The 13 Key Elements of an Insider Threat Program
PUBLISHED IN
Insider ThreatIn the last three years, since the arrival of the COVID-19 pandemic in the United States, the nature of the workplace has changed significantly. As of February, 76 percent of the workforce with a job that can be done from home in the United States was working a hybrid or completely remote schedule, according to Pew Research. Of that number, roughly one-third is completely remote.
In this evolving work climate, organizations need to be increasingly vigilant against malicious and unintentional (non-malicious) insider incidents. Many organizations never experience a headline-grabbing, large-scale insider incident. Instead, many insider incidents are accidental or non-malicious, typically the result of a security incident or policy violation. According to our research, distraction is a key factor in unintentional insider threat incidents. Distracted workers are more likely to make mistakes that can endanger an organization, such as failing to use their company's virtual private network (VPN) or clicking on phishing links in email. For many hybrid and remote workers, distractions involving workspaces in close proximity to children and other family members can lead to unintentional risk. Comprehensive enterprise risk management that includes an insider risk program is a key component to securing organizations in this new environment. In this post, we present the 13 key elements of an insider threat program.
Requirements Related to Insider Threat
In 2011, the U.S. federal government released an executive order requiring government agencies that operate or access classified computer networks to build a formal insider threat detection and protection program.
The federal government had been previously charged with building the National Insider Threat Task Force, which develops a government-wide insider threat program for deterring, detecting, and mitigating insider threats.
In 2016, the National Industrial Security Program Operating Manual (NISPOM), which outlines government standards for defense contractors, via NISPOM Confirming Change 2, also adopted a requirement that members of the Defense Industrial Base (DIB) build insider threat detection and protection programs. DIB members, like the government agencies, must conduct yearly self-assessments of established insider threat programs or independent third-party assessments.
A number of high-profile incidents have impacted for-profit companies as well, resulting in significant momentum to build insider threat programs in the private sector.
Within the CERT National Insider Threat Center, we have developed a number of resources to help public- and private-sector organizations assess the risk posed by trusted insiders. These resources focus on helping organizations understand the critical components of an insider risk program and by what metrics a program is deemed effective. We can also conduct third-party evaluations of insider threat programs for government or for-profit entities.
These resources include the CERT Common Sense Guide to Mitigating Insider Threat, Seventh Edition, which outlines 22 best practices that organizations can use to mitigate insider threat. Each best practice includes strategies and tactics for quick wins and high-impact solutions, mitigations to minimize implementation challenges and roadblocks, and mappings to notable and relevant security and privacy standards. Best practice #2, Develop a Formalized Insider Risk Management Program, provides a roadmap for organizations to follow.
Other resources include
- CERT Insider Threat Program Evaluator Certificate
- CERT Insider Threat Program Evaluator Certificate
- CERT Insider Threat Vulnerability Assessor Certificate
- Building an Insider Threat Program
- Insider Threat Analyst
- Insider Threat Awareness Training
- Insider Threat Test Dataset
The Why and When of Insider Risk Management
Incorporating insider threat into enterprise-wide risk management allows the program or organization to leverage existing resources by
- avoiding duplication of effort with existing security controls focused on external threat mitigation
- ensuring the insider risk program has participation from across the organization, proving threat intelligence (information) from risk management, information technology, physical security, personnel management, human resources, risk management, general counsel, and lines of business.
When considering insider threats, it is important to first develop a risk management mindset. A risk management mindset understands that the best time to develop an insider risk program and a process for mitigating incidents, both malicious and non-malicious, is before an incident occurs. When considering how to protect organizational assets, it is important to go back to foundational cybersecurity principles and identify the critical assets or services or business processes that, if attacked, would not allow your organization to achieve its mission as outlined by Brett Tucker in the post 10 Steps for Managing Risk: OCTAVE FORTE.
In determining critical assets (people, facilities, technology, information), it is important to ask
- What products or services do we provide?
- What information are we entrusted to protect?
- What do we do to provide these services or products?
- What assets do we use when performing these tasks?
- What are the security requirements of these assets?
- What is the value of these assets?
Key Elements of an Insider Threat Program
While information technology (IT) is key to an insider risk program, it is only one component. Too often organizations fall into the trap of considering their program complete once they purchase an insider risk management tool. Managing insider threat needs to be an ongoing, enterprise-wide effort that involves the IT department and others, such as human resources, general counsel, risk management, and physical security.
This enterprise-wide approach is needed because the ability to monitor user activity on a network does not always guarantee that monitoring is permitted or that it is not an invasion of privacy. The same standards and guidelines that require federal agencies and contractors to establish insider risk programs to monitor user activity on networks also requires privacy and civil liberty protection, which is an area where an organization’s general counsel plays a key role. A holistic approach to insider risk management involves enterprise-wide participation into requirements, monitoring, governance, and oversight of the program—someone watching the watchers. Oversight is a core principle in our best practices.
In September 2022, we published the seventh edition of our Common Sense Guide to Mitigating Insider Threats, which is based on research and analysis of more than 3,000 incidents. In addition to best practices for mitigating insider threats and resources for various stakeholders within an organization (i.e., management, human resources, legal counsel, physical security, IT, information security, data owners, and software), the guide outlines the critical elements of an insider risk program, shown in the figure below:
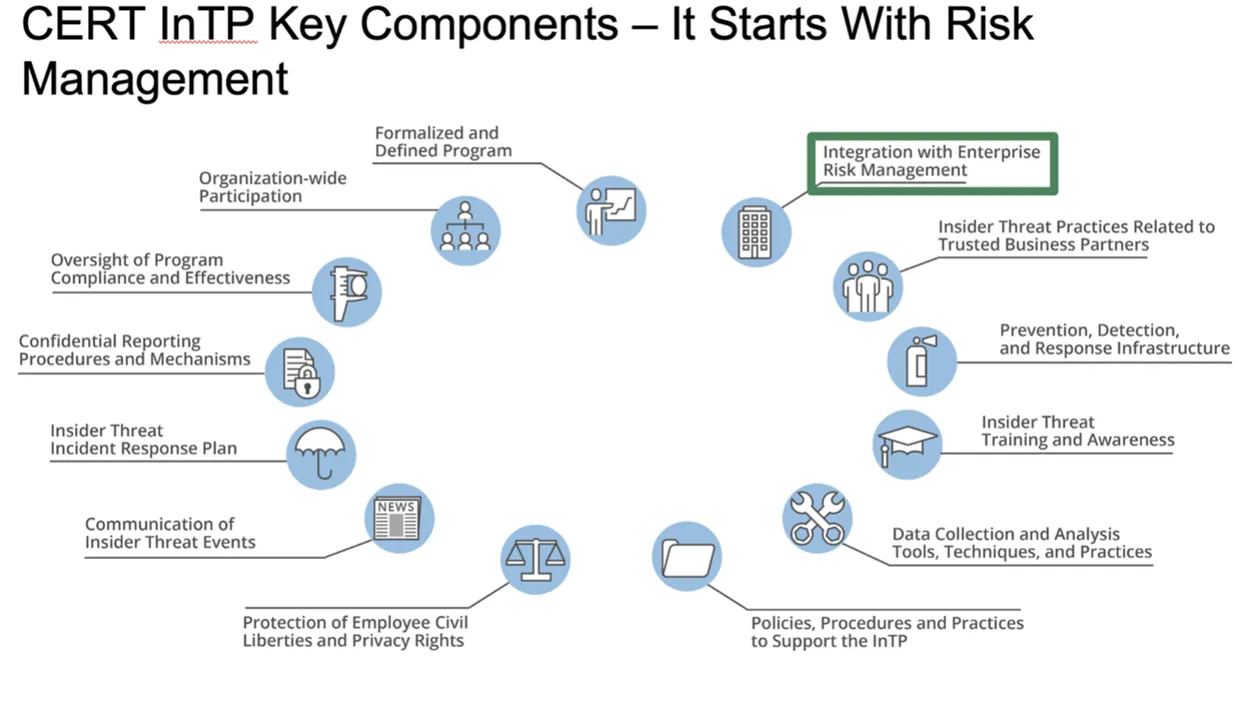
- Formalized and Defined Insider Risk Management Program (IRMP)—The program should include elements such as directives, authorities, a mission statement, leadership intent, governance, and a budget.
- Organization-Wide Participation—The program should have active participation from all organizational components that share or use program data. Senior leadership should provide visible support for the program, especially when the data the IRMP needs is in siloes (i.e., data lives exclusively in areas or departments such as human resources [HR], physical security, information technology [IT], or information security).
- Oversight of Program Compliance and Effectiveness—A governance structure, such as an IRMP working group or change control board, should help the IRMP program manager formulate standards and operating procedures for the IRMP and recommend changes to existing practices and procedures. Also, an executive council or steering committee should approve changes recommended by the working group/change control board. Oversight includes annual self-assessments and external entity assessments that evaluate the compliance and effectiveness of the IRMP.
- Confidential Reporting Procedures and Mechanisms—Not only do these mechanisms and procedures enable the reporting of suspicious activity, but when closely coordinated with the IRMP, they also ensure that legitimate whistleblowers are not inhibited or inappropriately monitored.
- Insider Threat Incident Response Plan—This plan must be more than just a referral process to outside investigators. It should detail how alerts and anomalies are identified, managed, and escalated, including timelines for every action and formal disposition procedures.
- Communication of Insider Threat Events—Event information should be appropriately shared with the correct organizational components, while maintaining workforce member confidentiality and privacy. This type of communication includes insider risk trends, patterns, and potential future events so that policies, procedures, training, etc., can be modified as appropriate.
- Protection of Workforce Member Civil Liberties and Privacy Rights—Legal counsel should review the IRMP's decisions and actions at all stages of program development, implementation, and operation.
- Integration with Enterprise Risk Management—The IRMP must ensure that all aspects of the organization’s risk management include insider threat considerations (not just outside attackers), and the organization should consider establishing a standalone component for insider risk management.
- Practices Related to Managing Trusted External Entities (TEEs)—These practices include agreements, contracts, and processes reviewed for insider threat prevention, detection, and response capabilities.
- Prevention, Detection, and Response Infrastructure—This infrastructure includes components, such as network defenses, host defenses, physical defenses, tools, and processes.
- Insider Threat Training and Awareness—This training encompasses three aspects of the organization: (1) insider threat awareness training for the organization’s entire workforce (e.g., employees, contractors, consultants), (2) training for IRMP personnel, and (3) role-based training for mission specialists who are likely to observe certain aspects of insider threat events (e.g., HR, Information Security, Counterintelligence, Management, Finance).
- Data Collection and Analysis Tools, Techniques, and Practices—These tools, techniques, and practices include user activity monitoring (UAM), data collection, and analysis portions of the program. Detailed documentation is required for all aspects of data collection, processing, storage, and sharing to ensure compliance with workforce member privacy and civil liberties.
- IRMP Policies, Procedures, and Practices—The IRMP must have formal documents that detail all aspects of the program, including its mission, scope of threats, directives, instructions, and standard operating procedures.
- Positive Incentives—Organizations should encourage positive workforce behavior rather than coerce it by leveraging positive-incentive-based organizational practices centered on increasing job engagement, perceived organizational support, and connectedness at work.
Insider Risk and AI
Machine learning (ML) and artificial intelligence (AI) have been on the forefront of insider threat anomaly detection for a number of years. Traditional security controls have involved tools that can monitor user activity, but only after receiving guidance from an analyst on specific behavioral anomalies to be on the lookout for. This arrangement limits the scope of monitoring to what is accessible within traditional controls and at an analyst’s discretion. Such an approach may flag activity if a user downloads 100 documents in a day, but what if an insider does one document a day over 100 days?
AI and ML can delve deeper to determine potentially worrisome patterns of activity by an individual by taking into account statistical and human anomalies.
A new class of insider threat tools, which rely on user entity and behavior analytics (UEBA), widens the aperture beyond technical anomalies involving an employee’s computer use to incorporate different data sets. If an employee is leaving an organization, for example, the tools would pull data from the HR management system. These tools also account for activity in an organization’s physical security systems, including badging records or camera systems.
UEBA tools are using AI first and foremost by incorporating different data from across an organization and informing analysts of anomalies without analysts telling the tools what should be reported.
Most employees do not join an organization intending to do harm, and, as we referenced earlier, most insider incidents that do occur are unintentional. Regardless of intent, all insider incidents involve a misuse of authorized access to an organization’s critical assets, and a large number of the incidents are unintentional. We in the CERT Division of the SEI are working to understand the underlying reasons behind stressors and concerning behaviors to detect insider threats early and offer employees assistance before they commit a harmful act.
Additional Resources
Common Sense Guide to Mitigating Insider Threats, Seventh Edition
Learn more about OCTAVE FORTE, OCTAVE for the Enterprise Model.
View our collection of publication in the SEI Digital Library on the CERT Resilience Management Model (CERT-RMM), the foundation for a process improvement approach to operational resilience management.
More By The Authors
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


