Supporting the Android Ecosystem
PUBLISHED IN
CERT/CC VulnerabilitiesA few months ago, a widely-publicized set of vulnerabilities called StageFright hit the Android ecosystem. While Google fixed the vulnerabilities in what appears to be a reasonable amount of time, the deployment of those fixes to end-user devices is another story. Many Android devices have a lengthy supply chain, which can make the process of deploying OS updates a slow and uncertain process. In this blog post, I investigate the supply chain of the Android platform and show how it can affect the security of the OS.
Android and iPhone Update History
Approximately four years ago, Michael DeGusta created a blog post called Android Orphans: Visualizing a Sad History of Support. This post contains an interesting graphic that helps to visualize the state of various Android phones as well as Apple iPhone devices:
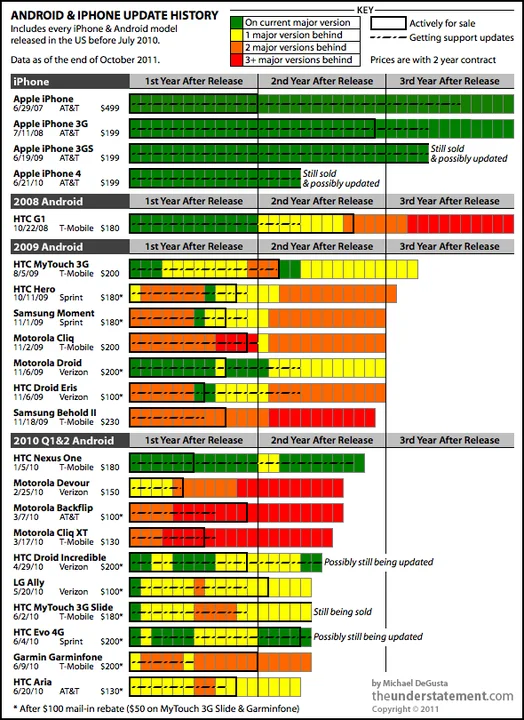
Here you can see that not only are Android devices appearing to lose support shortly after their release, but some Android devices come with old versions of the Android OS the moment they are purchased.
About two years later, Fidlee posted an updated version of the same type of information in the post Android Support vs iOS Support. The results are remarkably similar:
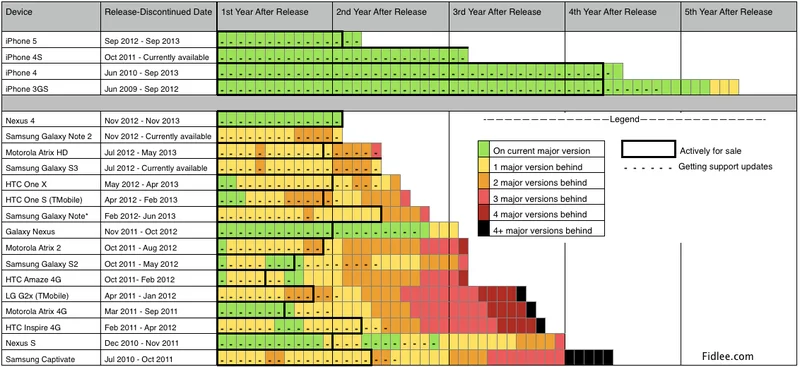
Here you can see the same sort of pattern. However, one pattern is more clear with this set of data. The Nexus phones seem to get more consistent support than any other Android phone. To understand why this is the case, it's important to consider the supply chain involved with most nexus phones.
Smartphone Supply Chain
Here are the supply chain steps for some different OS scenarios.
Apple iOS
First, let's consider the supply chain of an Apple iOS phone:
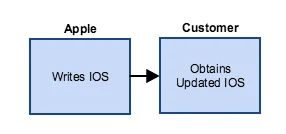
- Apple releases the iOS OS for iPhone devices.
- The customer is notified that the update can be installed.
Nexus Android
Now let's consider the supply chain of a Nexus Android phone:
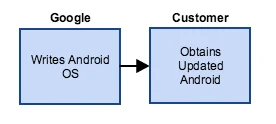
- Google releases the Android OS for Nexus phones.
- The customer can pick up a factory image from Google or the customer can wait for an over-the-air (OTA) update to upgrade the OS from his or her phone. (The version of the OS on the customer's phone is the Android OS as Google has intended it.)
Unlocked Android
An unlocked Android phone is one that is not provided by a specific wireless carrier, and therefore does not have any provider-specific customizations to the Android platform. The supply chain of an unlocked Android phone has one more step:
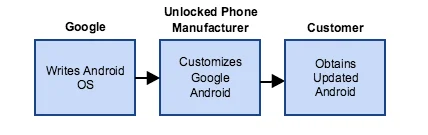
- Google writes the core Android OS.
- The phone manufacturers take the stock Android OS and customize it as they see fit.
- This customized version of Android makes it to the consumer's phone.
Other Android
Finally, let's consider the supply chain of most other Android phones:
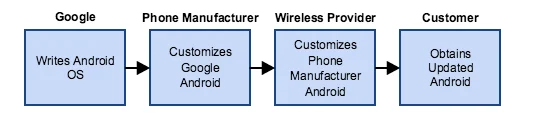
- Google writes the core Android OS.
- Phone manufacturers take the stock Android OS and customize it as they see fit.
- The phone's wireless provider customizes the phone manufacturer's already-customized version of Android.
- Finally, this double-customized version of Android makes it to the consumer's phone.
Keep in mind that the flow can stop at any point. Just because Google provides a new version of Android does not mean that the phone manufacturer will apply it to one of its devices. Every step of the supply chain adds a delay to the distribution of the OS. And just because a phone manufacturer produces an updated version of the OS for one of their phones does not necessarily mean that the wireless provider will choose to customize and release it to its customers. Phone manufacturers and wireless providers have little incentive to develop, customize, and test updates for older phones.
Security Updates
Having the latest and greatest OS is usually nice because it adds more functionality to the phone. However, it's important to consider the security improvements associated with OS updates. For example, depending on which Android version a customer is using, it may provide various levels of the ASLR exploit mitigation. Starting with Android Jelly Bean (4.1), full ASLR is provided. In other words, the newer the Android OS is, the more resistant it is to exploitation as is the case for most operating systems.
Aside from the increased security of newer operating systems, which may include improved exploit mitigations, as well as silently-fixed bugs, there is the situation of specific vulnerabilities that are disclosed. For example, consider again the recent vulnerabilities in the Android StageFright library. Until customers with vulnerable versions of Android receive OS updates, they are at risk. How long will that window of vulnerability exposure last, though?
The University of Cambridge created a page called AndroidVulnerabilities.org, which summarizes the population of Android devices that are vulnerable to a set of known vulnerabilities, including StageFright. This figure illustrates the estimation of vulnerable Android devices in the wild:
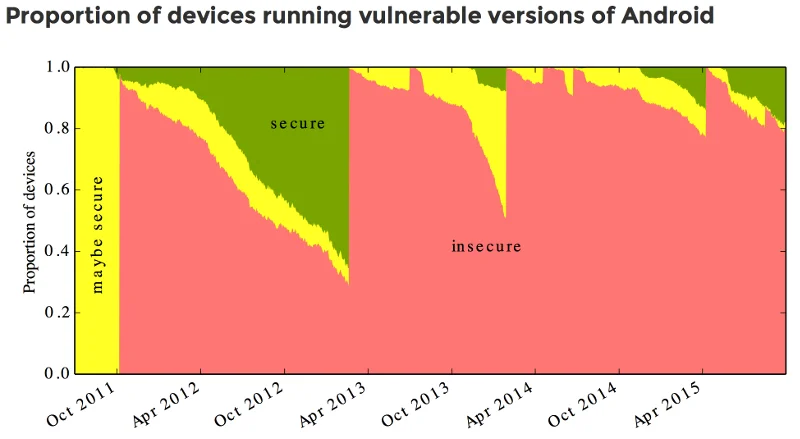
These numbers were obtained through the use of the Android Device Analyzer application, which reported statistics to the University of Cambridge for this study. The conclusion of the study is that 87% of Android devices are vulnerable. However, there is reason to suspect the above chart might be optimistic when extrapolated to the general population of Android devices.
Because the study required users to install the Device Analyzer app, it is likely that the participants were already interested in the security of their devices. If that is true, the data collected from the 21,713 Android devices in this study may under count the number of vulnerable devices.
Conclusions
While they are very capable computers, smartphones such as iPhones and Android phones do not see the same amount of support that desktop operating systems do. For example, Microsoft supported Windows XP for 12 years. With smartphones, the situation is quite different. Apple recently released iOS 9 for the iPhone 4s, a device that was first sold just over four years ago.
Android phones do not seem to receive the same length of support, though. Only after the StageFright vulnerabilities were disclosed did Google commit to supporting new Nexus devices for two years beyond the phone's initial release and security updates for three years beyond the phone's initial release, or 18 months beyond the last sale of the device from the Google Store, whichever is longer.
For older Nexus phones, that's not the case. For example, support for the Galaxy Nexus was abandoned less than two years after it was released. Some non-Nexus Android phones don't see any updates at all beyond their initial release.
The longer the supply chain is for an OS to get deployed to a customer, the longer the delay is. There is also more uncertainty about whether a device will receive updates at all. Non-Nexus Android phones fit in this category.
It is also important to consider non-phone Android devices. Without the same sort of support mechanisms that are in place for smartphones, it is easy to imagine that your Android-enabled refrigerator or automobile perhaps may see even less support by way of OS updates than your phone might.
Recommendations
If smartphone security is a concern, follow these guidelines:
- When selecting a smartphone, consider the track record of the phone manufacturer's release of security updates.
- If you are purchasing an Android phone from a wireless provider, consider the track record of the wireless provider releasing security updates as well.
- If you are purchasing an Android phone, consider a Nexus device since it has a better chance of continued support versus other Android devices. If you are not choosing a Nexus Android device, then an unlocked phone is the next best bet for minimizing the supply chain.
More By The Author
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
