A Platform for Dynamic Defense Technologies
Dynamic Network Defense (or Moving Target Defense) is based on a simple premise: a moving target is harder to attack than a stationary target. In recent years the government has invested substantially into moving target and adaptive cyber defense. This rapidly growing field has seen recent developments of many new technologies--defenses that range from shuffling of client-to-server assignments to protect against distributed denial-of-service (DDOS) attacks, to packet header rewriting, to rebooting servers. As researchers develop new technologies, they need a centralized reference platform where new technologies can be vetted to see where they complement each other and where they do not, as well as a standard against which future technologies can be evaluated. This blog post describes work led by researchers at the SEI's Emerging Technology Center (ETC) to develop a secure, easy-to-use, consistent development and deployment path to organize dynamic defenses.
Foundations of Our Work
Moving Target Defenses are adaptations to a system that create unpredictable conditions for cyber attackers. A dynamic defense can include changes to any technical attribute (e.g., schema, format, or protocol) that can in theory be turned into a moving target project. Two of the more well-known dynamic defenses are Internet protocol (IP) hopping, which strengthens networks against DDoS attacks, and address space layout randomization (ASLR), which protects from buffer overflow attacks.
Last October, researchers from the ETC began a multi-year project to create a reference implementation for a dynamic network defense platform--a standard by which future implementations and customizations can be evaluated. Ultimately our research will focus on a variety of techniques from any layer of the stack: from policy to operating system to network and beyond. Examples include requiring periodic password changes to create a changing environment, protocol diversity to make network spoofing harder, and redundant data to allow for double-checks and restoration.
Our project has three overarching goals:
- Adoptability. The platform must be easily adoptable for the researchers who need it.
- Security. The platform must be designed securely from the ground up.
- Extensibility. The platform must be customizable and easily added to.
Collaborators
We are collaborating with Marco Carvalho, a professor at the Florida Institute of Technology (FIT); David Garlan, a Carnegie Mellon professor; and Bradley Schmerl, a systems scientist at Carnegie Mellon. Garlan and Schmerl are experts in self-adaptive systems, and both work at the Institute for Software Research (ISR) within Carnegie Mellon's School of Computer Science (SCS). Collectively, these three researchers have published dozens of papers in the last decade on self-adaptive systems. More recently, they have focused on applying their research to security.
Our approach blends two types of systems and builds on the expertise of our collaborators in each area:
- Self-adaptive Systems. Self-adaptive systems, which can evaluate and modify their own behavior to improve efficiency, are increasingly important in software-intensive systems. Self-adaptive systems have a central-reasoning component that is fundamental to the concept of how the system works and can be used to ensure properties such as resiliency, healing, optimizations, configuration, and protection. Our approach examines how to use the strength of self-adaptive systems to build a piece of middleware to enable researchers to deploy and test their creations.
ISR researchers approach adaptation through architecture. Specifically, Garlan and Schmerl emphasize that if an architecture is understood and its properties can be reasoned about, then it can be adapted based on various goals.
- Multi-agent Systems. Multi-agent systems, a loosely coupled network of software agents that interact to solve problems, are resilient and partition tolerant. Because they are decentralized--spreading services across a network so that services continue to be available even if one part of the network is disabled--they provide additional resiliency and redundancy that minimize the risks of single points of failure.
Multi-agent systems provide a variety of other performance qualities because they allow users to execute commutations locally instead of having to go through a centralized location, which brings additional vulnerabilities.
Human-in-the-Loop Support
As shown in the figure below, our approach blends multi-agent systems with hierarchical self-adaptive systems, and we add strong human-in-the-loop support.
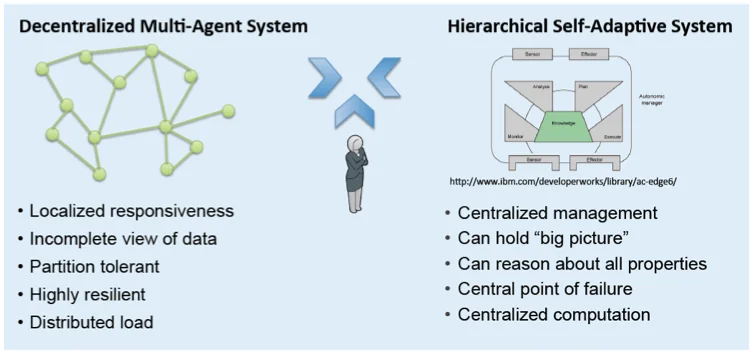
Human-in-the-loop support is notable because an important part of trusting a system is that the system must communicate with its users at a level at which they can actually be effective. Our approach makes system administrators a central component of the platform. Our goal is to ensure that the platform will allow system administrators who are defending the network to have a role in decision making and that the system's defenses be transparent to defenders.
In collaboration with our Carnegie Mellon collaborators, our team of researchers has extended the self-adaptive loop to include a strong human-in-the-loop approval component. Changes proposed by the autonomic system will have to go through a tunable human approval. For example, a recommendation might be to bring up "10 new servers to add additional capacity to your cloud." These will be very high-level recommendations that a sysadmin could quickly reason about and approve.
Our purpose is not to build the reasoning and planning engines, which are at the bleeding edge of research, but to provide a platform for collaborators and other researchers to build upon. Eventually the patterns and best practices developed in this project can be carried forward by industry into production environments.
Current Work and Requirements
The current work involves building a peer-to-peer distributed platform using Java. In our approach we use as much existing standards and open technologies as is practical. Where appropriate technologies are not appropriate (i.e. many technologies lack sufficient security) we augment or extend those to demonstrate the projects of tomorrow. The figure below shows a demonstration of our current work: a view of a network with the ability to run diagnostics on particular nodes, which provides the foundation for deploying the appropriate defenses.
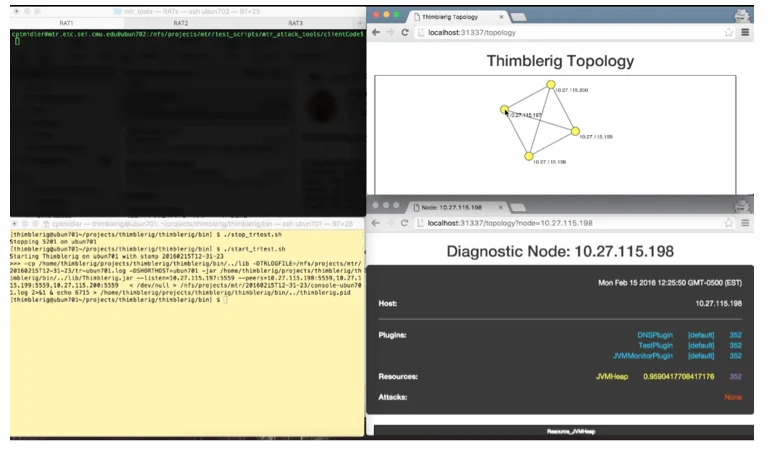
As we work, we focus on the following requirements:
- Flexibility: Our platform will flexibly support deployment and management of existing techniques and research of new techniques.
- Management of ensembles of techniques: Our platform will help identify where techniques interfere or complement one another and will enable reasoning about interactions and overall mission utility.
- Support at all levels of the stack: our platform will accommodate techniques of any type (e.g., policy, hardware, software).
- Strong human-in-the-loop support: including visualization, as described in the section above.
- Decentralization: our platform will work in a decentralized fashion and will be partition tolerant and highly available. This approach distributes services across the network to eliminate single points of failure.
- Advanced planning: our platform will have a rich data model for advanced planning, meaning it will take advantage of analytics as well as both proactive and predictive operations (routine actions that protect a network and actions performed based on actual information collected from sources like sensors).
- Federation: Our platform will share information and solutions.
- Security: We will structure the system design and architecture in such a way as to make the platform more secure. For example, we are using a sandbox similar to what Chrome and Firefox use for their executing plugins. In addition to accommodating a variety of defenses, our platform contains middleware that promotes secure design in extension components. Elements of our designed-in security include
- security architectures for middleware
- secure design and coding practices
- appropriate decomposition and privilege isolations
- strong management and policy configuration
Challenges
Many open-source products and standards we assessed were quite feature-rich and highly flexible. However, these platforms are often not developed to be modular, and the adopter must accept "all or nothing." Because a larger product implies a larger attack surface, we were often required to provide our own minimalistic solutions.
At times some of the technologies we wanted to use were not designed in a modular fashion. A modular configuration would allow us to remove unused features in an effort to reduce the attack surface in keeping with the principle of "economy of mechanism". With the existing configuration, we were unable to find simple implementations and had to develop our own.
Another broader challenge is the fact that uniformity and predictability make maintaining networks manageable (a straightforward example is an organization that requires all users to use the same desktop computer configuration or email client). Uniformity makes maintenance easy, but it can also make attacking a network easy. As we develop this platform, we face the challenge that organizations might not understand the tradeoff of the easy approach for greater network security. System's administrators are security professionals and currently incentivized to provide stable and unchanging systems. Therefore, this research anticipates many organizational and cultural hurdles.
Wrapping Up and Looking Ahead
Dynamic defenses offer many promising solutions for protecting vulnerable systems against attack. With substantial investment in the development of dynamic defense resources, developers, researchers, and sysadmins need a common environment where solutions can be compared and tested for compatibility.
Our platform will offer measurable improvements in security posture for real networks and will also allow researchers to evaluate new technologies in a standard environment. In addition, our platform will allow researchers to classify moving target strategies while facilitating experimentation, prototyping, and collaboration.
We welcome your feedback on this research in the comments section below.
Additional Resources
Presentation at DHS Science and Technology Cyber Showcase 2016:
https://www.dhs.gov/sites/default/files/publications/R%26D%20Showcase%20and%20Technical%20Workshop.pdf
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedGet updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
