Announcing CERT Tapioca 2.0 for Network Traffic Analysis
PUBLISHED IN
CERT/CC VulnerabilitiesA few years ago, I announced the release of CERT Tapioca for MITM Analysis. This virtual machine was created for the purpose of analyzing Android applications to find apps that don't validate SSL certificates. Since the original release of Tapioca, we have received a request to make it easier to use and add some additional features.
The new version of CERT Tapioca improves on the original in multiple ways in that it offers the following:
- is installable on multiple Linux distributions.
- contains a GUI.
- includes the ability to utilize a HOSTAP-compatible WiFi adapter for providing wireless connectivity.
- can save results from multiple targets tested.
- can search network traffic for specified strings.
With this blog post I will describe a few use cases of CERT Tapioca.
Downloading CERT Tapioca
CERT Tapioca is available for download from github. The README contains information that you will need to get started with installing and using it.
Confirming HTTPS Validation
The original use case for CERT Tapioca was to discover applications that do not properly validate HTTPS (SSL or TLS) certificates. The discovery of this validation failure occurs through the use of mitmproxy to perform a MITM attack on HTTPS traffic. Because the traffic is intercepted and re-encrypted using a key associated with a self-signed certificate, any application that accepts HTTPS traffic that is intercepted with mitmproxy is vulnerable.
To verify VU#846320, we can install CERT Tapioca in a virtual machine with two network adapters. The first network adapter is for providing network connectivity to the Tapioca machine, and the second adapter is configured to provide internet connectivity to another virtual machine that has the software we wish to inspect. In this case, it's Samsung Magician 5.0. In the virtual machine that has CERT Tapioca, we configure the second network adapter to live on a specific virtual network segment. In VMware Workstation parlance, we set the network adapter to use the network connection "Custom: Specific virtual network", and select an unused VMnet number. With the virtual machine that has the software we want to test, we configure it to use the same VMnet virtual network. When this virtual machine is powered on, it obtains an IP address from the CERT Tapioca machine, and all network traffic is routed through the Tapioca machine as well.
To confirm whether HTTPS traffic is properly validated, click the "Capture - Verify SSL validation" button in Tapioca and then run the program in the second virtual machine. Once you have stopped the capture, click the "Generate reports" button. If we click the "FAILED" text, we can see that Samsung Magician 5.0 uses HTTPS, but it does not validate the certificates. That is, it will happily communicate with a server that is an impostor. In this case, it is making an HTTPS connection with mitmproxy in the CERT Tapioca machine, rather than the server it wishes to communicate with.
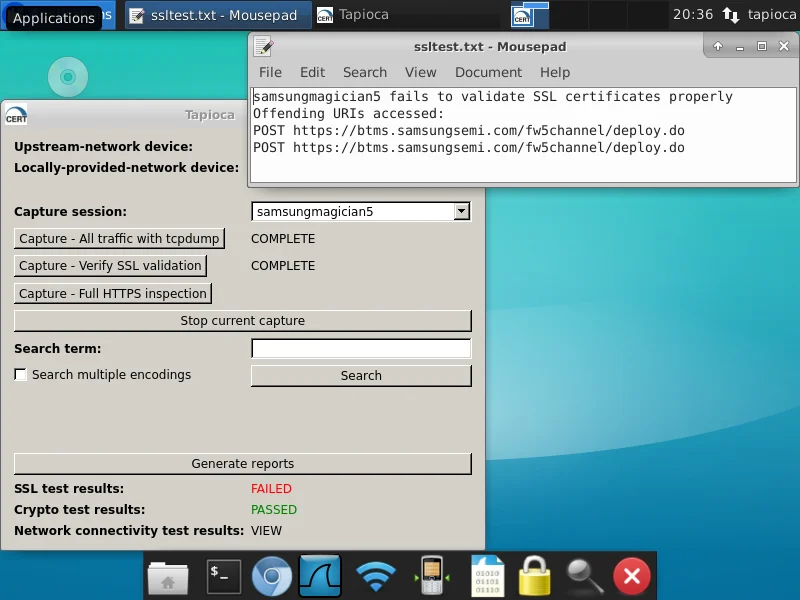
Confirming Crypto Standards
Similar to the HTTPS validation test, we can also test whether an application uses modern cryptography standards. For this test, we will run Internet Explorer 6.0 on a Windows XP SP3 virtual machine through CERT Tapioca. In this case, we will use the "Capture - All traffic with tcpdump" button. This is to ensure that we are observing the unadulterated network traffic, rather than attempting to MITM the traffic with mitmproxy. When we click the "FAILED" text next to "Crypto test results", we can see the reasons why IE 6 is unsafe to use:
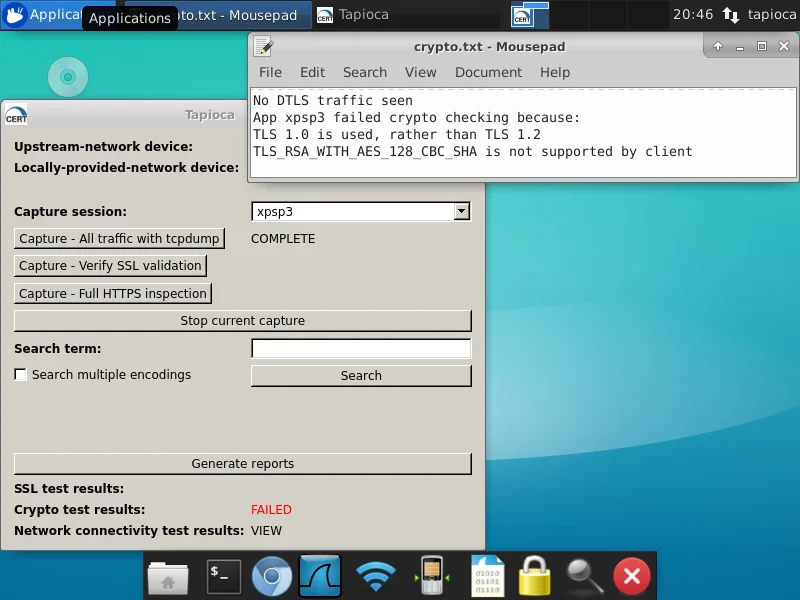
In this case, the target software is unsafe because it uses the deprecated TLS 1.0 protocol. Internet Explorer on Windows XP SP3 also does not support the TLS_RSA_WITH_AES_128_CBC_SHA cipher suite recommended by NIAP.
Observing Network Connectivity
Sometimes it is useful to know what hosts are contacted as the result of running an application. In this case, we will look into the Accuweather application on an Android phone. Since we are using a physical Android phone, we will use the "Soft AP" capability of CERT Tapioca. After connecting a HOSTAP-capable WiFi adapter to Tapioca, we click the WiFi icon, and the Wireless network will be created. After connecting the Android phone to the newly-created "Tapioca" network, we click the "Capture - All traffic with tcpdump" button and run the Accuweather application. After the network traffic has settled down, we stop the capture and press the "Generate Reports" button. After this is complete, we can click "VIEW" next to "Network connectivity test results" to see which hosts are contacted, as well as which DNS lookups are performed as the result of running the application.
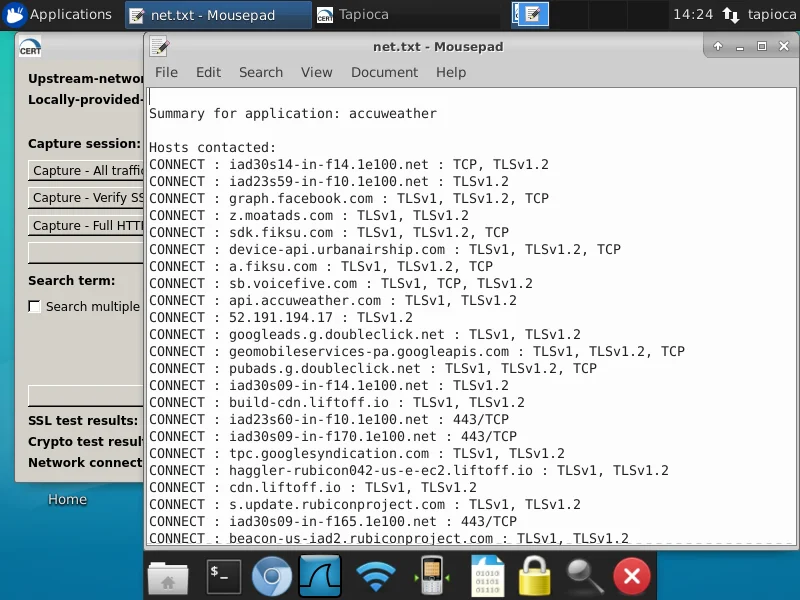
Here we can see which hosts are contacted, as well as which protocol was being used to communicate with them. This sort of analysis can be done with a tool like Wireshark, but depending on the volume of network traffic captured, the analysis can be pretty labor intensive. CERT Tapioca makes it easy!
Searching for Terms
CERT Tapioca includes the ability to search for strings within the network traffic. For example, if I have a password that includes the string "asdf" in it, I would like to know how and when the string "asdf" goes over the network. In this case, we will install the mitmproxy root CA certificate in our client system to get full HTTPS visibility into the traffic. First we will click the "Capture - Full HTTPS inspection" button to use a static key/certificate pair in mitmproxy. Then on our client system, we visit http://mitm.it to get the CA certificate to install. Depending on the platform and OS version our client is running, the steps to install this certificate may vary. Note that starting with Android Nougat (7.0), Android applications will not accept user-installed root CA certificates. In these cases, potential workarounds include installing the CA certificate in a rooted phone, or modifying the Android application to accept the user certificate.
In our case, we'll install the mitmproxy root CA certificate into a Windows system. After installing the certificate, we'll use our web browser to attempt to log in to outlook.com. After finishing the full HTTPS inspection capture with Tapioca, we can use the search box to look for "asdf":
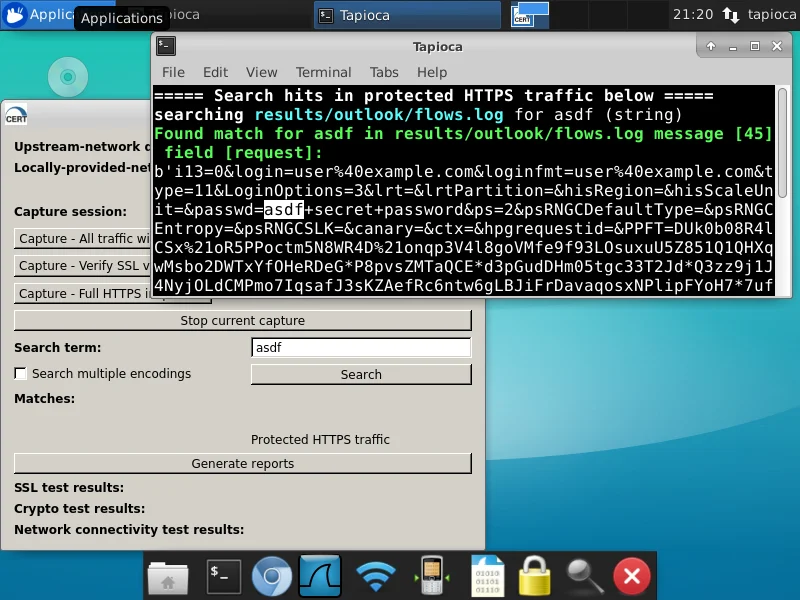
Here we can see that in the request part of mitmproxy message 45, the string "asdf" appears. It also reports that the string appears in protected HTTPS traffic, meaning that the string should be protected by HTTPS. If Tapioca reports that the string we are looking for is in unprotected HTTPS traffic or is in HTTP traffic, then this string would be visible to an attacker.
If we click on the "Protected HTTPS traffic" text under "Matches:", we can view the mitmproxy traffic where the string was found. By selecting message 45, we can see the traffic seen by mitmproxy:
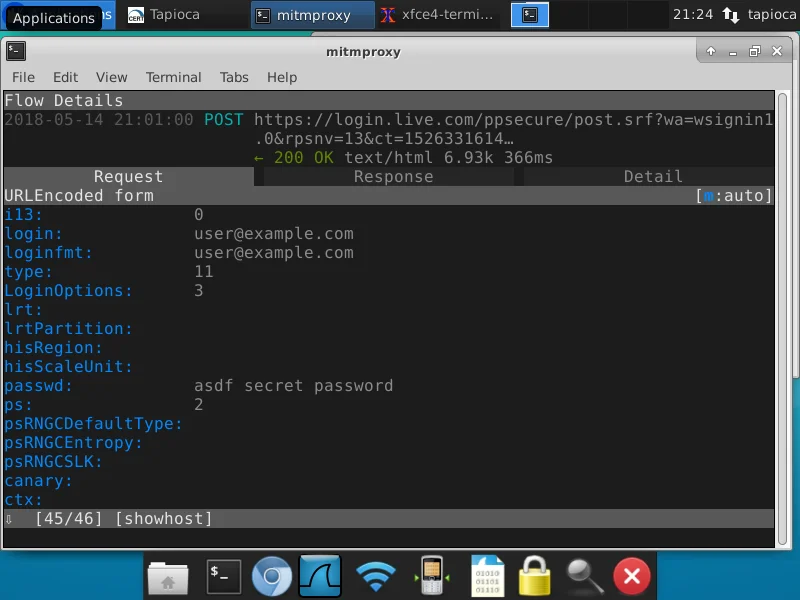
Here we can see the login attempt using user@example.com and the password "asdf secret password".
Conclusion
Network traffic analysis can give you some insight into what applications are doing. CERT Tapioca makes this analysis easier. Grab your copy now!
More By The Author
More In CERT/CC Vulnerabilities
PUBLISHED IN
CERT/CC VulnerabilitiesGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
