Formalized Insider Threat Program (Part 2 of 20: CERT Best Practices to Mitigate Insider Threats Series)
PUBLISHED IN
Insider ThreatThe second practice described in the newly released edition of the Common Sense Guide to Mitigating Insider Threats is Practice 2: Develop a formalized insider threat program. In this post, I discuss why this practice is so important to preventing and managing insider threats.
Effective insider threat mitigation requires coordination and collaboration among many different parts of an organization. Human resources, legal, physical security, information technology, enterprise risk management, incident response, contracting, and data owners for critical lines of business are just some of the parts of an organization that need to work in collaboration to share information to mitigate insider threats.
With so many stakeholders playing different parts in insider threat mitigation within an organization, it is vital to have a designated resource that coordinates these efforts and centralizes the needed resources. A formalized insider threat program can, and should, play that role.
A formalized insider threat program is characterized by having
- a directive, charter, or other policy document that establishes the program
- documented statements of its mission, scope, and authorities under which the program will operate
- a defined governance structure that helps produce, review, and approve the program's standards, practices, and operating procedures
- a dedicated operating budget
Due to the organization-wide participation that effective insider threat programs require, senior leadership buy-in and continued support are critically important to the success of any insider threat program. An insider threat program is responsible for establishing clear roles and responsibilities for all insider-threat-related efforts across the organization.
The IC Analyst-Private Sector Partnership Program, sponsored by the Department of Homeland Security's Office of Intelligence and Analysis on behalf of the Director of National Intelligence, developed a roadmap that can be used as a framework for building an insider threat program. We also recommend the 13 components, presented in the diagram below, for inclusion in an insider threat program.
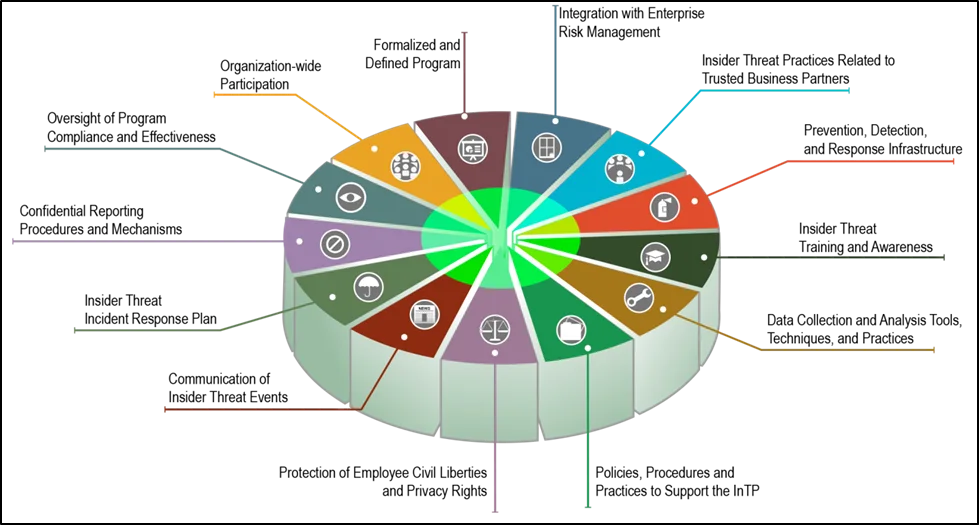
Refer to the complete fifth edition of the Common Sense Guide to Mitigating Insider Threats for a comprehensive understanding of the issues and recommendations I've mentioned here.
Check back next week to read Practice 3: Clearly document and consistently enforce policies and controls, or subscribe to a feed of the Insider Threat blog to be alerted when a new post is available.
For more information about the CERT Insider Threat Center, see www.cert.org/insider-threat, or contact info@sei.cmu.edu.
More By The Author
More In Insider Threat
PUBLISHED IN
Insider ThreatGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Insider Threat
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
