Technology Trends in Data Exfiltration
PUBLISHED IN
Insider ThreatOne of our goals at the CERT National Insider Threat Center (NITC) is to monitor the shifting landscape of insider threat to identify tools and techniques insiders may use to harm to their organization. Our expanding repository of insider incidents shows that the tools and techniques insiders use to exploit vulnerabilities change rapidly as new technologies emerge and organizations evolve how they protect their assets. This blog post will look at the emergence of technologies and the frequency with which they have been used by insiders over the last 20 years.
Two Technologies
I'll take a look at two technologies that insiders might use to remove data from a company's computer systems without authorization: email and removable media.
Let's look at the use of these technologies by insiders over time and compare their usage to when the technologies became generally popular. By popular, I mean readily available for consumer use to access organizational assets. I don't mean technology such as quantum computers, which are popular in media and entertainment but are mostly not available to the consumer market. It's a little hard to pin down when something becomes popular, but I'll use the following for the analysis:
- Email became popular in 2001, following an explosion of internet users driven by packaged internet and email services such as AOL and CompuServe.
- USBs became popular in 2003, after Intel started putting USB technology in their laptops the year before.
In these incidents from our CERT Insider Threat Incident Corpus, an insider used one or more email services to move data off of authorized computer systems. The insider may have used corporate email, personal email (Gmail, Hotmail, etc.) or a combination. While there are many ways insiders can use email to cause harm, one insider misused it to inform competitors about contract bids:
- A contracts manager colluded with two outsiders employed by two competitor organizations to provide confidential information over the phone and through email on bids for federal contracts. The insider's actions had a confirmed impact of more than $200,000 but a potential impact of $2.5 million.
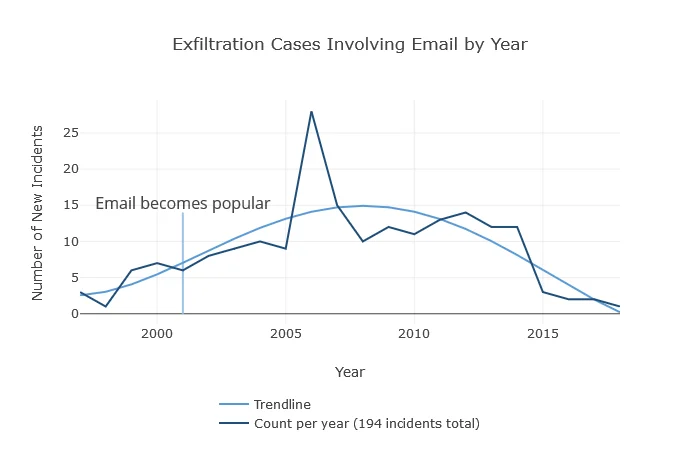
Figure 1: Data Exfiltration via Email
Removable Media
In these incidents, an insider used a USB drive or other removable media to move data off of an authorized storage location. These incidents include any external storage connected over USB, not just flash memory devices. One insider used removable media to steal personally identifiable information (PII) that was later used in identity theft:
- The insider was a government employee who stole PII through printed documents and removable media. The insider then resigned and used that PII to commit identity theft. Later, the victim organization opened an investigation into the insider, leading to law enforcement searching the insider's residence and finding the flash drive and confidential documents.
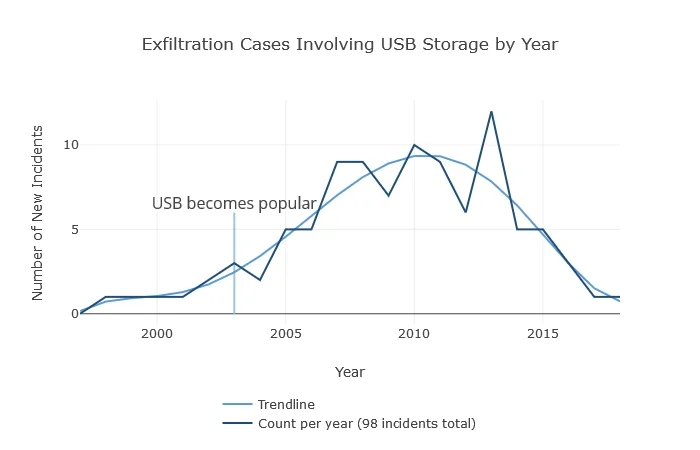
Figure 2: Data Exfiltration via Removable Media
Trend in Technology Use by Insiders
These graphs seem to show a trend: once a technology becomes commercially available, insiders start using it to carry out their attacks. We can illustrate this notational model as the figure below:
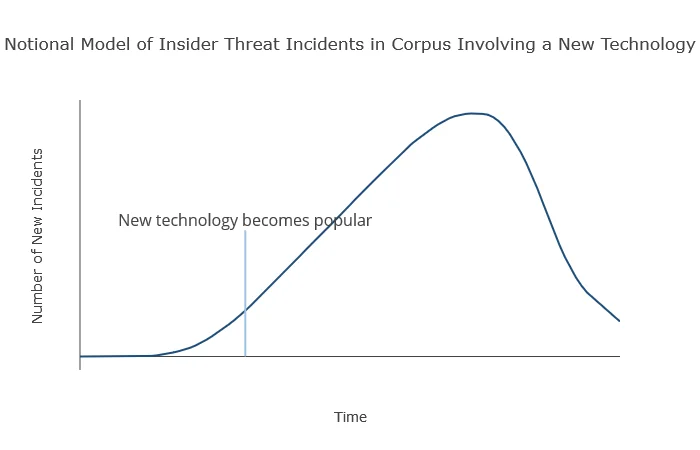
Figure 3: Notional Model of Insider Use of New Technology
Figure 1 shows that insiders were using email to exfiltrate data even before email's surge in popularity in 2001. To carry out their surreptitious activities, the early adopters leveraged a technology whose risks were not well planned for or mitigated.
Insider threat programs should carry forward this lesson on planning for early adopters of technology. Consider today's newer and more widespread technologies, like the Internet of Things (IoT). Across the board, personal and business consumers are seeing new releases of conventional products feature additional sensors for IoT integration or smart or predictive abilities for artificial intelligence learning. Wearables, having made waves for years in the watch industry, have started to break out into other clothing and accessory markets, allowing tech-makers to add their own IoT features to apparel. Now, more than ever, insiders of all types are able to leverage the connectivity and data-monitoring capabilities of IoT, whether by hacking the office's unsuspecting "smart" coffee pot or by wearing some "smart" apparel to the office. The threat landscape is significantly expanding.
What does this mean for insider threat programs? Now is the time, if you haven't begun already, to plan for and strategize how to mitigate threats posed by IoT technologies. Insiders will, and probably have, used IoT sensors to exfiltrate, sabotage, or surveil victim organizations.
Keeping Up
It seems new technologies are churned out every day. In the face of a fast-moving industry, it's important to keep up to date with what risks your organization might face from insiders, particularly those insiders who leverage the latest tech to advance their agenda. (Organizations should apply Best Practice 17, Institutionalize System Change Controls from the Common Sense Guide to Mitigating Insider Threats, Sixth Edition.)
Though our current dataset is limited to incidents that resulted in court convictions in the legal system, the data is not entirely reflective of the current legal or regulatory environment. The trend lines shown in our figures may change, based on future court decisions. Nevertheless, this data does give us some interesting historical context by which to hypothesize that if a novel technology exists, savvy insiders may use it to carry out their malicious activities.
This post has talked about what kinds of tools insiders may use, but not how to prevent or detect their use. For more on preventing and mitigating these kinds of attacks, check out our Common Sense Guide to Mitigating Insider Threats, Sixth Edition.
More By The Author
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
