Navigating the Insider Threat Tool Landscape
PUBLISHED IN
Insider ThreatMitigating insider threats is a multifaceted challenge that involves the collection and analysis of data to identify threat posed by many different employee types (such as full-time, part-time, or contractors) with authorized access to assets such as people, information, technology, and facilities. The landscape of software and tools designed to aid in this process is almost as wide and varied as the problem itself, which leaves organizations with the challenge of understanding not only the complexities of insider threats, but also the wide array of tools and techniques that can assist with threat mitigation. This post explores some of the recommended tool features and functionality available through use of a combination of tools, as well as a proposed process to implement and operate controls at an organization.
There are various features and functions to prevent, detect, deter, and respond to insider threats. The following list is not exhaustive, but provides several examples that should be considered as part of a robust and comprehensive insider threat prevention platform.
- Preserve forensic artifacts in the event of litigation
- Audit network and host-based activity
- Monitor data and prevent it from leaving authorized locations
- Correlate and resolve user and system entity activity across various data sources
- Perform analysis on data being gathered in the form of rule-based alerting, statistical anomaly detection or both, and prioritize those alerts
- Generate data visualizations to aid in analysis
- Manage and track the status and resolutions of cases/incidents
- Analyze text-based data sources for sentiment and affects
- Mask or anonymize sensitive information that is presented to analysts
The number of features to consider, however, does not necessarily correspond to the number of different tools required, nor does it mean that one or two tools can or should provide all of the desired functionality. There is a great deal of overlap, which may provide a defense in depth strategy but should not require you to purchase multiple tools, in several critical functional areas that can be accomplished by some combination of Data Loss Prevention (DLP), Enterprise Asset Management (EAM), Security Incident and Event Management (SIEM), User Activity Monitoring (UAM), and User (and Entity) Behavior Analytics (UBA/UEBA) tools. Given this overlap, it is important to understand the capabilities offered by existing hardware and software before assuming that procurement is the only method to introduce new functionality. Despite many claims, there is no single tool that will solve a problem as complex as insider threat. Instead of taking a tool-centric approach, begin by enumerating the desired functions to mitigate the threat and work from there. Depending on the industry or government sector, an organization may be subject to different regulations or mandates for specific types of controls. It is crucial to understand the actual requirements that must be fulfilled to avoid over-buying a particular solution that contains unnecessary functionality. However, in the absence of outside requirements, start by adhering to the best practices outlined in the Common Sense Guide to Mitigating Insider Threats.
Figure 1 illustrates a potential iterative process for implementing and operating insider threat controls.
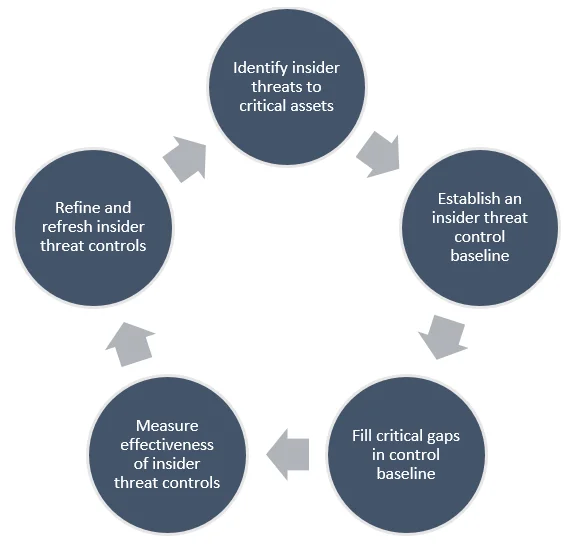
Figure 1: Proposed Insider Threat Control Implementation and Operation
The first step at the top of the diagram is to identify your critical assets and the threats to those assets in order to help prioritize and focus the control efforts. This is a vital first step, as it helps to temper the expectation that every single system and piece of data must be secured to the highest degree. As the adage goes, if everything is critical, then nothing is critical. Start by involving the right people in the decision-making process, such as an existing risk management group, process owners, and high-level management. Identify areas of work including business process and critical services that are paramount to achieve the organization's mission and survival and focus the remaining steps of the implementation and operation process starting with those areas.
Step two is to implement a baseline set of security controls. It is recommended to start with the tools and capabilities that already exist within the organization. Again, identify any governing standards or regulations or begin by referencing accepted standards, such as the Insider Threat specific controls included in NIST SP 800-53 Revision 4 and above. For example, one might leverage an existing log collection mechanism from host operating systems with a particular focus on auditing user activity.
Once the capabilities of the current toolset have been fully implemented, identify and fill any gaps with new (or modified) security controls. For instance, if there are no controls to prevent or log data movement across network or storage boundaries, then that gap might be filled by a DLP component.
The next step is to measure the effectiveness of the implemented controls. This measurement is not purely the number of actors that have been caught (which may not be greater than zero due to the low base rate of occurrence for insider incidents). However, one goal of this phase, in the absence of a high frequency of true positives, is to reduce false positives and false negatives. This step also includes measuring the control implementation and the effectiveness of the surrounding procedures, such as how long it takes to complete case investigations or how long it takes to engage or receive information from other parts of the organization. The final aspect of this step is to measure the coverage of controls and maximize the percent of machines, users, or data repositories that are actively monitored.
Given these data and measurements, the final step to closing an iteration of the loop is to refine the controls and alerts in order to maximize effectiveness and maintain capabilities. The iterative and continuous nature of this approach is especially important when you are faced with things like changing organizational priorities, missions, personnel, technologies, and risks.
For more information, including a few potential software solutions for smaller organizations or new Insider Threat programs, see the Navigating the Insider Threat Tool Landscape: Low Cost Technical Solutions to Jump Start an Insider Threat Programi presentation at the 2018 Workshop on Research for Insider Threats as part of the 39th IEEE Symposium on Security and Privacy.
Please send questions, comments, or feedback to insider-threat-feedback@cert.org.
i Spooner, D., Costa, D., Silowash, G. & Albrethsen, M. Navigating the Insider Threat Tool Landscape: Low Cast Technical Solutions to Jump Start an Insider Threat Program. Software Engineering Institute, Carnegie Mellon University. To be published.
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed