Moving Personal Data at Work
PUBLISHED IN
Insider ThreatMany organizations allow limited personal use of organizational equipment. To move personal data to or from the organization's devices and network, employees typically use email, removable media, or cloud storage--the same channels a malicious insider would use for data exfiltration. This post explores a new way, based on cross-domain solutions, for employees to safely transfer personal data between an organization's network and their own systems.
Dtex Systems' 2017 Insider Threat Intelligence Report found that 56% of surveyed organizations faced potential data theft from new and departing employees. During the first two weeks of employment, new employees imported large amounts of data; during the final two weeks of employment, departing employees had unusual file aggregations.
A personal data channel provides a legitimate way for non-malicious employees to transfer personal data to and from the organization's network. For example, a user who downloads recipes on a work computer might want to move these recipes to a home system for use. With this approach, the user would submit a request to move the personal data outside the organization's network. The data would be examined and, if acceptable, moved to a separate, permission-controlled directory. The user would then copy the data in this directory to storage outside the network.
This approach makes malicious or unintentional exfiltration of data by traditional channels easier to spot. It also provides intelligence that could later be used to detect malicious activity.
How Personal Data Channels Work
Any approach to moving personal data needs to prioritize confidentiality, data integrity, and availability of the organization's critical assets. Cross domain solutions (CDS) provide a model of information assurance (IA) when transferring data across different security domains. To move data from the secured side to the unsecured side in a CDS, the user must provide the location of the files to IA personnel and affirm that the data is unclassified. The IA team verifies this information, moves the data, and informs the user where to access the data.
Now, let's build a model of personal data movement. The inside of the network is the secured side, where the user's personal data resides. The outside is the unsecured side--the Internet.
Based on the CDS model, events flow through the system as shown in Figure 1.
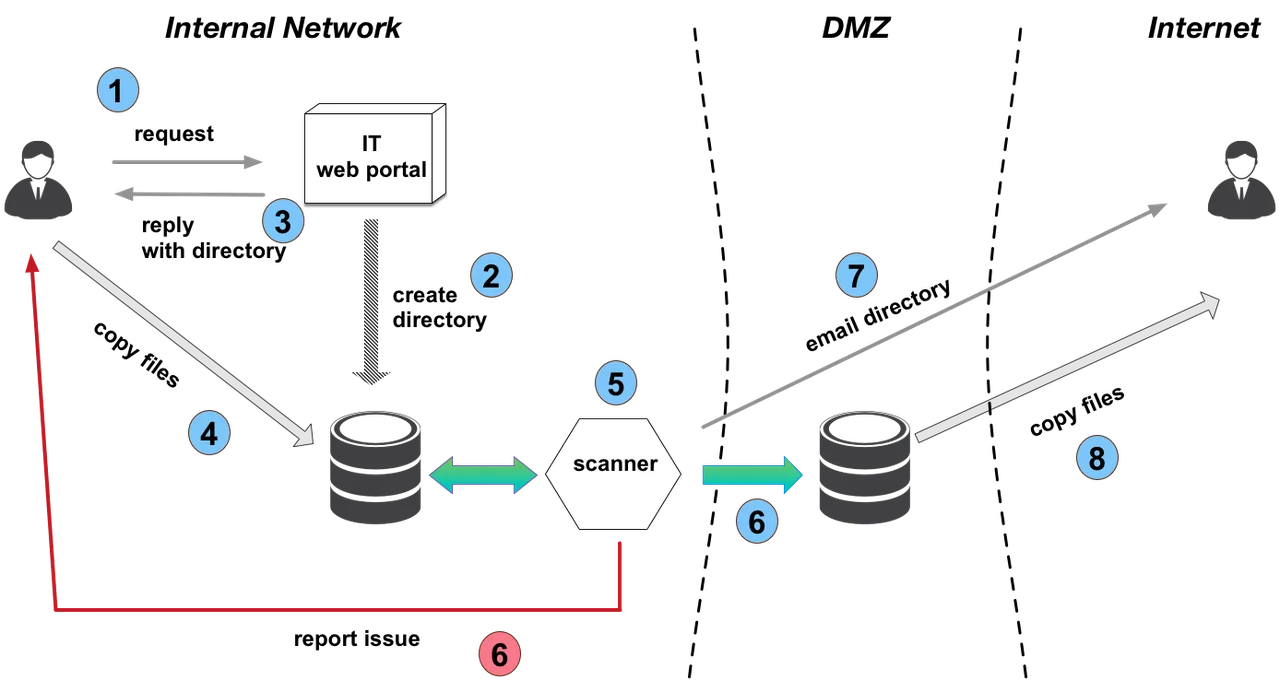
Figure 1: Personal data movement between an internal network and the Internet
- A user submits a request to move personal data files.
- The IT department processes the request and creates a directory for the user's personal data.
- If the volume of requests is low, IT staff could manually process requests.
- If the volume of requests is high, the IT department could set up an automated, self-service web portal to process requests. - The IT department replies to the user, indicating the directories where the user should put the personal files. The reply could also remind the user of the acceptable use policy and which files are permitted to be moved (e.g., size limitations on files, no password protected files). Again, this could be done manually or through an automated web portal.
- The user copies the personal data into the newly-created, user-specific directory.
- Once the system detects the user's personal files, it scans them (for example, with a data loss prevention (DLP) system). Additionally, the files could be archived for a given period of time for forensic purposes.
- If the files pass the scan, the system moves them to a location that is accessible from outside the enterprise network (the de-militarized zone, or DMZ), and the process moves to step 7. If the files do not pass the scan, the system reports the error back to the user. The report could also tell the user how to fix common errors and specify a contact person for disagreements. Errors should be logged and files quarantined for future use or resolution.
- The system tells the user the location of the personal files in the DMZ. This notification might be delivered as an email to the user's personal email address, if the user has provided one. If file size permits, the data could be emailed to the user's personal address as an attachment. The user's personal email address could also be used in later insider threat investigations, if such processes comply with legal and civil liberty policies.
- From outside the organization's network, the user copies the files to a personal account.
Transferring Personal Data into an Organization
This approach shows how data can move effectively and securely from inside an organization to the outside. A similar approach could be used to move data in the reverse direction. For example, a user might find a work-related article while browsing on a home system and wish to send it to a work system for future reference. In this direction, the scanner should look for malware and search for keywords that could identify documents from a competitor (to avoid insiders from other companies trying to infiltrate information into your company).
Benefits and Drawbacks of Personal Data Channels
Personal data channels help organizations manage the flow of non-malicious personal information into and out of networks. Removing legitimate, personal data from potential exfiltration paths reduces false positive indicators of malicious activity. Personal email addresses can be used in insider threat investigations, if allowable. The names of files rejected by the scanner can be used in the DLP and user activity monitoring (UAM) tools as potential alert triggers.
However, this approach is not without drawbacks. Malicious insiders could hide organizational data within personal data (steganography) and use the organization's own security channel against itself. To combat this, the approval process for personal data channels could incorporate behavioral analysis and a check on the size and number of files being sent. Any requests that surpass a combined threshold for these two mechanisms could trigger an alert.
In addition, if this approach is not properly architected, it could be used as a vector for a denial-of-service attack that is automated to fill disks and cause excessive scanning. To mitigate this risk, the system should be monitored and files removed based on a predetermined timeout.
Conclusion
Using personal data channels to transfer files has benefits for both employees and organizations. Employees have a legitimate path to migrate their personal data. Organizations have better visibility into data flowing into and out of their networks, which facilitates looking for actual insider threats.
More By The Author
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
