Bundled Software and Attack Surface
PUBLISHED IN
CERT/CC VulnerabilitiesHi, it's Will. We are all probably annoyed by software that bundles other applications that we didn't ask for. You want a specific application, but depending on what the application is, where you downloaded it from, and how carefully you paid attention to the installation process, you could have some extra goodies that came along for the ride. You might have components referred to as adware, foistware, scareware, potentially unwanted programs (PUPs), or worse. Sure, these may be annoyances, but there's an even more important security aspect to these types of applications: attack surface.
Recently I was working in a virtual machine, and I needed to extract an archive. 7-Zip seemed like a reasonable choice, so I used the default search engine in the default browser in the virtual machine:
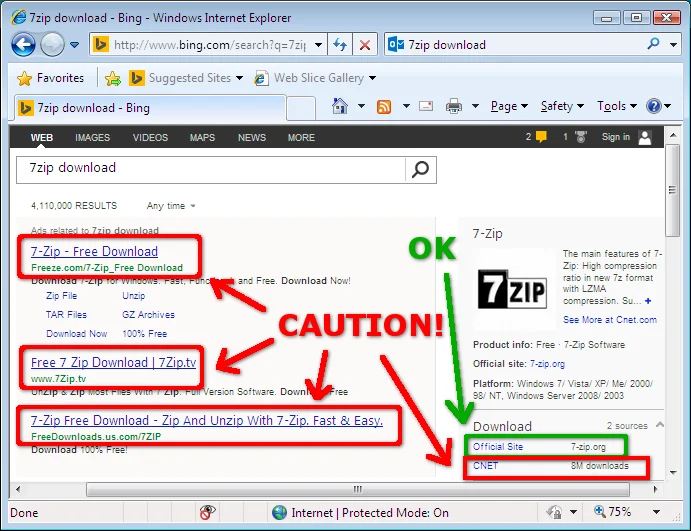
I encountered quite the minefield, and I hadn't even gotten to the point of downloading anything yet! It's not that any of the sites outlined in red are necessarily malicious, but rather, if 7-zip is installed from any of those sites, I will likely end up with additional unwanted software. This got me wondering about what sort of software other folks might be downloading.
There are sites that are known for bundling installers for the purpose of generating advertising revenue, such as Download.com, Softonic.com, or Winstally.com. Let's look at a single download from one of the many sites where you can download software, in particular, KMPlayer from CNET Download.com. I chose this application from the list of popular downloads that Download.com provides. In any given week, this application is downloaded approximately half a million times.
A simple thing to do with a file that you're curious about is to upload it to virustotal.com. The results of the KMPlayer installer from Download.com are interesting. As of the publication of this blog entry, four different AV products detect that the Download.com installer for KMPlayer contains potentially unwanted software.
As it turns out, the behavior of the Download.com installer wrapper has been known for years. The Electronic Frontier Foundation (EFF) wrote about it in 2011. Several other sources have discussed Download.com installer issues as well. It's pretty clear that installing software from Download.com and other similar sources may result in unwanted software being installed with the software you wanted. But what are the security aspects of such bundling?
For now let's ignore the specific behaviors of the bundled software and just consider the fact that you have more software on your system. Generally speaking, the more software you have on your system, the larger your attack surface. And the larger the attack surface, the higher the risk.
Let's say that we don't have one of the 4 AV products that would warn us when we attempt to run the Download.com installer for KMPlayer, so we proceed with installation. We are first presented with a dialog stating that the download is secure and has been ensured to be virus and spyware free, which is good to know.
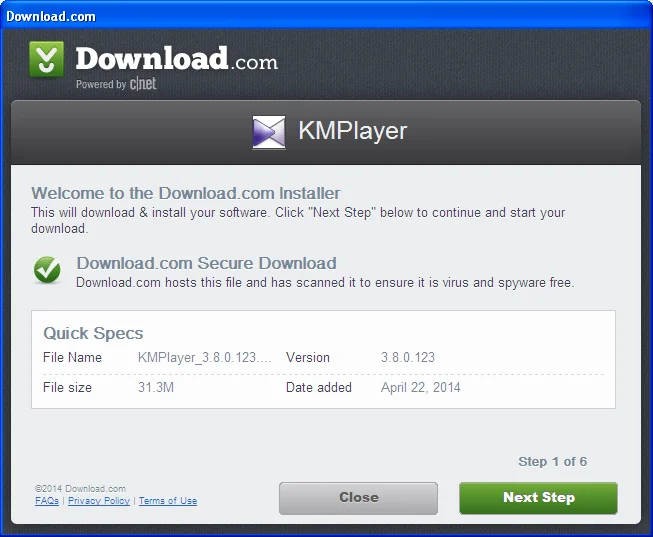
As soon as we click into the installer, we are presented with the first advertising-supported offer:
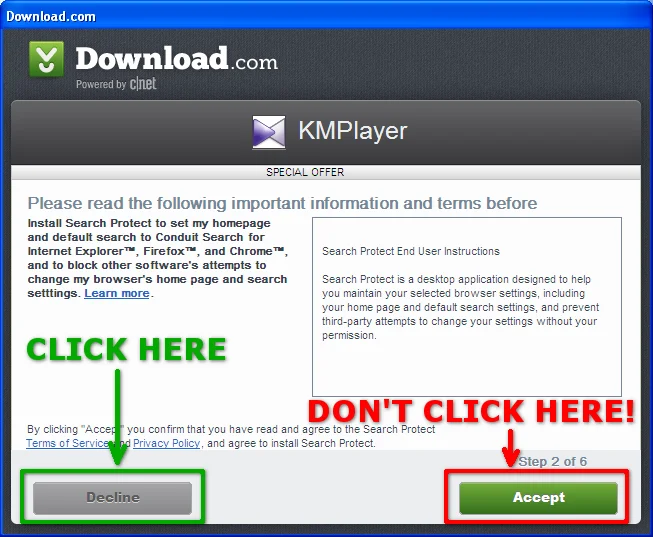
The nature of this dialog is deceptive, presumably with the intention of convincing more people to install additional software. First, the green "Next Step" button in the previous step has been replaced with an "Accept" button. So if the user has not moved the mouse and simply clicks through to the next step, the extra bundled software will be installed. Second, the "Decline" button appears to be disabled and the user may believe that clicking it may cancel the entire installation process. What the button actually does is opt out of installing additional unnecessary software.
If we're not careful, we'll end up with software called "Search Protect," which installs a service that runs with SYSTEM privileges and also spawns two separate processes that run with the privileges of the currently logged-on user. If we continue with the installation, there are two more offers in the Download.com wrapper installer. The offers seem to be somewhat dynamic, but I've seen things like PassShow, RRSavings, and AtuZi. These sorts of programs hook into your browser, exposing a larger attack surface, and potentially making the system less secure. Once we get through the Download.com wrapper installer, we finally get to the KMPlayer installer itself:
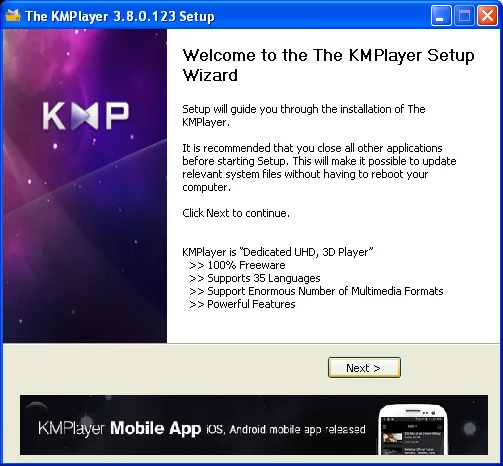
Great. Now we can install the software we actually wanted in the first place. But wait, there's more!
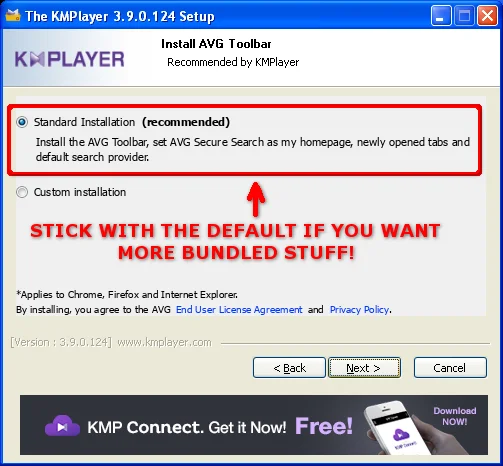
The default installation may include AVG Secure Search software. Despite the software claiming to provide "an additional security layer while searching and surfing," its installation means more code on your system and therefore another thing that attackers might target. The download also provides a web browser toolbar, installs an ActiveX control that bypasses the Internet Explorer Protected Mode sandbox as well as the ActiveX Opt-in feature introduced with IE7, and it changes the browser's homepage.
Given that CERT has an awesome ActiveX testing tool called Dranzer, I figured that I would take a quick look at this particular control. As it turns out, this one ActiveX control, called ScriptHelper, exposes a number of dangerous methods for anybody on the internet to abuse (CERT VU#960193). This is a perfect example of more software putting you at increased risk.
So now, since we might not want the AVG Secure Search software and we definitely don't want the ActiveX control, we choose custom installation:
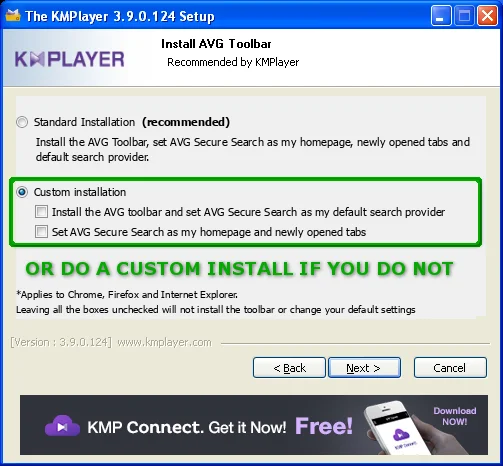
Just when we think we're past additional software, there's even more:
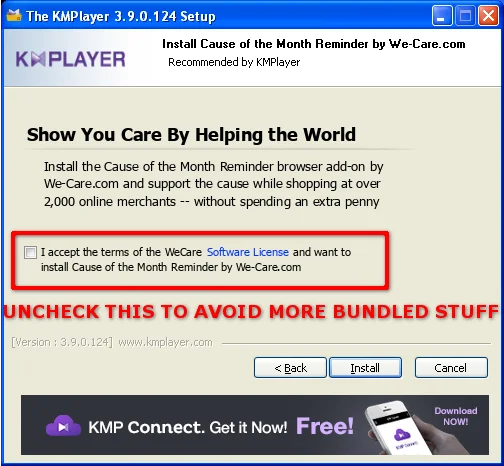
Here we can uncheck the box to let the installer know that we don't care about helping the world or else we'll get more unwanted code on our system.
Finally, we're done installing the software. Time to celebrate! We'll fire up our web browser to look at the newest kitten photos. If we did not go through the extra steps of deselecting the bundled software, we'll start getting browser pop-ups like this:
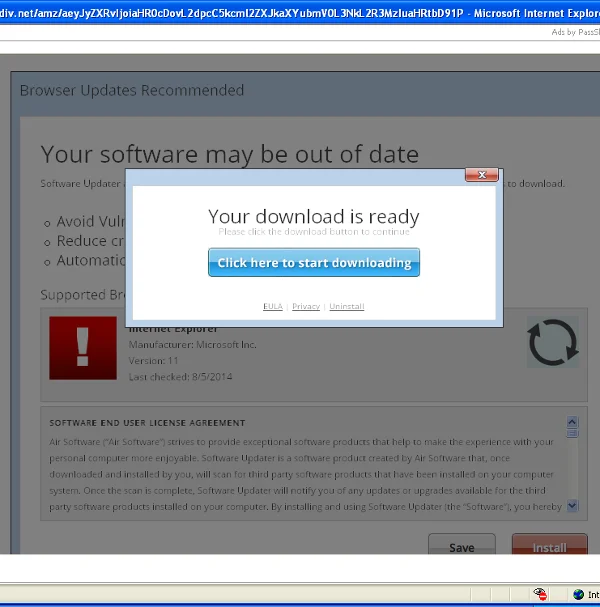
The version of Internet Explorer in the virtual machine I used for testing was horribly out of date, so I clicked away to get the update. Look at the VirusTotal report for this download. This one looks even scarier than the last. Every new application loaded onto the system comes bundled with even more unwanted software. At this point, between the pop-ups, the runaway CPU usage, and application crashes, the virtual machine was nearly unusable.
This all started from a single application installed from Download.com. The other advertising-supported recommendations from my original search engine query also put the system in a similar state in the end: slow, bloated, and having an increased attack surface.
Conclusion
Free software isn't always free. Just because you're not paying money out of your wallet doesn't mean that there isn't an economic transaction occurring somewhere as the result of installing the software on your computer. Certain vendors pay money to get their software loaded on to computers. So when you download a free application that is free only because it is bundled with adware, consider the security implications of your actions.
A good strategy is to try your best to find the official developer's website for the software so that you can download it directly. Regardless of the search engine that you use, be aware of which links in the results are from advertisers and avoid those. Be aware of sites that are known for bundling installers for the purpose of generating advertising revenue, such as Download.com, Softonic.com, or Winstally.com.
If you must use a service known for bundling adware into their installers, pay careful attention to the installation steps to make sure to opt out of any additional software choices provided. Even installing applications such as Oracle Java or Adobe Flash may result in unwanted software, such as browser toolbars, if you are not careful.
One strategy for helping to stay safer on the internet is to minimize your attack surface. More software is not the solution, it's the problem.
More By The Author
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
