attack requires the attacker to be in range of the user's intended network to attack. However, with KARMA, an attacker can target client systems even when they are away from the networks they use. For example, if I am using a client system that is vulnerable to KARMA, my client may associate to a wireless access point that identifies itself on-the-fly as "coffeeshop," even if my real "coffeeshop" network is hundreds of miles away.
The other way that KARMA is more effective than the evil twin attack is that it is a more subtle attack. If my coffee shop notices a rogue access point with the same SSID of "coffeeshop," then it's pretty clear that there is some sort of foul play going on. With KARMA, the attack is more subtle in that the attacker does not broadcast the SSIDs that he/she is attacking. The rogue access point simply responds on demand to whatever probes it receives.
Hidden SSIDs and KARMA
When setting up a wireless network, some people may choose to enable the feature to hide the SSID. Originally, the thinking was that if the SSID is not broadcast, then it will be less likely to be targeted with an attack. By now, the myths about a hidden SSID being more secure have been debunked. The most important part related to KARMA is that if your client is configured to connect to hidden SSIDs, it will send out probes for those networks.
KARMA in 2015
Since the KARMA attack is over ten years old, it surely doesn't affect modern platforms, right? Sadly, that's not the case. Many modern platforms can be affected by KARMA in some way.
OS X
One platform that is still vulnerable to KARMA is Mac OS X. Even with the latest Yosemite version (10.10.4), turning on Wi-Fi will cause probes to be sent. If OS X has at least one open network remembered, then it could associate with a KARMA attacker's network without the user noticing.
Windows
I tested Windows 7. By default, Windows does not send out probes for wireless networks, and therefore does not appear to be vulnerable to KARMA. However, I discovered that the wireless adapter that I was using for testing can make Windows vulnerable to KARMA. When installing the affected software, the default option is to install the driver and a wireless configuration utility. There is an optional way of running the installer that only installs the driver. As it turns out, the wireless configuration utility configures Windows in a way that makes it vulnerable.
When the affected software is used to connect to a wireless network, it creates a Windows network profile that is vulnerable to KARMA:
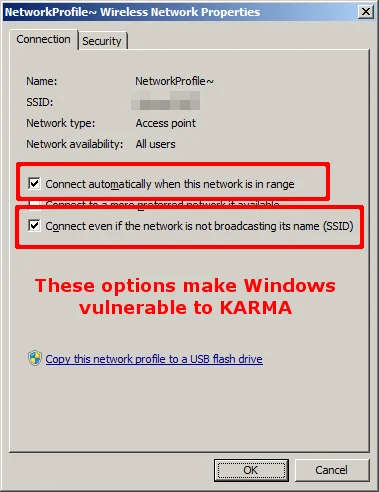
The option to "Connect even if the network is not broadcasting its name (SSID)" guarantees that Windows will send out a probe request, and the "Connect automatically when this network is in range" option causes the network connection to happen without any user interaction. Those two options combined result in a KARMA-vulnerable system.
Ubuntu Linux
There are plenty of different Linux distributions. Even within a single distribution, you can end up with various configurations that use different network managers. I looked at the default install of the most recent LTS desktop release of Ubuntu, which is 14.04. This platform is vulnerable to the KARMA attack. It will send probes for networks that it has connected to in the past and will happily connect to an attacker's KARMA network.
Android
Older versions of Android, such as Gingerbread, are vulnerable to KARMA. Stock newer versions of Android (I tested "Ice Cream Sandwich" version 4.0.4) appear not to be affected, assuming the user has never saved a manually-added network. Saved networks that have had their SSIDs manually added will cause Android to send probe requests and be vulnerable to KARMA.
IOS
In my testing, Apple IOS devices fared well against KARMA. However, if an attacker is within radio range of the network being joined, an IOS device may join the attacker's KARMA network rather than the intended one.
All the Rest
It's probably obvious by now that it would be impractical to list the KARMA vulnerability status of all things that talk Wi-Fi. In my testing, I used a MAC address whitelist to limit Wi-Fi associations to my own devices. However, during the testing, some other devices nearby attempted unsuccessfully to associate with my KARMA hotspot. I saw an association attempt from a Barnes & Noble MAC address. One might conclude from this that at least one version of the NOOK is vulnerable to KARMA. I also saw an association attempt from a Blackberry Limited MAC address. So at least some form of a Blackberry device is vulnerable to KARMA. These days almost everything talks Wi-Fi, so comprehensively testing all the Wi-Fi-enabled things is not practical.
Conclusions and Recommendations
Vulnerability to KARMA is not a black-and-white situation. There are multiple factors that can affect how vulnerable a system is to KARMA. Some platforms are definitely more vulnerable than others. What are we to do about it then? Luckily, there are actions that we can all take.
To be on the safe side, assume that your device IS vulnerable to KARMA. When using a KARMA-vulnerable system, there are several precautions that you can take to limit your exposure:
- Don't use open Wi-Fi. The use of open Wi-Fi networks can open your system to evil twin and KARMA attacks. Beyond those attacks, open Wi-Fi networks allow others on the same network to more easily observe traffic of others on the network.
- Clear out any open Wi-Fi networks that your system remembers. The steps to perform this action will vary from platform to platform. It is important to realize that any open network that you have ever connected to during the life of your system can open it up to KARMA attack right now. Note that some platforms, such as Apple IOS, only allow users to forget Wi-Fi networks that are nearby at the time.
- Restrict saved networks to a specific BSSID. Some platforms, such as Linux NetworkManager, can allow saved networks to only associate with a specific BSSID (MAC address). By setting this option, the client should only automatically associate with the wireless network that the user has selected, rather than a KARMA attacker.
- Use strong passphrases for any encryption-protected networks that you use. If a KARMA-vulnerable system has a remembered network with a weak password, then an attacker may be able to crack the password and subsequently gain access to the network.
- Do not use a network with a hidden SSID. When a client connects to a network with a hidden SSID, the client sends a probe request for the SSID name. This means that an attacker knows exactly what network(s) the client is looking for, allowing the KARMA attack to work. A client with a remembered open network that has a hidden SSID is virtually guaranteed to be vulnerable to KARMA.
- Pay attention to the Wi-Fi networks that your device connects to. With most platforms, the Wi-Fi status simply indicates "connected" or "not connected" unless you dig into the details. Especially since Wi-Fi connections can fluctuate, it can be impractical to click into the Wi-Fi details constantly. Some applications can help indicate, without requiring clicks, the current Wi-Fi status, such as which SSID the system is connected to.
- Disable Wi-Fi when you're not using it. Leaving Wi-Fi enabled constantly causes an increased attack surface. Whether it's KARMA or other Wi-Fi-related attacks, leaving Wi-Fi off when it is not required can help to keep a system safer.
More By The Author
More In Security Vulnerabilities
PUBLISHED IN
Security VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Security Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
