Cybersecurity of Quantum Computing: A New Frontier
Research and development of quantum computers continues to grow at a rapid pace. The U.S. government alone spent more than $800 million on quantum information science (QIS) research in 2022. The promise of quantum computers is substantial – they will be able to solve certain problems that are classically intractable, meaning a conventional computer cannot complete the calculations within human-usable timescales. Given this computational power, there is growing discussion surrounding the cyber threats quantum computers may pose in the future. For instance, Alejandro Mayorkas, secretary of the Department of Homeland Security, has identified the transition to post-quantum encryption as a priority to ensure cyber resilience. There is very little discussion, however, on how we will protect quantum computers in the future. If quantum computers are to become such valuable assets, it is reasonable to project that they will eventually be the target of malicious activity.
I was recently invited to be a participant in the Workshop on Cybersecurity of Quantum Computing, co-sponsored by the National Science Foundation (NSF) and the White House Office of Science and Technology Policy, where we examined the emerging field of cybersecurity for quantum computing. While quantum computers are still nascent in many ways, it is never too early to address looming cybersecurity concerns. This post will explore issues related to creating the discipline of cyber protection of quantum computing and outline six areas of future research in the field of quantum cybersecurity.
What is Quantum Computing?
The common computers that most people use every day are built on the binary logic of bits, which are based on 0 and 1 as represented by a binary physical property, such as whether flow of electricity to a transistor is off or on. These traditional computers are typically referred to as classical computers when discussed in relation to quantum computers. In contrast to the binary nature of classical computers, quantum computers use qubits, which are capable of being in a superposition of two states at the same time (i.e., representing both a 0 and 1 at the same time). One analogy to understanding superposition is to consider flipping a coin. A classical computer can represent the coin as being heads or tails after the coin lands. A quantum computer, on the other hand, can represent the coin as both heads and tails at the same time while it is still flipping in the air.
The capability of quantum computers is further enriched by the property of entanglement, which enables distributed encoding of information. Quantum entanglement allows qubits that are separated, even by significant distances, to interact with each other instantaneously. Entanglement occurs when particles interact in such a way that each particle’s quantum state cannot be described independently of the state of the others. That is, the measured states of entangled particles are correlated such that measurement of state for a single particle enables probabilistic prediction of state for others. Consider the coin flipping example from above; now imagine that two coins are flipped at the same time. As they are flipping in the air, the states of each coin are correlated.
Collectively, quantum superposition and entanglement enable substantial computing power. Consider that a 2-bit register in a classical computer can store only one of four binary combinations (00, 01, 10, or 11) at a given time, but a 2-qubit register in a quantum computer can store all four of these numbers simultaneously. As more qubits are added, this computational advantage of quantum computers over classical computers grows exponentially.
Cyber Threats to Quantum Computers
The current state of quantum computer systems is often referred to as the NISQ (noisy intermediate-scale quantum) era, characterized by quantum computers that offer moderate computing power and are still challenged by system fidelity. Current quantum computers are volatile and unstable, with error-correction for quantum calculations still being addressed. While researchers work to solve these challenges, it is apparent that in the near-term—and further into the near-future—quantum computers will most likely be used as co-processors in hybrid systems in which classical computers will hand off mathematical calculations to the quantum computer as part of a larger system workflow that still heavily depends on classical computers. The diagram below shows a notional concept of the components for a quantum-classical hybrid commuting environment. Implementation details will vary by quantum architectures, but similar layers will exist in all quantum-classical hybrid computers.
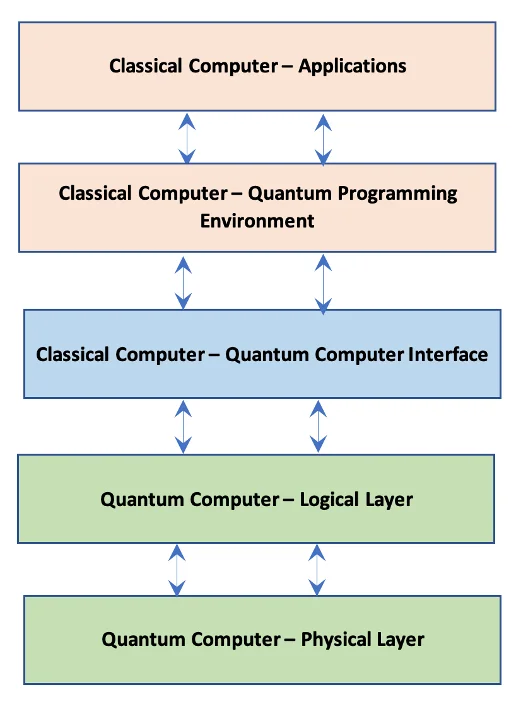
Understanding how quantum computers will be integrated with classical computers is essential to considering the cyber threats to quantum computers. The interface between classical and quantum computers in the hybrid computing environments typical of the NISQ-era is an area ripe for cybersecurity threats. This interface is literally the gateway between the classical and quantum environments, so it can serve as a conduit for known exploits of classical computers to traverse into quantum areas. In short, there are already many known cyber attack techniques for classical computers that can be leveraged to compromise a hybrid system.
Another attack vector stems from novel approaches for control and measurement of quantum devices that will be implemented in these interfaces. Application-specific integrated circuits (ASICs), field-programmable gate arrays (FPGAs), digital-to-analogue converters (DACs), and other elements of classical-quantum interfaces are being used in new ways. The current focus of research in designing these interfaces is on functionality and performance, yet security concerns also must be addressed. Given the many known techniques for compromising classical computers, it seems probable that attacks on quantum computers will originate in weaknesses in classical computers and then propagate to the quantum-classical interface.
Research sponsored by Microsoft Quantum Sydney outlines scalability issues related to current approaches for classical-quantum interfaces. The study highlighted challenges related to I/O management, heat and power dissipation, system footprint, noise and interference, and bandwidth. While these issues are presented in relation to scalability, the same issues provide avenues for attack. For instance, attackers can leverage the heat sensitivity to enable a denial-of-service attack or the proclivity for noise and interference to attack the integrity of operations. Our work in cybersecurity of classical computers has taught us that any system failure can provide an opening to exploit a system.
While securing the classical-quantum interface is a critical element in quantum cybersecurity, there are other areas to address. For instance, the output of quantum computing calculations will be much more valuable to protect (and valuable to steal) than most classical computer output, given the resources necessary to perform the calculations and derive the output. For instance, a commercial pharmaceutical company using a quantum computer to solve a complex chemistry problem will consider that output quite valuable because it may be hard to reproduce and the end-product will contain highly valuable intellectual property.
Moreover, the vast computing power in quantum computers necessitates protecting the quantum computational power itself. That is, not just protecting algorithms and their outputs but also detecting and protecting against hijacking of quantum computing capability, in the same way a botnet attack hijacks classical computing power. For example, if adversaries do not have quantum computing power of their own, but want to perform a resource-intensive calculation, then they may try to get unauthorized access to someone else’s quantum capability. Likewise, an adversary may just want to disrupt quantum-based computations solely to adversely influence the results.
Lastly, a key difference between quantum computers and classical computers is their sensitivity to temperature and the physical world in general, which opens new vectors for denial-of-service-attacks. For instance, the refrigeration requirements for many quantum architectures opens an avenue to perform a denial-of-service attack: disrupt the cooling for these architectures and their entire operation can be halted. These are the most pressing of the many threats to quantum computers that the new discipline of quantum cybersecurity must address.
6 Key Areas of Future Research in Quantum Cybersecurity
Since the design and architecture of quantum computers is still an open area of research with many alternatives being explored, it is premature to focus on specific vulnerabilities in specific systems. Researchers in this field must first form an understanding of current and future threats to quantum computers to develop more effective protections. The preceding section highlighted various threats to the confidentiality, integrity, and availability of quantum computers. This section highlights areas of research needed to develop protections against these threats.
For example, one key area for future research is the development of capabilities for monitoring quantum computations. Quantum processing cannot be monitored in the same ways that system monitoring is done for classical computers, which makes it hard to both assess what algorithms quantum computers are running and determine whether malicious processing is occurring. This gap illustrates the need for developing a multi-layered instrumentation framework for quantum computers, which is one of the following six key areas for future quantum security research we identified in the Workshop on Cybersecurity of Quantum Computing:
- Building secure large-scale control systems. The scale of the classical computation involved in supporting a large-scale quantum computer can be extensive. This support includes control systems and error correction, but it can also include monitoring for intrusions. Research is needed on building secure classical control systems for quantum computers.
- Enabling distributed high-performance quantum computing. Classical high-performance computing systems are typically multi-tenant and distributed. Addressing the security of multi-tenant and distributed quantum computers now can lay the foundation for more secure quantum computers when they achieve scale.
- Understanding attack vectors on different types of quantum computers. Deeper research on potential attack vectors for various quantum system models, such as whether adversaries only access quantum devices through a user interface, is needed to more fully understand how to secure quantum computers.
- Creating formal methods for safe and secure quantum computing systems. In computing, formal methods refer to rigorous mathematical techniques for specifying, developing, and verifying computer software and hardware. Research is needed on developing formal methods for quantum computing to achieve trustworthy quantum computing.
- Constructing a multi-layered instrumentation framework. Such a framework would allow security-relevant properties of quantum computers to be enforced or verified.
- Developing the necessary tools for service providers to verify quantum algorithms. These tools will enable the ability to verify and control which algorithms are running on a quantum computer, also helps ensure that a quantum computer will not perform undesirable behaviors.
While all these areas of research are critical for protecting quantum computers, the landscape of cyber threats will continually change as quantum computing technology evolves. All the above areas should be researched and, in tandem, additional areas for quantum cybersecurity research should be added as they become relevant. Techniques for protecting classical computers, such as threat modeling and considering ways to compromise the principles of the confidentiality, integrity, availability (CIA) triad, must be applied continually to quantum computers to discover emerging threats to research as this field of quantum cybersecurity advances.
Securing Increased Quantum Deployment Conclusion
As quantum computing becomes more practical, organizations must answer many questions about how to leverage it for strategic use. Increased quantum deployment will raise many technical questions about how data is prepared and transferred to quantum computers, how algorithms are implemented in quantum computers, and how quantum computing results are returned and verified. With all these technical considerations, an overarching question will be, How can this all be done securely? Here at the CERT Division of the SEI, we have a long history of protecting software and computing systems. Moreover, when the time comes to make smart, secure decisions about utilizing quantum computers, we are ready to welcome you to quantum cybersecurity!
Additional Resources
Read the Summary of the Workshop on Cybersecurity of Quantum Computing.
More By The Author
More In Quantum Computing
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Quantum Computing
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
