Improving Cybersecurity Governance via CSF Activity Clusters
PUBLISHED IN
Insider ThreatThe National Institute for Science and Technology (NIST) recently released version 1.1 of its Cybersecurity Framework (CSF). Organizations around the world--including the federal civilian government, by mandate--use the CSF to guide key cybersecurity activities. However, the framework's 108 subcategories can feel daunting. This blog post describes the Software Engineering Institute's recent efforts to group the 108 subcategories into 15 clusters of related activities, making the CSF more approachable for typical organizations. The post also gives example scenarios of how organizations might use the CSF Activity Clusters to facilitate more effective cybersecurity decision making.
Cybersecurity Governance and Org Charts
Setting up an organizational structure specifically for optimal cybersecurity governance and operations can be highly challenging. The level of cybersecurity success or failure is often as dependent on culture, leadership, experience, and personalities as it is on adherence to a line-and-box organization chart structure. Still, the structure is necessary, and spreading responsibility for 108 separate cybersecurity activities across that structure isn't straightforward.
Decomposing the overall cybersecurity mission into a more standard set of components and focusing on the dependent relationships among those components can yield valuable insights that may help to inform organizational structure and improve cybersecurity effectiveness. We formed our standard set of cybersecurity components from the CSF because of its widespread use and scope of cybersecurity activities.
Methodology
Subcategory Dependencies
The underlying methodology used for the CSF relationship mappings and clustering is based on two complementary approaches. The first involves comparing each of the 108 CSF subcategories against one another (see Figure 1). We manually evaluated each of the 11,556 subcategory pairs based on dependency, with four possible outcomes: x is dependent on y, vice versa, they are codependent, or there is no dependency. By "dependency," we mean either a subcategory chronologically preceding another or feeding data to another. For example, ID.GV-2 is dependent on ID.AM-6 because ID.AM-6, "cybersecurity roles and responsibilities are established," must precede ID.GV-2, "cybersecurity roles and responsibilities are coordinated and aligned with internal roles and external partners."
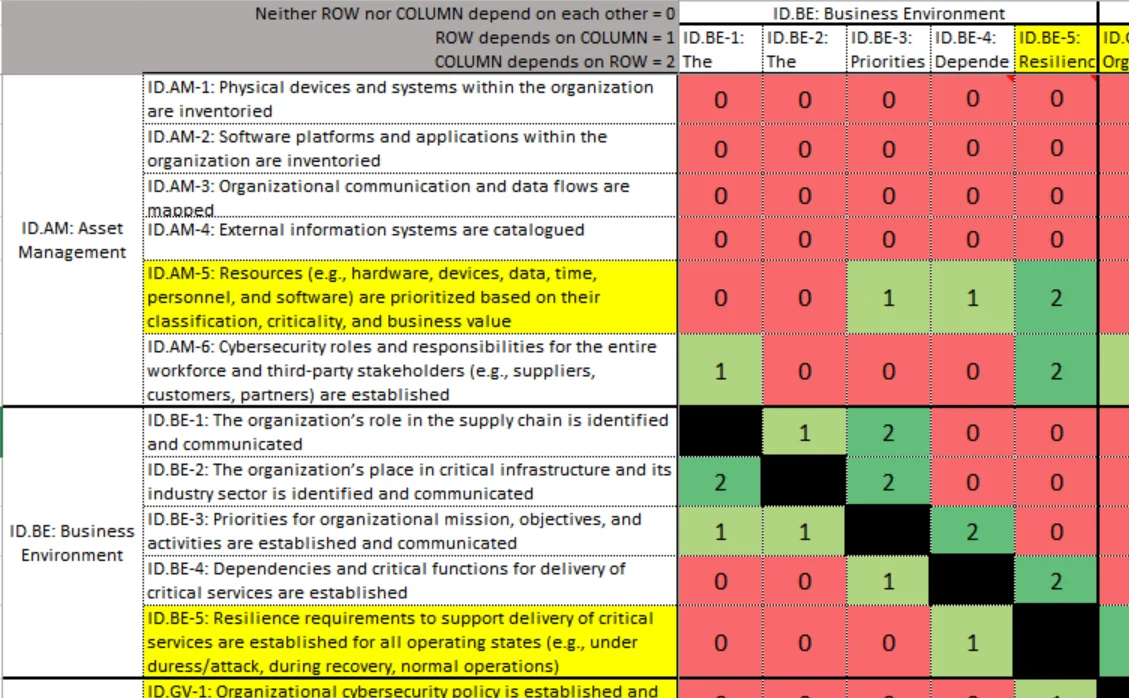
Figure 1. CSF subcategory relationship matrix
We then graphed the matrix of these dependency relationships, creating a visual representation of the connectedness of the subcategories. This approach is extremely useful for identifying functional dependencies and highlighting key interfaces between subcategories and groups of subcategories. However, it does not explicitly identify how subcategories and groups of subcategories are related from an organizational perspective, in terms of skillsets required, level of organizational responsibility, and functional similarity.
Organizational Similarity
Our second approach builds on the first by analyzing the organizational characteristics of the newly clustered CSF subcategories. My colleagues and I used a consensus-building discussion to refine the subcategory groupings, based on three questions:
- To what extent do the outcomes described by the subcategories require similar personnel with similar skillsets?
- To what extent do they require similar organizational authorities?
- To what extent are they described by the subcategories and "functionally" similar?
The consensus answers to these questions created a secondary graph of the subcategories, which was then overlaid onto the dependency graph. The resulting integrated viewpoint incorporates both approaches--dependency and organizational similarity--into a model that could provide a baseline for addressing governance tasks, such as assigning functions to organizations and ensuring key dependency interfaces are managed. The graph also indicates relationships between the clusters as well as relationships between the subcategories within each cluster.
The 15 CSF Activity Clusters
We're defining a cluster as a grouping of similar cybersecurity processes that support a common cybersecurity administrative or operational activity. We grouped the NIST CSF subcategories into the following cybersecurity Activity Clusters:
| 1. Environment and Mission | Activities that define the key purpose(s) of the enterprise and ensure that mission is properly communicated to the entire organization |
|---|---|
| 2. Risk Program Definition | Risk appetite, assessment, and mitigation approaches to ensure both alignment with the organization's mission and cost-effective management of attendant risks |
| 3. Cybersecurity Governance | Activities that ensure proper leadership, culture, sponsorship, and cybersecurity policies and procedures are in place |
| 4. Awareness and Training | Awareness and skills necessary to achieve the desired cybersecurity outcomes |
| 5. Asset Management | Activities that identify, document, and manage the organization's assets |
| 6. External Dependencies Management | Activities necessary to effectively manage supply chain risk (e.g., contractual vehicles, third-party assessment) |
| 7. Data Management | Engineering data access to maintain appropriate confidentiality, integrity, and availability |
| 8. System Management | Technical activities, policies, and procedures to ensure systems are properly developed, configured, and managed throughout their lifecycle |
| 9. Network Management | Engineering to ensure protection of the confidentiality, integrity, and availability of data in transit |
| 10. Access Management | Activities to manage access, both physical and logical, to organizational assets |
| 11. Vulnerability Management | Proper identification and management of cybersecurity vulnerabilities within the organization |
| 12. Threat Information Management | Proper identification and understanding of threats to assets |
| 13. Event and Incident Analysis | Activities to ensure the appropriate level of response commensurate with the risk represented by events and incidents |
| 14. Monitoring and Detection | Proper event monitoring and analysis to maintain full-network cybersecurity situational awareness |
| 15. Incident Response and Recovery | Activities to ensure response to incidents is commensurate with a defined organizational risk program as well as relevant policies and procedures |
Use Cases
Here are two examples of how the CSF Activity Clusters could inform organizational cybersecurity governance effectiveness.
Example 1: Organizational Tension
By overlaying the CSF Activity Clusters onto its organizational chart, an enterprise could see how specific cybersecurity activities and groups are distributed within the organization. The mapping could show possible areas of decision-making tension. For example, if responsibilities for one cluster's subcategories are distributed across three or four individuals, management can better understand the challenges facing the individuals in executing those subcategories soundly and consistently.
Example 2: Resource Allocation
By introducing and mapping other metadata (e.g., budget, headcount) against the CSF Activity Clusters and their inter- and intra-cluster relationships, an organization could better identify its distribution of governance-related resources. Such a mapping could inform a realignment of resources to help ensure greater likelihood of effective CSF outcomes.
Conclusion
The CSF Activity Cluster concept allows organizations to look beyond the standard line-and-box organization charts to understand and address their governance challenges. It enables a resource perspective that can help organizations identify where and how to address those challenges and, ultimately, improve cybersecurity outcomes. Going forward, we are looking at ways to visualize the clusters and their relationships, as well as other possible applications of the concept.
Please let us know what you think! Write to us at info@sei.cmu.edu.
The author would like to acknowledge the contributions of Doug Gardner, Will Cunha, Carl Grant, Matt Trevors, and Mike Wigal to this effort.
More By The Author
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
