Watching Domains That Change DNS Servers Frequently
Hello, this is Leigh Metcalf of the CERT Network Situational Awareness (NetSA) Team. Timur Snoke and I have discovered some interesting results in our continuing examination of the public Domain Name System (DNS). Our work has been focusing on domains that change their name servers frequently.
In the DNS, a domain only exists once it has been registered with the TLD (top-level domain) registry and the name servers to which it is assigned are operational. Logically, the entity that registers the pairing of domain to name server and the entity that operates a name server are distinct, although they are often the same. A domain may be purchased from a registration authority, which may also host the name servers to which the name is assigned. Many times the resolution authority and the registration authority are one and the same. If they aren't the same, then the administrator of the domain must both provide updates to the zone file--to point to the correct name servers--and ensure that the servers operate correctly.
Changing name servers generally causes disruptions. Regardless of the authority structure, for stability and robustness, the standard configuration is to use multiple name servers but not to change name servers often. This is a feature that's often taken for granted by end-users in today's Internet since DNS operators have had such practice in the tricky handovers.
Using a public source of passively collected DNS resolutions, we were able to find a collection of domains that frequently changed name servers over a period of 3 months. A domain changing name servers once or twice during 3 months is likely not suspicious; such behavior is probably due to reasonable hosting and operational changes. In our analysis, we found over 2,400 domains that exhibited name server instability. Figure 1 displays the distribution of the number of times a domain changed its name server, ranging from 3 to 16 times.
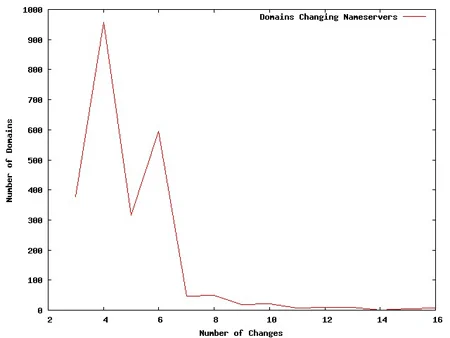
Figure 1: Distribution of the Number of Times Domains Changed Name Servers
Conceptually this is suspicious because only domains that try to hide need to be on the run, to stretch a metaphor, from name server to name server. We studied the various domains that exhibited this behavior, and our examination of the top offenders yielded domains exhibiting unsavory behavior such as hosting malware, pornography, unlicensed pharmacology sales, and hacked domains. The domains that changed name servers frequently were not necessarily malicious; however, all displayed some unsavory characteristic, and this behavior may foreshadow additional malicious behavior. In short, our study yielded a list of suspicious domains that should be examined or monitored.
A possible explanation for these changes in resolution name server and why such changes are linked to unsavory behavior is that changing name servers may be due to provider reassignment. If a domain provides unsavory content, it may constantly be forced to relocate by its providers. Although we have no visibility into such details, it's our best guess as to why this suspicious name server behavior is correlated with such unsavory types of domains.
Going forward, we can't determine if this practice will become more or less widespread. However, it's behavior that's occurring in the wild. Since there's a correlation between moving name servers and unsavory behavior, we suggest that people take similar measures to identify and watch such domains.
More By The Authors
More In CERT/CC Vulnerabilities
PUBLISHED IN
Get updates on our latest work.
Sign up to have the latest post sent to your inbox weekly.
Subscribe Get our RSS feedMore In CERT/CC Vulnerabilities
Get updates on our latest work.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Subscribe Get our RSS feed
