Maturing Your Insider Threat Program into an Insider Risk Management Program
PUBLISHED IN
Insider ThreatHaving trouble clearly stating the scope of your insider threat program? Struggling with measuring the program's effectiveness? Failing to provide actionable intelligence to the program stakeholders? Lacking consensus regarding your organization's current security posture against insider threats? These are signs that your insider threat program may not be properly integrated with a risk management program within your organization. In this blog post, we will discuss the benefits of grounding insider threat program operations in the principles of risk management, and we will present strategies for successfully maturing your insider threat program into an insider risk management program.
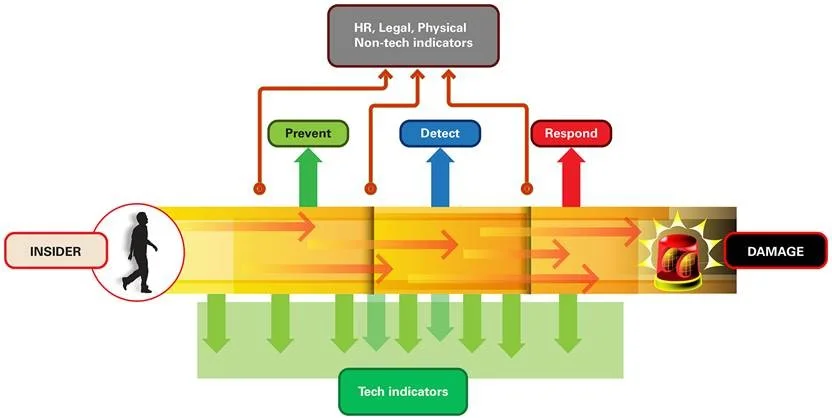
The Real Goal for an Insider Threat Program
Fledgling insider threat programs typically start with a focus on reactive activities: identification of damaging events and strategies for response and recovery. As organizations mature their insider threat programs, they tend to add proactive activities: detection of concerning behaviors and activities that precede a damaging event and response options focused on reducing the likelihood that individuals exhibiting concerning behaviors will go on to harm the organization.
Based on nearly 20 years of research into insider incidents and insider threat program building, we believe the goal for an insider threat program is to leverage data, controls, authorities, and expertise from across the organization to better prevent, detect, and respond to insider threats to the organization's critical assets, both reactively and proactively. To put it another way, an insider threat program should allow the organization to better manage risks to its assets posed by insiders.
Because proactive insider threat program activities focus on detecting and responding to pre-damage conditions, a key to success is the ability to identify the likelihood that damage will be done by an insider, given their personal predispositions, stressors, and concerning behaviors. Not all damaging events are created equal, so another key is the ability to identify the impact of a damaging event should it occur. This ability involves an understanding of what assets the organization is trying to protect from harm from insiders. Identifying the impact and likelihood of insider threats to specific types of assets--this is where risk management can help!
A Risk Management Approach to Insider Threat Program Building
Risk management frameworks, such as the SEI's Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE®) FORTE method, provide standardized processes and procedures that help organizations more effectively manage risk. Most risk management frameworks include steps for identifying the critical assets an organization is trying to protect, identifying and analyzing risks to those critical assets, and prioritizing and implementing response plans. Early engagement of insider threat programs with a robust enterprise risk management program can ensure that
- the insider threat program scope can be clearly defined ("the organization's insider threat program is designed to protect these assets from these threats posed by insiders")
- the insider threat program scope operates under the appropriate governance structure and with an accurate understanding of the organization's risk appetite
- insider risks are managed consistently with all other risks the organization manages at the enterprise level
The relationship between insider threat programs and enterprise risk management programs is mutually beneficial: insider threat programs often provide insight into threats to an organization's critical assets that the enterprise risk management team may have not considered. Organizations should consider using use risk and vulnerability assessment methodologies such as OCTAVE Allegro and the SEI's Insider Threat Vulnerability Assessment to streamline and optimize the process of assessing risks to their critical assets posed by insiders. Using a process like OCTAVE Allegro to establish security requirements for the assets to be protected by the insider threat program also provides a set of goals and metrics the program can use to measure its own effectiveness.
For insider threat programs in organizations without robust enterprise risk management programs, we recommend that the organization build the insider threat program using a risk management framework as a backbone. Because an insider threat program requires enterprise-wide participation, building an enterprise risk management function with insider risk as the first type of risk being managed can be an effective way to get started.
Learn More
For more recommendations on how to incorporate insider threats into risk assessments, see best practice 6, "Consider threats from insiders and business partners in enterprise-wide risk assessments," from the CERT Common Sense Guide to Mitigating Insider Threats, Sixth Edition. For more on how to mature your insider threat program into an insider risk management program, see our presentation from the 2019 RSA Conference, "Finding the Right Answers - Facilitating Insider Threat Analysis using OCTAVE FORTE."
More By The Author
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
