An Introduction to the Cybersecurity Maturity Model Certification (CMMC)
PUBLISHED IN
Enterprise Risk and Resilience ManagementAndrew Hoover co-authored this blog post.
A recent study predicted that business losses due to cybercrime will exceed $5 trillion by 2024. The threat to the Defense Industrial Base (DIB)--the network of more than 300,000 businesses, organizations, and universities that research, engineer, develop, acquire, design, produce, deliver, sustain, and operate military weapons systems--is especially alarming due to current cyber warfare activities by cybercriminals and state-sponsored actors. A cyber attack within the DIB supply chain could result in devastating losses of intellectual property and controlled unclassified information (CUI). To bolster cybersecurity posture within the DIB supply chain, SEI researchers have spent the last year helping the federal government develop the Cybersecurity Maturity Model Certification (CMMC) 1.0. This post details the development of the model and its role in securing the DIB.
CMMC Development
The Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) recognizes that security is a foundational component of acquisition and that some contractors are trading security to benefit cost, schedule, and performance. Our adversaries are committed to acquiring critical U.S. intellectual property through cyber-enabled theft, and have already proved successful in many instances. It's estimated that the DoD supply chain consists of more than 300,000 businesses and organizations, all of which are targets. Most of these organizations are small to mid-size businesses, which are the most vulnerable to cyber-attacks. According to Verizon's 2019 Data Breach Investigation's Report, organizations with up to 250 employees have the highest targeted malicious email rates.
Moreover, supply chain attacks are increasing at an alarming rate, which has huge implications for the DoD. OUSD(A&S) sought the development of an approach that would help DIB contractors secure unclassified information throughout the supply chain. While there are two types of unclassified information, federal contract information (FCI) and controlled unclassified information (CUI), the chief concern is with CUI, which is sensitive information (such as contractor rates or architecture documents) that is not classified. The U.S. National Archives and Records Administration (NARA) defines CUI as:
information that requires safeguarding or dissemination controls pursuant to and consistent with laws, regulations, and government-wide policies.
The CMMC framework draws on maturity processes and cybersecurity best practices from multiple standards, including the National Institute of Standards and Technology (NIST) frameworks and references, as well as input from DIB entities and the DoD. Before the development of CMMC, DIB organizations self-certified their compliance with NIST SP 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations, and listed gaps on a Plan of Actions and Milestones (POA&M). With CMMC, DIB organizations will be required to complete an assessment of all their CMMC practices at a particular level and become certified by a CMMC third-party assessment organization (C3PAO). POA&Ms will not be allowed under CMMC. This is a significant change from the current DFAR since an organization will need to have all requirements implemented in order to work on contracts at that level.
In addition to securing the DIB supply chain, which will facilitate the rigorous measurement of cybersecurity capabilities, the CMMC framework will enable the DoD to make risk-informed decisions regarding the information it shares with DIB contractors. All this information will help to create justified confidence in DIB partners.
After CMMC is implemented fully, DIB companies will be required to achieve a CMMC certification level prior to bidding on contracts. The CMMC levels will range from Basic Hygiene to State-of-the-Art. Eventually, the required CMMC level for a specific contract will be contained in DoD requests for proposals (RFPs).
In 2019, the SEI built the initial versions of the CMMC in collaboration with the Johns Hopkins University Applied Physics Laboratory, a university affiliated research center. The SEI team served as key architects in the development of the CMMC model, drawing upon our experience in cybersecurity, cybersecurity assessments, and process maturity. Version 1.0 of the model was released in January 2020, and pilot testing will occur later in 2020. The SEI, in support of OUSD(A&S), will work to assist with future implementation of the cybersecurity maturity model.
CMMC Model Structure
The goal of CMMC is to provide a framework for the improvement of cybersecurity in DIB sector organizations. CMMC currently defines 17 domains of technical capability, each with five levels of certification (L1 through L5) and specific practices. The DoD will require an organization to have CMMC Level 3 certification before it can receive CUI in any domain.
Fourteen of the CMMC's 17 domains originate from the security-related areas in two publications:
- Federal Information Processing Standards (FIPS) Publication 200, which spells out minimum security requirements for federal information and information systems, and
- NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations.
To these 14 domains, the CMMC model adds Asset Management (AM), Recovery (RE), and Situational Awareness (SA).
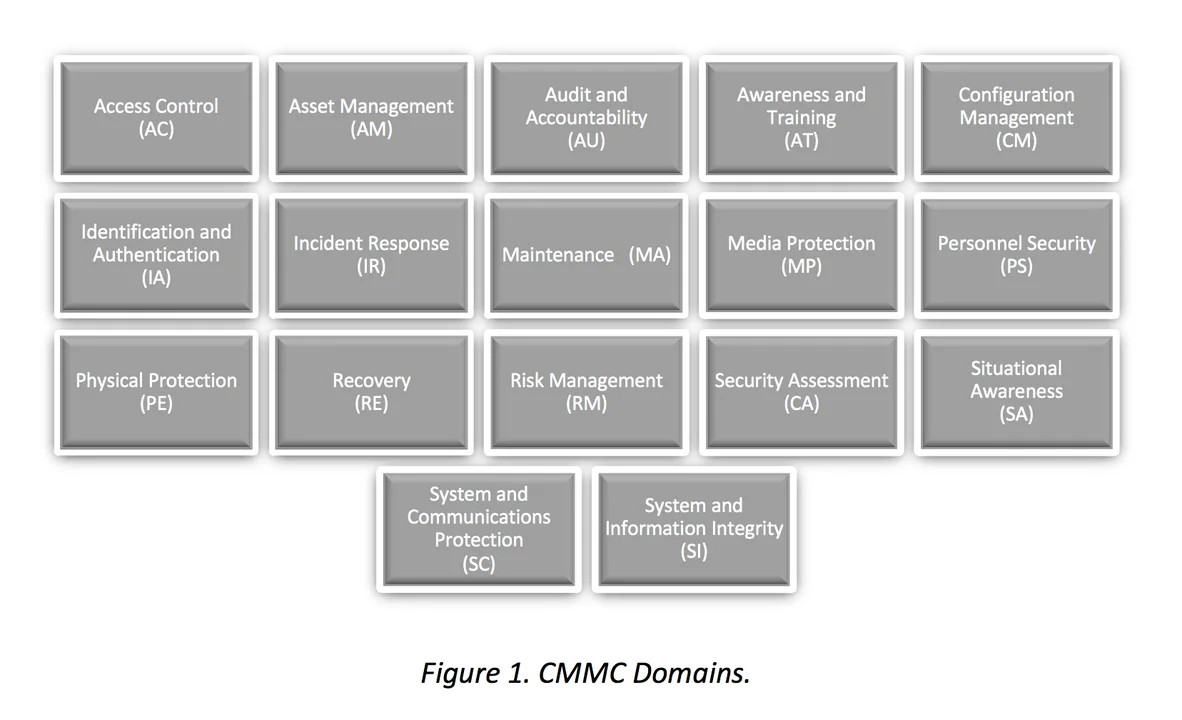
Figure 1. CMMC Domains.
A total of 171 technical practices span the 17 capability domains. In addition, for each capability domain, there are five maturity processes, Maturity Level 1 (ML 1) through Maturity Level 5 (ML 5). To achieve a given CMMC level, an organization must demonstrate both the technical practices and maturity processes defined in that level, as well as those in the preceding, lower levels. If an organization demonstrates practice implementation at Level 3, but ML2 process implementation at Level 2, it will receive a Level 2 certification.
Leveled Practices
The majority of the practices (110 of 171) originate from the safeguarding requirements and security requirements specified in FAR Clause 52.204-21 and DFARS Clause 252.204-7012. The practices fall into five levels:
- Level 1 represents basic cyber hygiene, and focuses on the protection of federal contract information (FCI). It consists of practices that correspond only to the basic safeguarding requirements specified in 48 CFR 52.204-21 ("Basic Safeguarding of Covered Contractor Information Systems").
- Level 2 is a transitional step in cybersecurity maturity progression to protect CUI. Level 2 consists of a subset of the security requirements specified in NIST SP 800-171, as well as practices from other standards and references.
- Level 3 focuses on the protection of CUI. It encompasses all of the security requirements specified in NIST SP 800‑171, as well as additional practices from other standards and references.
- At Level 4, the model begins to focus more on the proactive activities an organization can take to protect, detect, and respond to threats. These practices enhance the organization's ability to address and adapt to the changing tactics, techniques, and procedures (TTPs) used by advanced persistent threats (APT)s.
- Level 5 focuses on the protection of CUI from APTs. The practices increase the depth and sophistication of cybersecurity capabilities.
Process Maturity
For each domain, the CMMC accesses process maturity starting at Level 2. The table below summarizes the maturity processes.
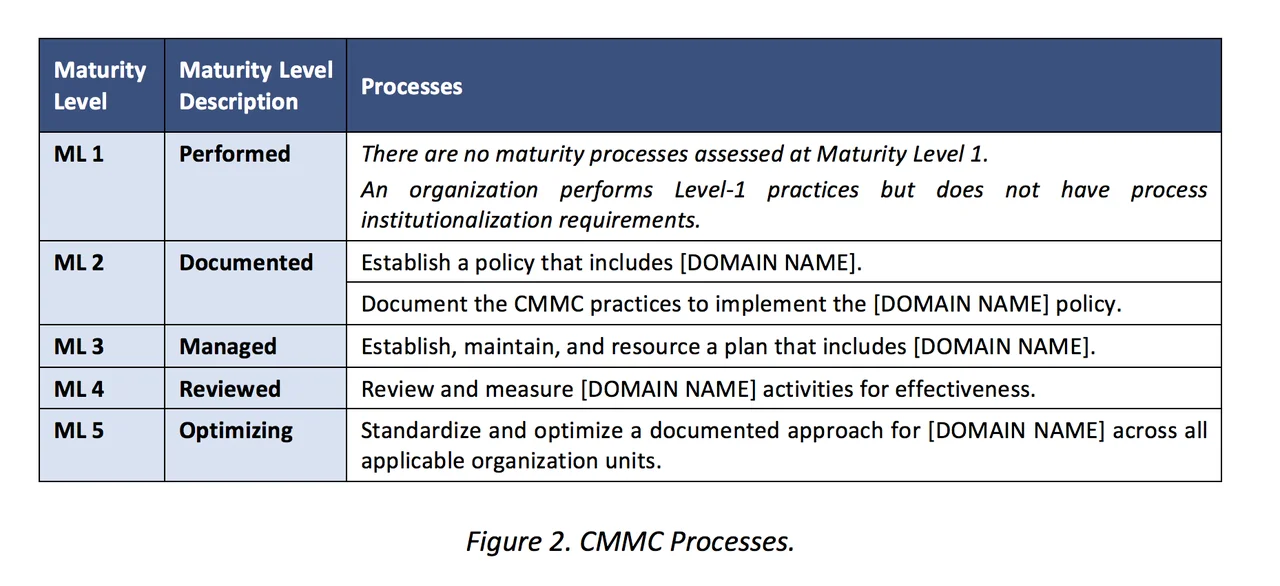
The defined maturity processes for each level assess process institutionalization, which measures how ingrained the CMMC practices are within an organization. Process institutionalization creates repeatable and mature processes that improve an organization's ability to both prevent and respond to a cyberattack.
A description of each maturity level (ML) is below:
- ML 1 requires an organization to perform the specified practices. Because the organization may perform these practices only in an ad hoc manner, process maturity is not assessed this level. Documentation, unless specified directly in the practice, is not required at ML 1.
- ML 2 requires an organization to establish and document practices within a domain. The documentation of practices enables an organization to execute the CMMC practices in a repeatable manner and to achieve expected outcomes. In addition, ML2 requires that the organization has a guiding policy that establishes the objectives and importance of the CMMC domain.
- ML 3 requires an organization to establish, maintain, and resource a plan for managing CMMC domain activities. The plan may include information on missions, goals, project plans, resourcing, required training, and involvement of relevant stakeholders. In addition, at ML 3, an organization must resource its CMMC activities as defined in the plan.
- ML 4 requires an organization to review and measure practices for effectiveness. Organizations at this level must also take corrective actions when necessary and inform higher level management of status or issues on a recurring basis.
- ML 5 requires a company to standardize and optimize process implementation throughout the organization. A company must develop procedures from standard guidance that senior management typically provides. In addition, a company must communicate and share improvement information throughout the organization.
Looking Ahead
A transition to the CMMC's maturity model certification approach will fundamentally change DIB sector security. Process institutionalization is a key component of CMMC. It also represents one of the largest changes to how DIB companies currently assess compliance.
In the next blog post in this series, we will explore CMMC Process Maturity in more detail.
Additional Resources
The CMMC Framework and accompanying DoD information is available for download: https://www.acq.osd.mil/cmmc/index.html
View the SEI webpage CMMC--Securing the DIB Supply Chain.
Download the fact sheet, CMMC--Securing the DIB Supply Chain with the Cybersecurity Maturity Model Certification Process.
More By The Authors
More In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
PUBLISHED IN
Enterprise Risk and Resilience ManagementGet updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In Enterprise Risk and Resilience Management
Process and Technical Vulnerabilities: 6 Key Takeaways from a Chemical Plant Disaster
• By Daniel J. Kambic
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed


