Effectiveness of Microsoft Office File Validation
PUBLISHED IN
CERT/CC VulnerabilitiesMicrosoft recently released a component for Office called Office File Validation that is supposed to help protect against attacks using malformed files. Because I recently performed file fuzzing tests on Microsoft Office, I decided to test the effectiveness of Office File Validation.
Background
Before a file is opened, Office File Validation analyzes the file's structure to determine if it is well-formed. Office will warn the user if a file has failed validation before the file can be opened. To increase protection, Office File Validation can be configured to automatically block malformed files from being opened rather than giving the user a choice. Until recently, this feature was only available with Microsoft Office 2010. Office File Validation is now available as an optional add-on for Microsoft Office 2003 and 2007.
Microsoft states, "Office File Validation helps detect and prevent a kind of exploit known as a file format attack or file fuzzing attack." I was able to test the accuracy of this claim by using the crashing test cases from the brief Office fuzzing campaign that I performed.
The Test
To test Office File Validation, I used a set of 100 DOC files that cause Microsoft Word 2003 to crash in unique ways. The test environment is fully patched as of May 19, 2011. Rather than using the raw fuzzed files from our fuzzing framework, I used the minimized test cases. After determining that a file causes an application to crash, the framework will attempt to generate a file that is minimally different from the original seed file but that still causes the same crash. In other words, the files are as well-formed as possible, yet they still cause Word to crash.
The Results
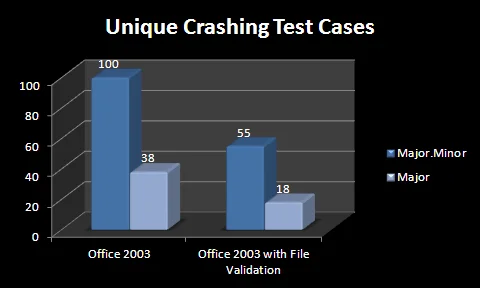
When a crash is encountered, !exploitable assigns a crash Major and Minor value to help determine uniqueness. By using both the Major and Minor hash values, the original set of 100 crashes is reduced to 55. In this particular set of test cases, this corresponds to a 45% reduction in attack surface. If you consider just the crash Major values, the number of cases that cause unique crashes goes from 38 to 18, or a 53% reduction in attack surface.
Conclusion
The Microsoft Office File Validation add-on does help prevent file fuzzing attacks. Although the protection it provides is far from comprehensive, the protection is significant enough to warrant its use. I recommend that Office 2003 and Office 2007 users install Office File Validation to help minimize the attack surface of the Microsoft Office products. It is important to realize, however, that because Microsoft Office File Validation does not block all malformed files, additional runtime exploit mitigations should be used to help keep you safe. The blog entry about fuzzing Microsoft Office outlines these mitigations. Incidentally, Microsoft has released an updated version of EMET, which provides additional exploit mitigation techniques and improves support for enterprise deployments. I strongly encourage users and administrators to evaluate its use.
More By The Author
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
